Welcome to Cantina
If you are new here, welcome.
Cantina exists for a simple reason: when value, reputation, and public trust move onchain, security stops being a department and becomes infrastructure. It has to be real. It has to be measurable. And it has to hold up in the moments that matter most, including the ones nobody can schedule.
For years, Cantina has been known for bringing exceptional security researchers, high signal processes, and rigorous security programs to the most complex & critical code in Web3. That work still matters deeply, and we are proud of it. But 2025 changed the shape of the problem we are all solving, and it changed what the best teams started asking for.
This is a short story about that change. It is also a look back at what we built together, and a statement of what we are building next.
2025 Security by the Numbers
Before we talk about the shift, it helps to ground it in what 2025 looked like in practice.
In 2025, across Cantina and Spearbit:
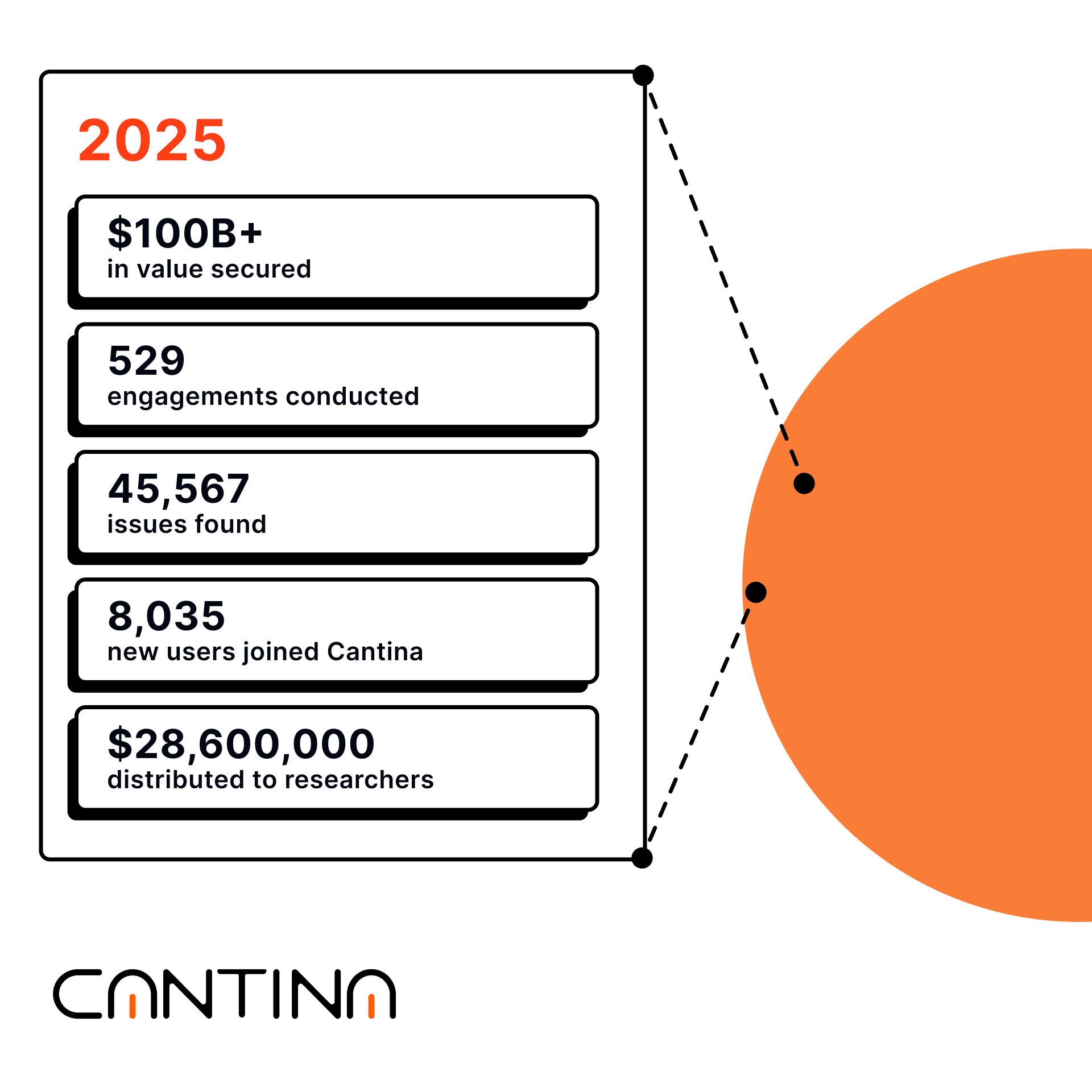
Those numbers reflect a year of sustained execution across security reviews, competitions, and bug bounty programs, and they also explain why our direction expanded. When the volume and velocity of risk rises, assurance has to extend beyond pre launch work into operational readiness and response.
The year the threat model caught up to everyone
The digital landscape in 2025 was shaped by an unmistakable surge in cyber crime, and by a convergence that many teams had been warning about for a long time.
Web3 was hit hard. In the first half of 2025 alone, protocols collectively lost more than $2.3 billion to hacks and exploits. A large share of those losses traced back to access control failures, the kinds of breakdowns that are rarely just “a bug” in isolation. They are failures of systems: key management, privilege boundaries, operational process, and decision making under pressure.
Web2 was not a separate universe. It kept teaching the same lessons at painful scale. Social engineering, misconfigured infrastructure, and supply chain compromise continued to create breaches that were not defeated by better code alone.
Identity became the new perimeter, and it did so in a way that is easy to underestimate. Organizations now host vastly more non human identities than human ones, as bots and AI agents proliferate across workflows. When credentials, access paths, and approval flows become the battlefield, you cannot treat security as a single moment before launch.
At the same time, the incentives of attackers changed. AI made the marginal cost of convincing phishing, tailored social engineering, and automated exploitation much lower. It also made iteration faster. In practical terms, it compressed the time teams have to notice an attack, understand it, and respond before damage becomes irreversible.
All of this happened while regulations accelerated across jurisdictions. Institutions that were already cautious became more exacting. If you want serious capital, serious partnerships, or serious distribution in 2026, you need more than the right narrative. You need evidence.
That is the core reason our direction changed.
What we built before 2025, and why it still matters
Before we talk about the shift, it is worth naming what came before it, because it is still the foundation.
Cantina’s earlier years were defined by raising standards on point in time assurance. We built a platform where leading researchers can do their best work, where organizations can run security programs that scale, and where “security investment” produces outcomes that a team can stand behind.
That meant security audits that treat systems as adversarial environments rather than static codebases. It meant competitions designed to pressure test surface area that traditional approaches miss. It meant bug bounties that reward real expertise and prioritize signal, supported by serious triage and program design.
Those are not legacy tools. They are still essential. But 2025 made something impossible to ignore.
Even the best pre deployment program cannot fully cover the risk created by compromised keys, compromised vendors, compromised signers, and crisis decisions made in minutes with incomplete information. The biggest failures were increasingly about operations.
So we did not walk away from what made Cantina valuable. We expanded it into something more complete.
2025 at Cantina: the work that defined the year
When we look back on 2025, what we remember most is not one program or one announcement. It is the feeling that the industry started treating security as a first order design constraint, and that the strongest teams began building in public ways that others could learn from.
We saw that in major protocol upgrades, where the surface area is so large that security has to be treated as a coordinated ecosystem effort. We saw it in modular architectures, where extensibility creates power and risk at the same time. We saw it in cross chain infrastructure, where one integration can become a multiplier of impact. We saw it in institutional flows, where “good enough” is not a category.
Some highlights from the year reflect those themes.
PancakeSwap entered 2025 with a clear ambition: evolve from a successful multichain exchange into core liquidity infrastructure that can support modern capital flows and higher expectations around reliability. PancakeSwap Infinity pushed modularity further, with hooks and customizable pool designs that expand what teams can build on top. To match that ambition, PancakeSwap partnered with Cantina on a $1 million USDC bug bounty to invite the global security community to pressure test Infinity’s architecture in production conditions. The message was clear: when the surface area grows, security has to scale with it, continuously.
Coinbase represented another version of responsibility at scale. For millions of people and thousands of organizations, Coinbase is a default entry point into Web3, across wallets, custody, Base, and onchain products. In 2025, Coinbase and Cantina collaborated on an onchain security program that reflects what it means to be that entry point. It included a 5 million USDC bug bounty focused on Coinbase’s onchain products and Base smart contracts, structured smart contract audits, a targeted competition, public guidance for researchers, and a visible role in shaping Web3SOC. The underlying intent was straightforward: when trust is the product, security work has to be verifiable and ongoing.
At the protocol layer, Ethereum’s 2025 security story stood out for its scale. Pectra was the next major upgrade after Dencun, and it touched enough of the client and specification surface that it demanded a program designed for that reality. In collaboration with Ethereum Foundation protocol contributors and major client organizations, Cantina ran a $2 million Pectra Security Competition, plus a client layer security review spanning twelve repositories across execution clients, consensus clients, and protocol specs. Security at that scale is not only about finding vulnerabilities. It is about building repeatable coordination patterns for the infrastructure the entire space depends on.
Across DeFi, we saw lending systems mature in ways that institutions could recognize, but only because teams paired architectural ambition with real security posture.
Morpho established itself as a reference lending backend for teams that need institutional grade infrastructure without giving up composability. That role was reinforced by an ongoing security program centered on an ongoing 2.5 million bug bounty and dedicated competitions around critical vault components.
Euler spent 2025 doing something that is both difficult and important: making a highly flexible lending design something that security teams, DAOs, and institutions can reason about. Euler v2 pushed modularity to the edge, while keeping risk local to clearly defined surfaces. That required a security program to match, including a 7.5 million USDC plus token incentive bug bounty, a large scale competition, and targeted reviews of core components.
Uniswap showed what end to end security looks like when a protocol becomes programmable liquidity infrastructure. On the product side, Uniswap advanced v4 Hooks, new execution environments, smart wallet workflows, and institutional integrations. On the security side, Uniswap Labs hosts the largest bug bounty in DeFi on Cantina at 15.5 million USDC, expanded scope, ran targeted audits, and acted as a core Web3SOC collaborator. The result is a benchmark that other teams can learn from, not because it is loud, but because it is consistent.
LI.FI reflected the multi chain shift. As liquidity began moving through shared aggregation layers, more organizations treated connectivity as core infrastructure. LI.FI sits at the center of that world, connecting applications to liquidity across many chains, bridges, exchanges, and solver networks through a single policy aware integration. Together, LI.FI and Cantina paired growth with a deliberate security program that included deep security reviews, a large open competition, and a one million dollar bug bounty focused on the contracts that move value for users and partners.
We also saw the next frontier taking shape with EigenCloud. In 2025, EigenCloud moved from vision to deployed infrastructure, introducing a verifiable cloud for Web3 with containerized workloads, hardware acceleration, and API access backed by cryptoeconomic guarantees rather than blind trust. EigenAI and EigenCompute made verifiable inference and verifiable offchain execution real for developers. That matters because it points to the next version of the trust problem: how we secure systems that act, not just systems that execute.
Across all of these efforts, a pattern emerged. The most serious teams were not asking “did you do security.” They were asking “can you operate securely when something goes wrong.”
That is the shift.
The moment we knew we had to build beyond point in time
There is a particular feeling you get when you read enough incident reports. At first, each one looks like a unique failure. Over time, you see the repetition. Then you see what is missing.
In 2025, the missing layer was operational continuity.
Competitions, audits, and bounties remain critical, but they are not a substitute for being ready in real time. They cannot guarantee that signers will not be targeted. They cannot guarantee a vendor will not be compromised. They cannot guarantee that a team will make the right call under stress, with incomplete information, while attackers are moving funds across chains.
The strongest organizations started building security programs that look more like an operating system than a one time event. They needed a way to map risk across dependencies, align governance and authority, rehearse response, monitor continuously, and recover with discipline.
That is why we built Managed Detection and Response for Web3.
Managed Detection and Response, built for how incidents actually happen
Cantina MDR exists because modern incidents do not respect the boundaries between onchain and offchain, technical and organizational, code and governance.
MDR is built as five layers that evolve with your organization.
We start by understanding what matters most in your operations. We map dependencies, identify critical assets, and surface blind spots so the team is not guessing about priorities when stress hits.
Then we translate that understanding into structure. We build incident response playbooks that span technical, legal, and governance realities. We align multisig processes, escalation paths, approvals, and access control with the way decisions actually have to be made.
After that, we stress test. Tabletop exercises and simulations are not theater. They are a way to build muscle memory and expose mismatches between process and reality. We simulate exploits, phishing attempts, multisig failures, and contagion scenarios because those are the situations that decide outcomes.
Signal is the continuous layer. MDR provides 24 by 7 monitoring with a less than 15 minute SLA for mission critical events, plus logged actions that support compliance and audit readiness. The goal is not noise. The goal is decision relevant information, fast.
Shield is where response becomes real. Rapid containment, root cause analysis, timeline reconstruction, attacker profiling, and recovery recommendations. The point is to respond quickly, and also to learn in ways that make the next incident less likely and less damaging.
If you are building in 2026, this layer is becoming table stakes. It is not a replacement for good engineering. It is what allows good engineering to survive contact with the real world.
Web3SOC: a shared language for institutional trust
At the same time, another gap became obvious in 2025.
Institutions, and increasingly sophisticated ecosystem partners, were running into the same friction repeatedly. Due diligence was fragmented. Every evaluation started from scratch. Even when a protocol was doing the right work, it was hard to communicate maturity in a way that boards, risk teams, and compliance stakeholders could use.
Web3SOC was built to solve that.
It defines what it means to be institutional grade by scoring organizations across four core areas: operational maturity, financial resilience, security posture, and regulatory readiness. It produces classifications from Enterprise to Nascent, with transparent breakdowns that institutions can compare and organizations can improve against.
For institutions, it creates a standardized due diligence tool. For organizations, it creates a structured path to institutional adoption that is clearer than vague promises and more actionable than generic questionnaires.
In practical terms, Web3SOC is the connective tissue between what builders do and what institutions need to understand.
Why We Are Building AI Security
We’re also building a new AI security tool, and the interest has been immediate. AI is accelerating both discovery and exploitation, which means the gap between disclosure and remediation increasingly decides outcomes. Our approach is to reason over scope and code, test exploit hypotheses, and only surface a report when the impact is defensible.
If you're curios how the AI security tool works, the waitlist is open.
A note for newcomers, and why this feels personal
If you are reading this as someone just discovering Cantina, you might wonder why we are spending time talking about sentiment and direction rather than only products and programs.
The honest answer is that security work is built on trust, and trust is built over time.
The best parts of 2025 were not just the size of programs or the names involved. They were the moments when teams made hard decisions in the open. The moments when researchers pushed on systems that matter and were treated as partners rather than adversaries. The moments when organizations invested in readiness not because it looked good, but because it was the right thing to do for users and for the ecosystem.
Those moments accumulate. They create culture. They create standards. They create the future.
Cantina is grateful to be part of that story, and we do not take it lightly.
Getting ready for 2026
As we enter 2026, we see three forces tightening at the same time.
Attackers are faster and more automated, and identity is increasingly the battlefield. Regulations and institutional expectations are raising the bar for resilience, reporting, and evidence. The architecture of Web3 continues to expand across chains, dependencies, and offchain systems, which means incidents are more likely to propagate and harder to contain.
We also see something encouraging.
The best teams are building security as a capability, not a milestone. They are making their systems easier to reason about. They are adopting shared language. They are running programs that combine prevention and preparedness. They are treating operations as part of the product.
Cantina’s direction is to support that future.
We will keep raising the standard for audits, competitions, and bounties, because high signal pre deployment work remains essential. We will expand the operational layer through MDR and AI, because response readiness is now inseparable from security. We will keep building Web3SOC, because institutional adoption requires a common language and comparable evidence.
The goal is simple: safeguard everything that matters, and help the organizations building the next era of finance operate with confidence.
Closing
If 2025 was the year the threat model caught up to everyone, 2026 can be the year we build systems that hold.
If you are a builder scaling a protocol, shipping an upgrade, or expanding across chains, we would like to help you turn security from a moment into continuity.
If you are an institution evaluating onchain exposure, we would like to help you replace fragmented diligence with structured evidence.
And if you are simply new here and trying to understand what Cantina stands for, we hope this makes it clear.
We are here to help the best teams build things that deserve to last. Contact us, we'll find the path to security and institutional readiness, together.




