BNB Chain is a widely adopted smart contract platform. Low fees, rapid finality, and an expanding dApp ecosystem make it attractive for developers, but also a high-value target for attackers. Secure engineering practices are essential from the outset.
Here are 15 high-priority recommendations for BNB Chain development. These draw on common vulnerability patterns, observed exploits, and practical defenses. They also integrate Cantina’s specialized capabilities in high-signal reviews, incident command, competitive audits, and community-led bug bounties.
1. Enforce Nonce-based Signature Validation
Avoid replayable off-chain signatures by adding nonces and validating them strictly
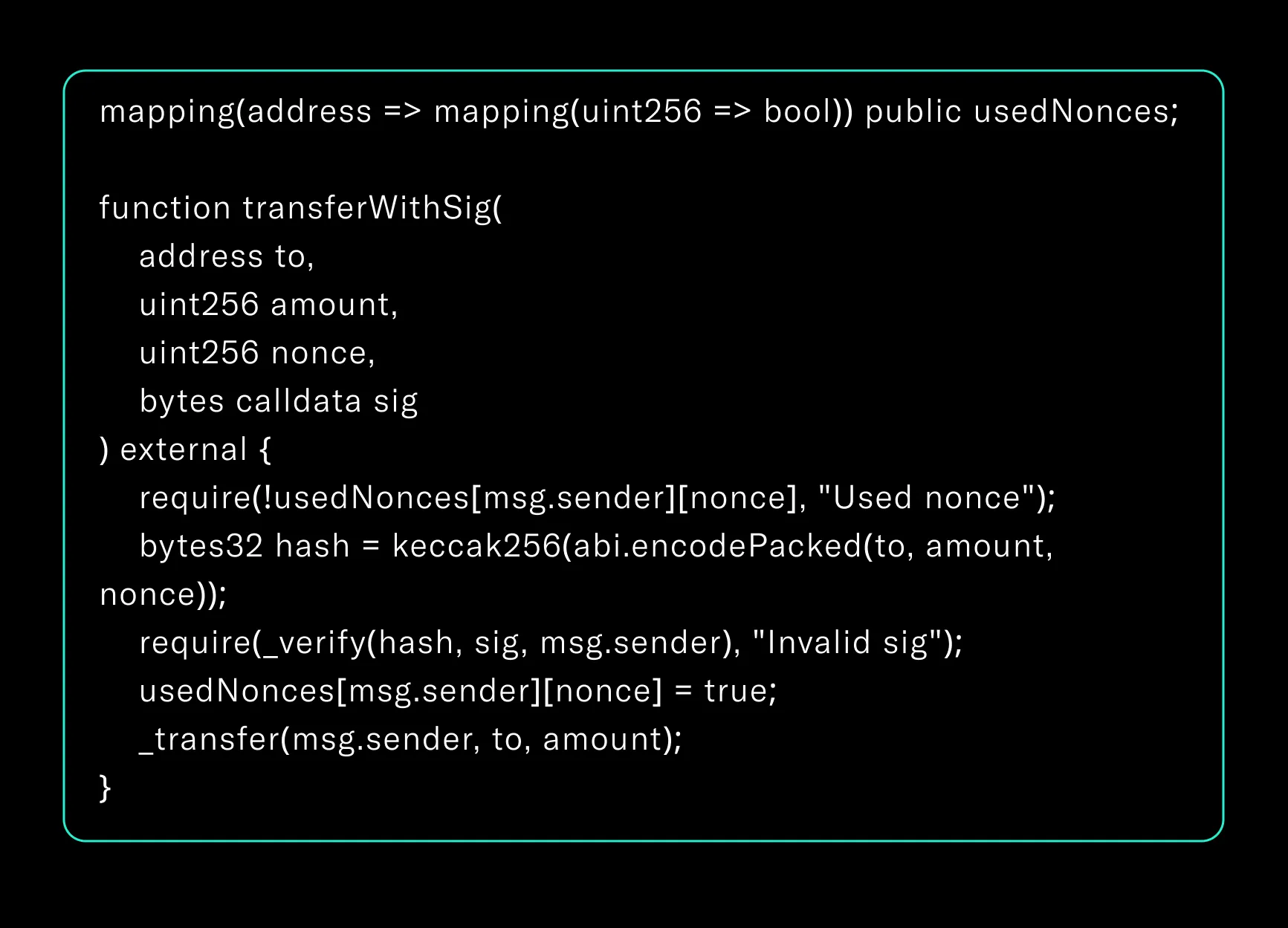
This simple addition prevents transaction replays across networks or within the same chain.
2. Always Apply Checks-Effects-Interactions
State changes must always precede external calls. This pattern minimizes reentrancy risk:
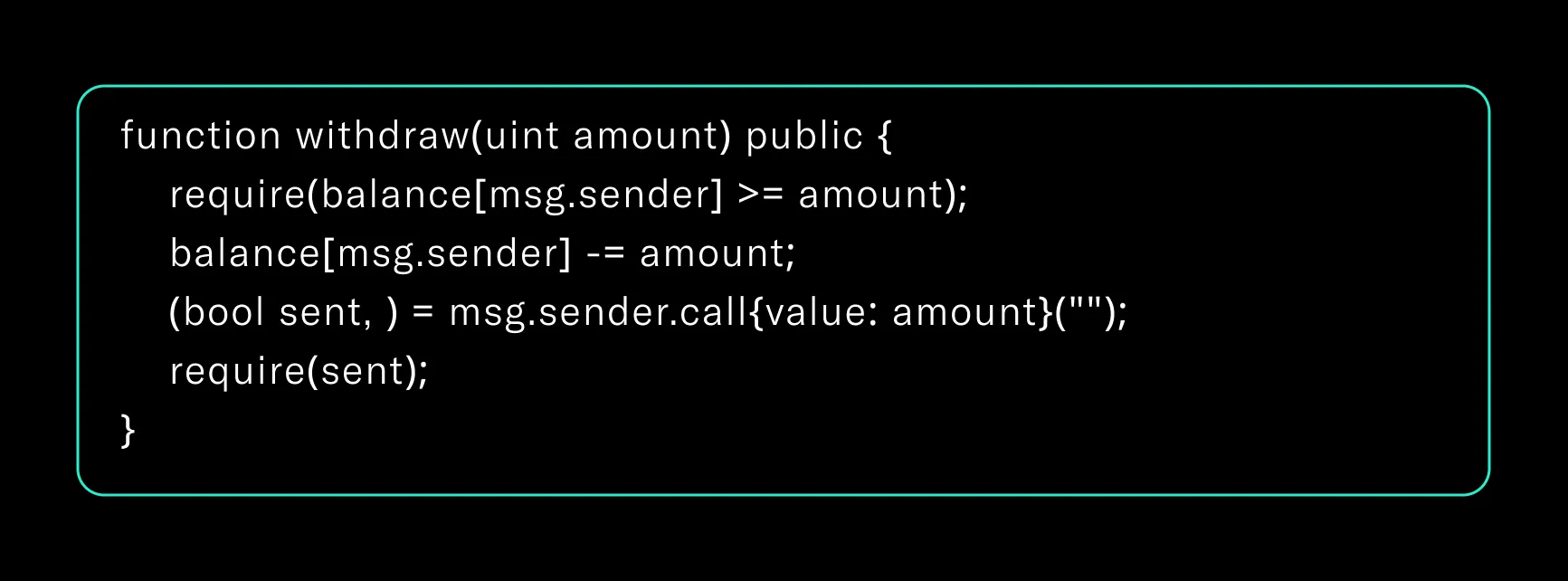
Cantina reviewers consistently flag reversed order logic in engagements—even minor violations can open exploit paths.
3. Avoid On-chain Oracles With Synchronous Exposure
Directly reading DEX pair reserves (e.g., Uniswap, PancakeSwap) introduces attack surfaces.
Replace synchronous reads with TWAPs or decentralized oracle networks for pricing.
4. Limit Upgrade Complexity
Use established proxy patterns and avoid inline custom modifications. Insert storage gaps:

Proxies remain a common vector for subtle logic corruption. Cantina researchers validate storage layout integrity during upgrade audits.
5. Restrict Visibility and Enforce Role Control
Explicitly define external, internal, public access. Rely on onlyOwner or role-based modifiers where appropriate:

Visibility defaults and missing role enforcement continue to be one of the top root causes in critical incidents.
6. Use Commit-Reveal for Front-Running Resistance
For auctions, votes, and predictions, conceal sensitive input:
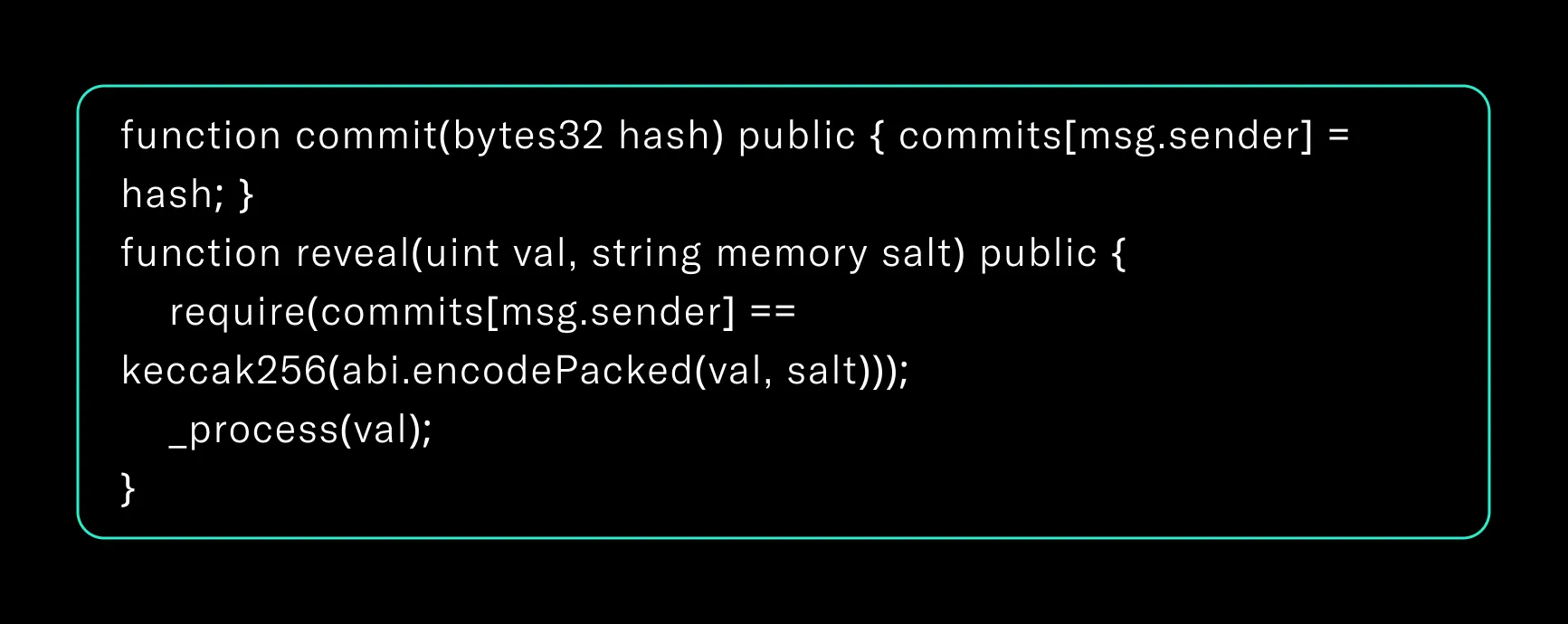
Fair sequencing services can supplement this design where available.
7. Create and Maintain Incident Command Protocols
Define incident response roles, multisig controls, and emergency pause functions. Cantina offers on-demand incident command services to triage and mitigate during active exploits.
8. Integrate High-Signal Security Reviews
Routine, targeted security reviews by expert researchers are foundational. Cantina aligns reviewers with domain-specific experience—DeFi, NFTs, L2s, infrastructure—and supports both solo and modular team configurations.
9. Host Competitive Reviews and Bug Bounties
Competitions uncover edge cases often missed in standard reviews. Cantina supports competitive engagements and ongoing bounty programs with structured triage.
10. Sanitize and Validate All External Inputs

Guard conditions on inputs reduce unexpected edge behavior. This includes function parameters, calldata, msg.value, and token amounts.
11. Handle Fallbacks and Bounces Properly
Always define receive() and fallback() explicitly. Avoid assuming all value sends will succeed. For systems with internal messaging (cross-chain, etc.), explicitly parse and verify bounced messages.
12. Test Cold Paths and Asynchronous States
Complex flows require simulation beyond unit tests. Use Foundry or Hardhat for concurrency testing. Cantina incorporates cold path fuzzing in its standard review flow.
13. Review Token Standard Assumptions
Ensure compatibility and compliance with token standards. Do not assume all ERC20s return true on transfer() or approve().
14. Validate External Calls and Fallback Paths
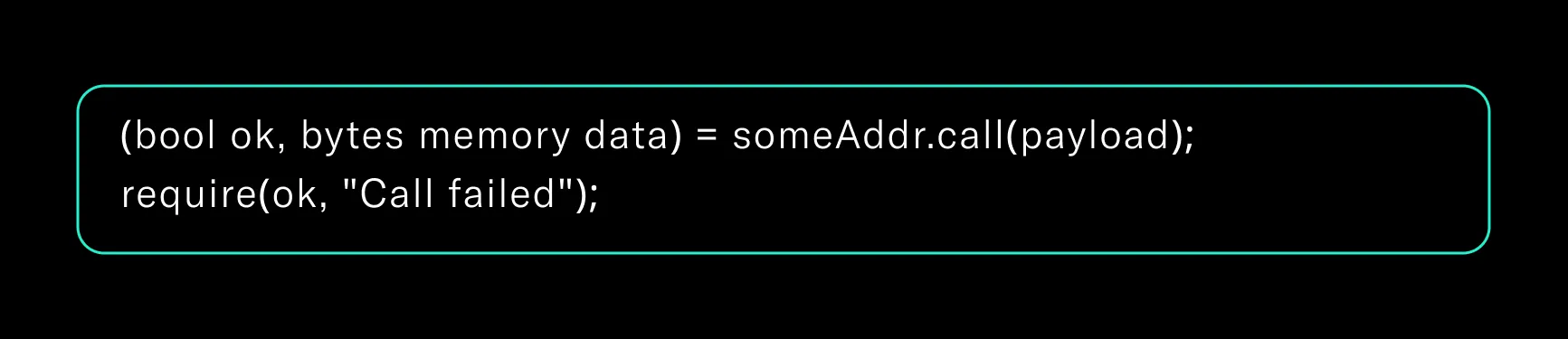
Avoid unchecked low-level calls. Validate execution paths and fallback behaviors to prevent silent failures.
15. Formalize Pre-Launch and Post-Launch Security Checklists
Halt dev prior to review, document unchecked blocks, compile cleanly, annotate assumptions. Post-launch, set up monitoring, run continuous reviews, and deploy automated alerts.
BNB Chain developers can build more resilient systems by operationalizing these practices. Cantina provides modular review formats, high-signal researcher access, and full-scope security coverage - from first commit to incident command.
Ready to secure your next deployment? Let’s talk, contact us.




