As Ethereum Layer 2 adoption accelerates, Arbitrum has emerged as one of the most dominant execution environments. Protocols are scaling with faster throughput, lower fees, and expanding user bases, but that growth introduces new challenges. This guide outlines the architectural assumptions, governance dependencies, and deployment patterns unique to Arbitrum, and offers practical guidance for developers and researchers working across the stack.
Understanding the Arbitrum Execution Environment
Arbitrum scales Ethereum through optimistic rollups, executing transactions off-chain and posting results back to Ethereum L1. Its design supports familiar Solidity tooling, but introduces unique behavior that organizations must validate in production.
Execution Architecture
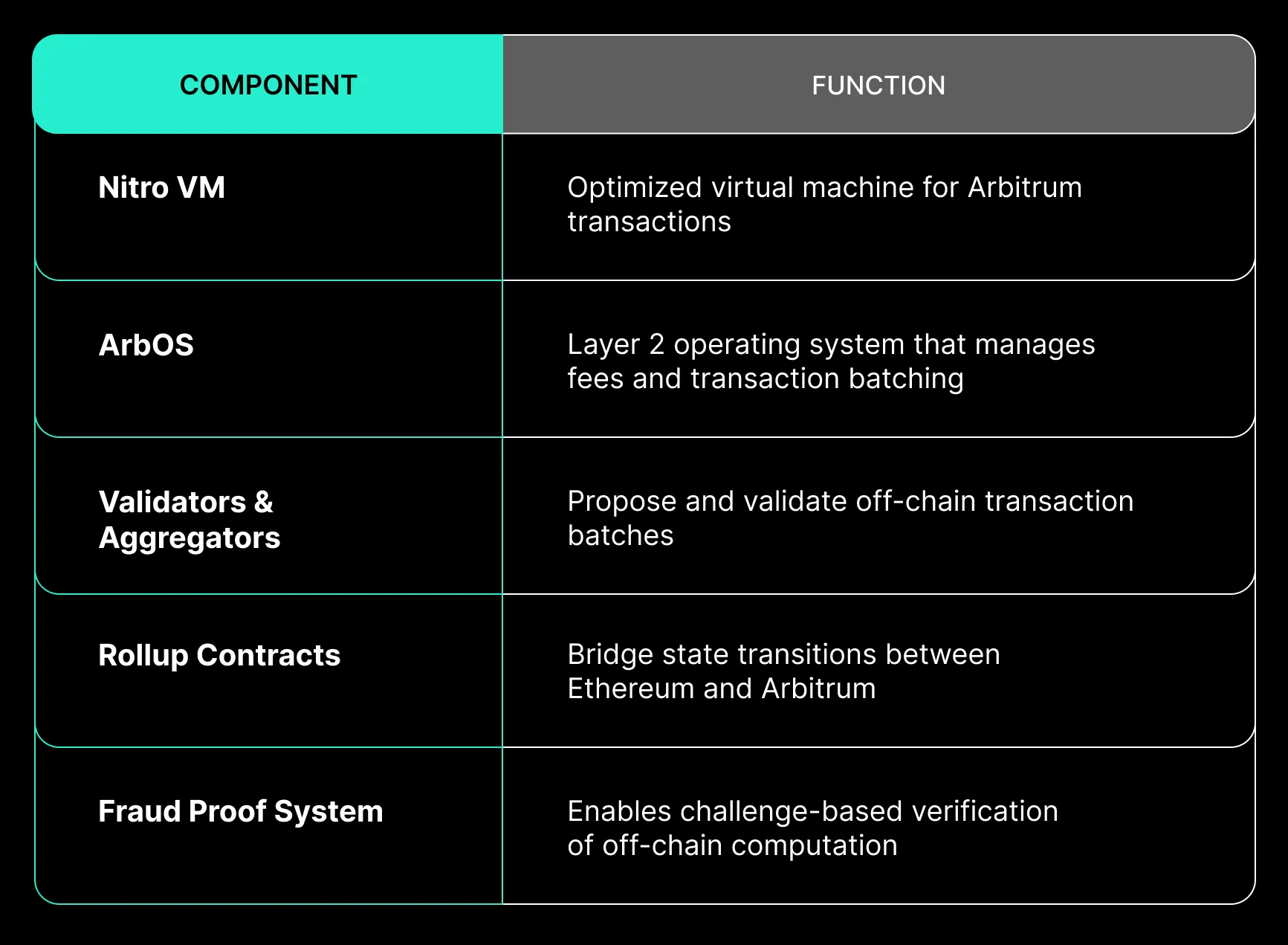
While computation happens off-chain, security is ultimately enforced by Ethereum. Finality depends on fraud proof windows, and developers must account for delayed final confirmation compared to mainnet L1 operations.
Infrastructure Risk and Operational Considerations
Sequencer Centralization
Arbitrum’s centralized sequencer introduces a critical dependency. Although mechanisms like the Delayed Inbox allow users to bypass the sequencer, few projects rely on these paths. Fallback readiness remains low in many production deployments.
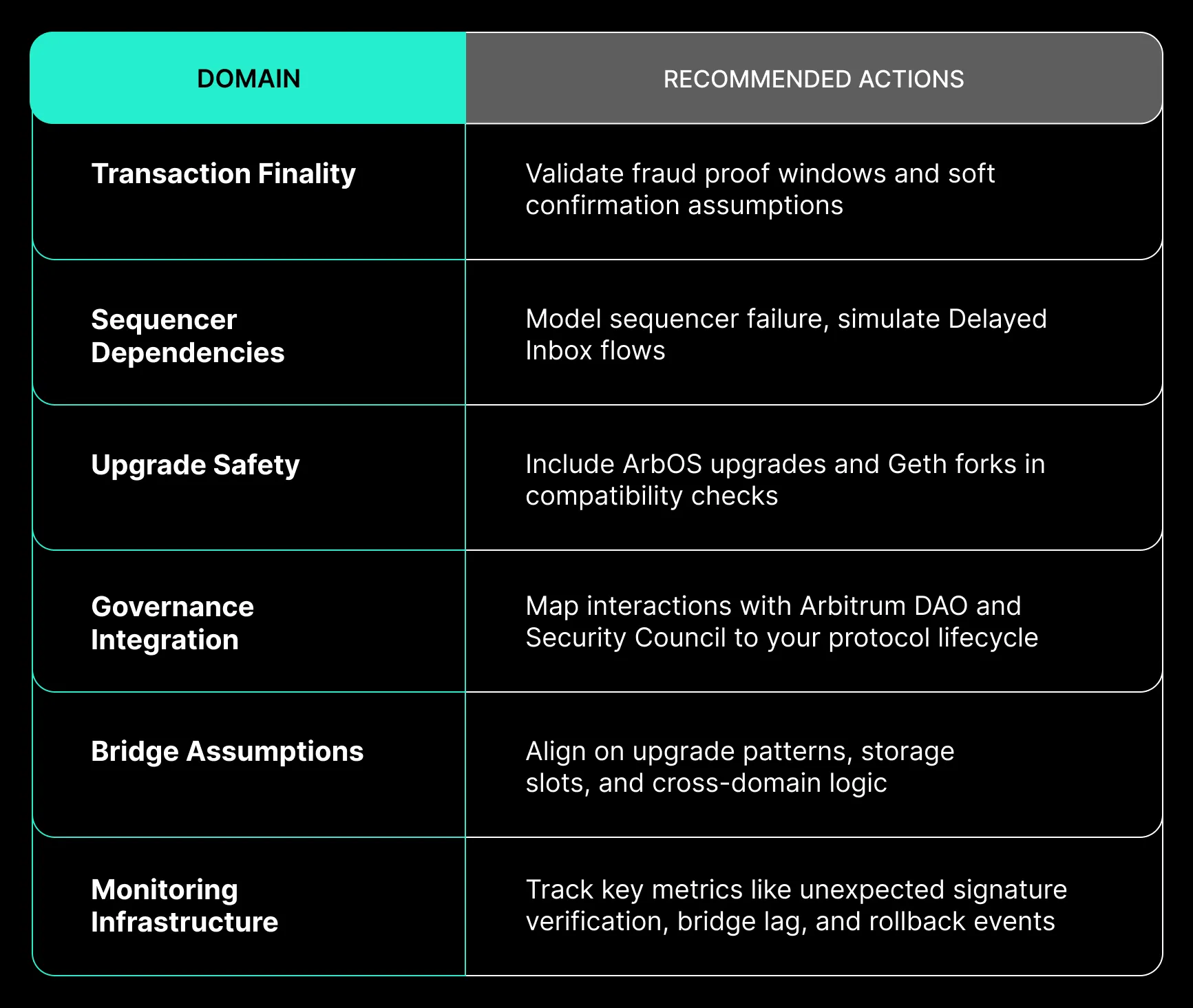
Recommendation: Assess what happens to your protocol under sequencer downtime. Test Delayed Inbox behavior and verify that funds cannot be trapped due to forced sequencing failures.
Bridge and Upgrade Behavior
Custom bridge logic, proxy patterns, and upgrade workflows can silently introduce consensus-breaking changes. Recent security incidents exposed risks in signature validation and consensus state transitions.
Recommendation: Conduct reviews that align bridge assumptions with contract upgrade behavior. Include ArbOS upgrades and Geth forks in threat modeling. Document storage layouts and execution invariants clearly.
Governance and Emergency Coordination
Security Council and DAO Escalations
Arbitrum features an emergency Security Council with powers to halt protocols, revoke permissions, or coordinate patch releases. These actors operate outside of DAO governance in specific windows.
Recommendation: Projects must define how DAO or Council actions influence their upgrade flow, proxy logic, or protocol pausing. Failing to model governance interactions can introduce legal or operational ambiguity during incidents.
Simulated Governance Response
Simulation of governance-based triggers improves resilience. Events like protocol freezes, multisig escalations, and temporary custodianship must be stress-tested.
Application Risk Areas
High-Frequency Systems (e.g., DEXs, Perps)
Arbitrum’s throughput allows for millisecond-level latency across orderbooks and AMM designs. However, the lack of guaranteed sequencing means developers must account for transaction reordering and stale state reads.
Mitigation: Adopt deterministic ordering where possible. Guard against stale read-modify-write operations. Validate sequencer slippage and enforce logical checkpoints on batch execution.
Cross-Chain Coordination
Bridged tokens, oracle price feeds, and validator attestations can introduce inconsistency. Asynchronous execution between chains must be handled carefully.
Mitigation: Confirm time-bounding, attestation freshness, and replay resistance across your bridge logic. Include fallback scenarios for oracle failure or validator downtime.
Security Checklist
Arbitrum Development Considerations
Arbitrum supports familiar tooling (Hardhat, Truffle, Remix) and libraries (ethers.js, web3.js). Its compatibility makes onboarding easy, but off-chain state and fee systems can behave differently from Ethereum.

How Spearbit Supports Secure Arbitrum Development
Spearbit works with infrastructure organizations, dApps, and governance participants to validate and secure Arbitrum-based deployments. Our capabilities include:
- Full-stack reviews of bridge logic, sequencer behavior, and Nitro VM assumptions
- Governance threat modeling across DAOs, councils, and protocol upgrades
- Architecture walkthroughs with ArbOS and custom validator configurations
- Research-driven bug bounty design to capture Arbitrum-specific vulnerabilities
- Incident command support to simulate live responses and escalation workflows
Ship with confidence on Arbitrum. Contact us to design a security program aligned with your infrastructure and governance model.




