Avalanche has matured into a modular blockchain platform that supports performance scaling and custom subnet deployments. Its architecture allows organizations to deploy independent execution environments with custom consensus parameters. That flexibility introduces coordination demands around validator behavior, economic alignment, governance paths, and infrastructure robustness. This guide presents the considerations that matter for developers building resilient systems on Avalanche.
Understanding Avalanche’s Modular Architecture
Avalanche operates with three foundational chains: the Exchange Chain (X Chain), the Platform Chain (P Chain), and the Contract Chain (C Chain). These provide core services such as asset transfer, stake coordination, and compatibility with the Ethereum Virtual Machine. On top of these foundations, custom subnets may be launched. Each subnet runs its own validator set and may adopt custom execution rules or governance structures.
Custom subnets offer sovereignty and throughput benefits. They also require organizations to take ownership of processes such as validator selection, governance design, upgrade coordination, and operational oversight. Subnets differ from monolithic chains in that each project must ensure its own integrity and resilience.
Validator Coordination and Economic Considerations
Validators contribute to network integrity by maintaining consensus on global chains while optionally validating subnets. Subnet validators must meet dual expectations: uphold primary chain requirements as well as subnet-level economic and availability goals.
To maintain stability, subnets require a diverse validator set, strong uptime, and incentive alignment. Smaller or loosely coordinated validator sets may introduce vulnerabilities such as transaction exclusion or periods of reduced throughput. Additionally, token models or reward schedules within subnets should align with expected behavior under load.
Governance and Upgrade Pathways
Subnet governance models vary. Some subnets use fixed validator sets. Others may use proposals or DAO-style voting mechanisms. These models determine how quickly software changes can be deployed and who controls execution boundaries.
Organizations designing governance should ensure clarity around rollback procedures, version compatibility, voting thresholds, decision latency, and quorum. Upgrade processes should offer observation windows and safe upgrade paths in case of unforeseen issues.
Bridge, Messaging, and Interoperability Assumptions
Cross-chain bridges and messaging systems are central to subnet functionality. Safe bridge design depends on validator honesty, correct signature aggregation, replay protection, and timely finality.
When subnets connect to external L1s or other subnets, they should enforce verification of source chain, timestamps, and message ordering. Where external bridges or validators are lightly audited, integrating fallback mechanisms or verification layers can strengthen trust.
Node Hardening and Infrastructure Discipline
Validator nodes form the backbone of Avalanche subnets. Infrastructure exposure through misconfigured nodes or insecure access opens attack surfaces. Best practices for node deployment include:
- Isolating signing keys via hardware security modules or remote signers
- Disabling RPC endpoints that allow unauthenticated access
- Enforcing encryption on peer-to-peer communication
- Monitoring node health, resource usage, and availability through external telemetry
Subnet stability depends not simply on consensus rules but also on consistent node operations. Interruptions from resource constraints or misconfiguration may impact throughput or consensus.
Subnet Governance and Incentive Alignment
Slashing policies are optional and subnet specific. Some networks enforce penalties for downtime or misbehavior. Others rely purely on reward incentives. Clear definitions of enforcement logic, dispute resolution, and recovery procedure are essential to maintain validator discipline.
Introducing active monitoring and transparent governance fosters alignment among validators. When validator misbehavior is visible and consequences are well defined, the likelihood of reliable participation increases.
State Management and Long-Term Data Strategy
Most subnets maintain local state over time. Without strategies for managing that state, systems may face storage inflation, degraded read performance, or costly synchronization operations.
Effective data strategies include snapshotting state regularly, employing efficient serialization, archiving old blocks, and establishing metrics for state growth. Custom virtual machines may demand bespoke solutions for persistent state or historical traceability.
Consensus Stability and Finality Under Load
Avalanche consensus achieves probabilistic finality. Finality is supported when a sufficient fraction of validators sample and agree on transaction acceptance. Formal studies indicate that when adversarial control surpasses certain thresholds, safety or finality may be affected under conditions of validator churn or network delay.
Builders should model failure conditions, validate assumptions about validator stake distribution, and anticipate what happens under latency or validator turnover.
Engineering Practices for Robust Deployment
To support stable and resilient Avalanche deployments, developers and infrastructure operators should:
- Harden node infrastructure and configure executable environments securely
- Establish slashing and reward mechanisms that promote desired validator behavior
- Monitor consensus metrics and observe deviations from expected finality or transaction inclusion
- Review bridge components thoroughly including cross-chain validation logic
- Define governance procedures that include version governance, upgrade paths, rollback plans, and applicable observation windows
- Use external monitoring to track uptime, latency, and transaction flow across RPC and peer networks
- Simulate edge cases using testnets or forked environments to validate behavior under stress
How Spearbit Assists Organizations on Avalanche
Spearbit offers security reviews that align with the modular and sovereign nature of Avalanche development. Our contributors deliver:
- Formal modeling of subnet consensus assumptions and validator coordination
- Infrastructure reviews for node security, signing isolation, upgrade control
- Audits of bridging logic with proof validation and message sequencing verification
- Governance flow assessment and upgrade path planning
- Operational readiness engagement including incident response preparation and behavior simulation under adversarial conditions
We support subnet architects, protocol engineers, and application teams seeking dependable deployment and long-term operational clarity.
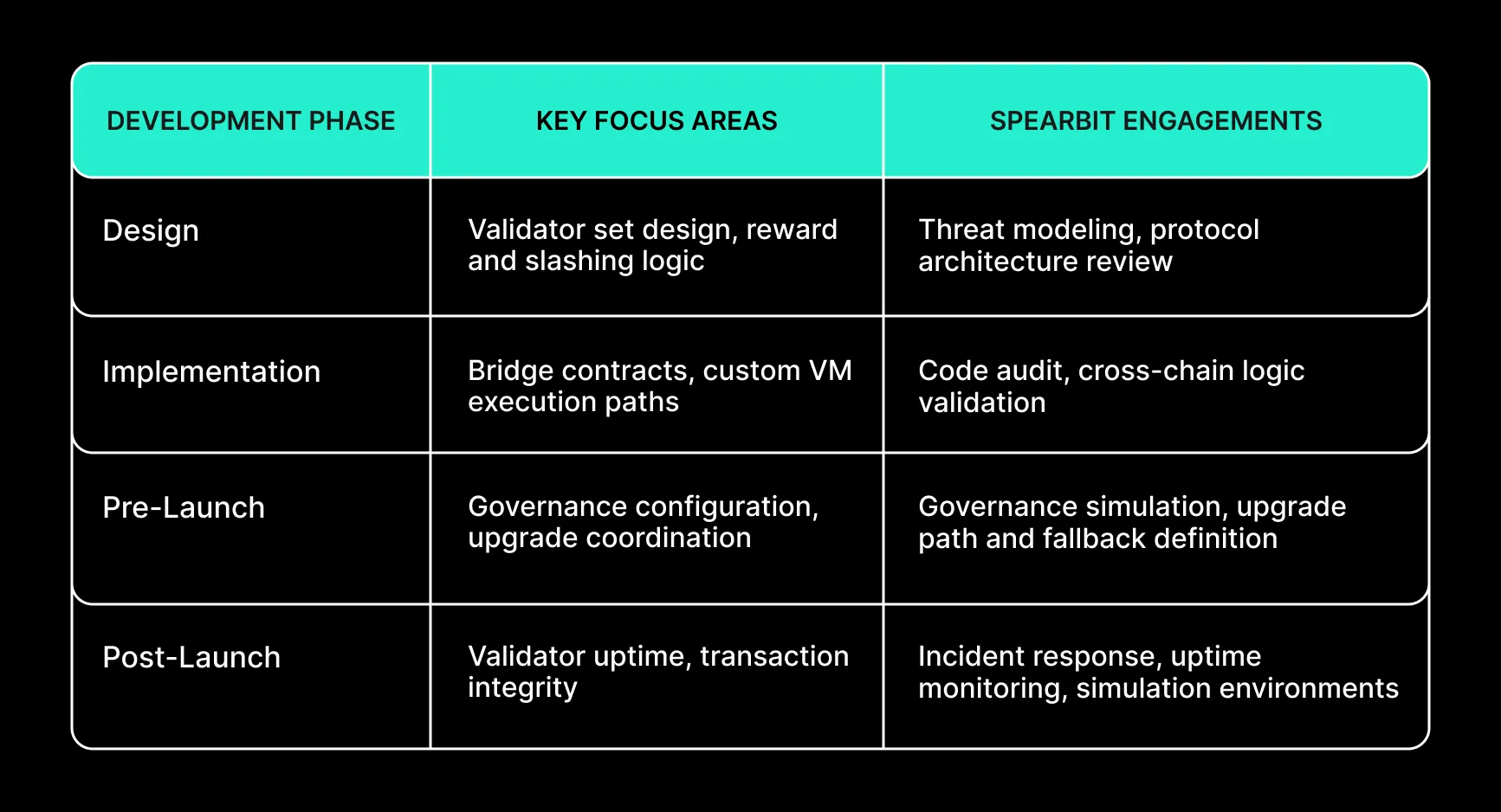
Security Coverage Across Avalanche Development Lifecycle
Final Reflection
Avalanche’s flexibility offers powerful opportunities for innovation across DeFi, gaming, supply chain, and enterprise systems. That flexibility demands commensurate diligence in consensus design, validator coordination, governance discipline, and infrastructure integrity. Organizations that build with those dimensions in view not only minimize unexpected behavior but also strengthen ecosystem trust.
For support tailoring a secure deployment on Avalanche, reach out to us. Our network of world renowned researchers is ready to collaborate with your team across design, validation, and ongoing resilience.