Detection is often mistaken for protection. Alerts can signal the presence of a threat, but they do not execute a response. What happens next, within the first few minutes, determines whether the organization maintains control or suffers loss.
These situations are rarely caused by unknown vulnerabilities. The outcome typically reflects poor coordination, undefined ownership, and fragmented internal response.
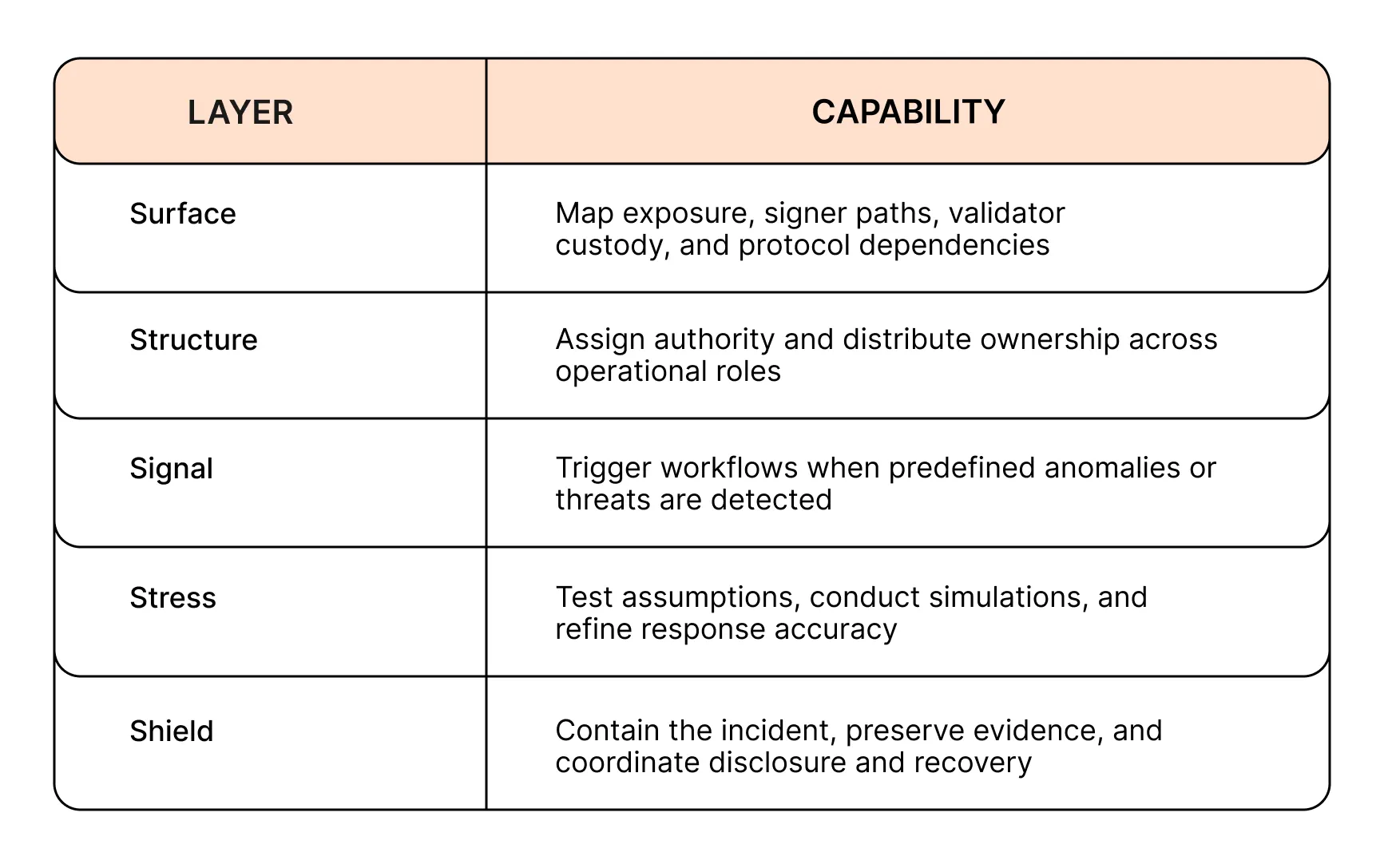
Incident Response was built to close that gap. It gives organizations the structure to detect, escalate, and contain incidents before damage spreads.
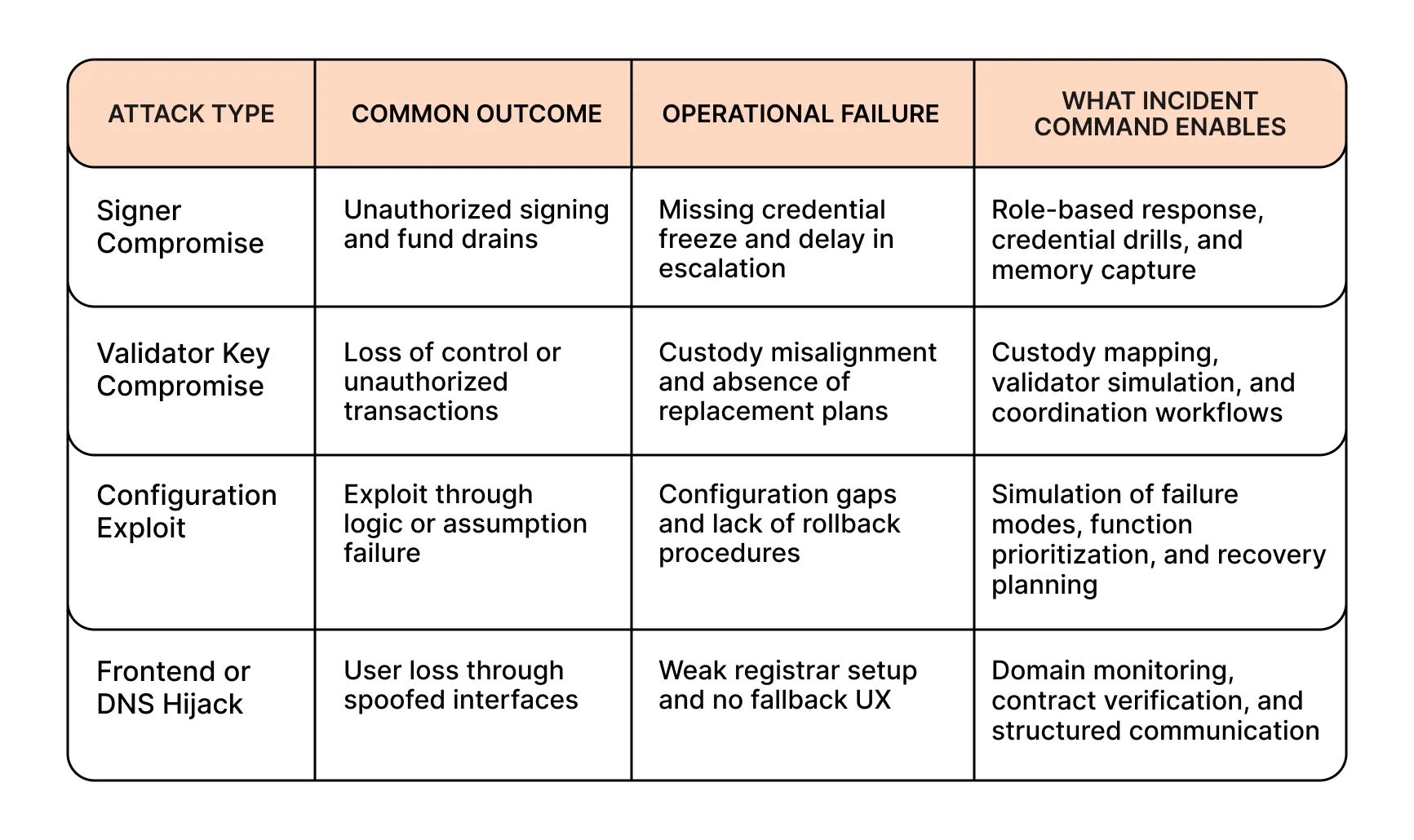
The following breakdown highlights 4 common Web3 attack vectors and shows how Incident Response changes what happens next, from first signal to full containment.
Who This Is For
Relevant for leaders overseeing security, engineering, legal, or governance functions within institutional and high-value Web3 organizations.
Applies to any organization managing protocol infrastructure, custody, or capital where the first 15 minutes of an incident remain undefined. Without clearly assigned ownership and executable plans, operational risk compounds.
These attack types reflect recurring threat models surfaced across protocol reviews and simulations. Incident Response translates those models into structured, testable response plans.
Summary
These patterns are drawn from real incidents and reflect threat models commonly encountered during Cantina-led reviews and simulations.
Attack Type 1: Signer and Credential Compromise
During simulations, signer compromise remains one of the most common and destructive entry points. Malicious links, phishing payloads, or exposed credentials often lead to unauthorized signing within seconds. When response is not clearly owned or rehearsed, containment fails and funds move before intervention begins.
Incident Response addresses this by clarifying authority, hardening credential paths, and running live phishing simulations to validate readiness across roles.
Prevention and Execution with Incident Response

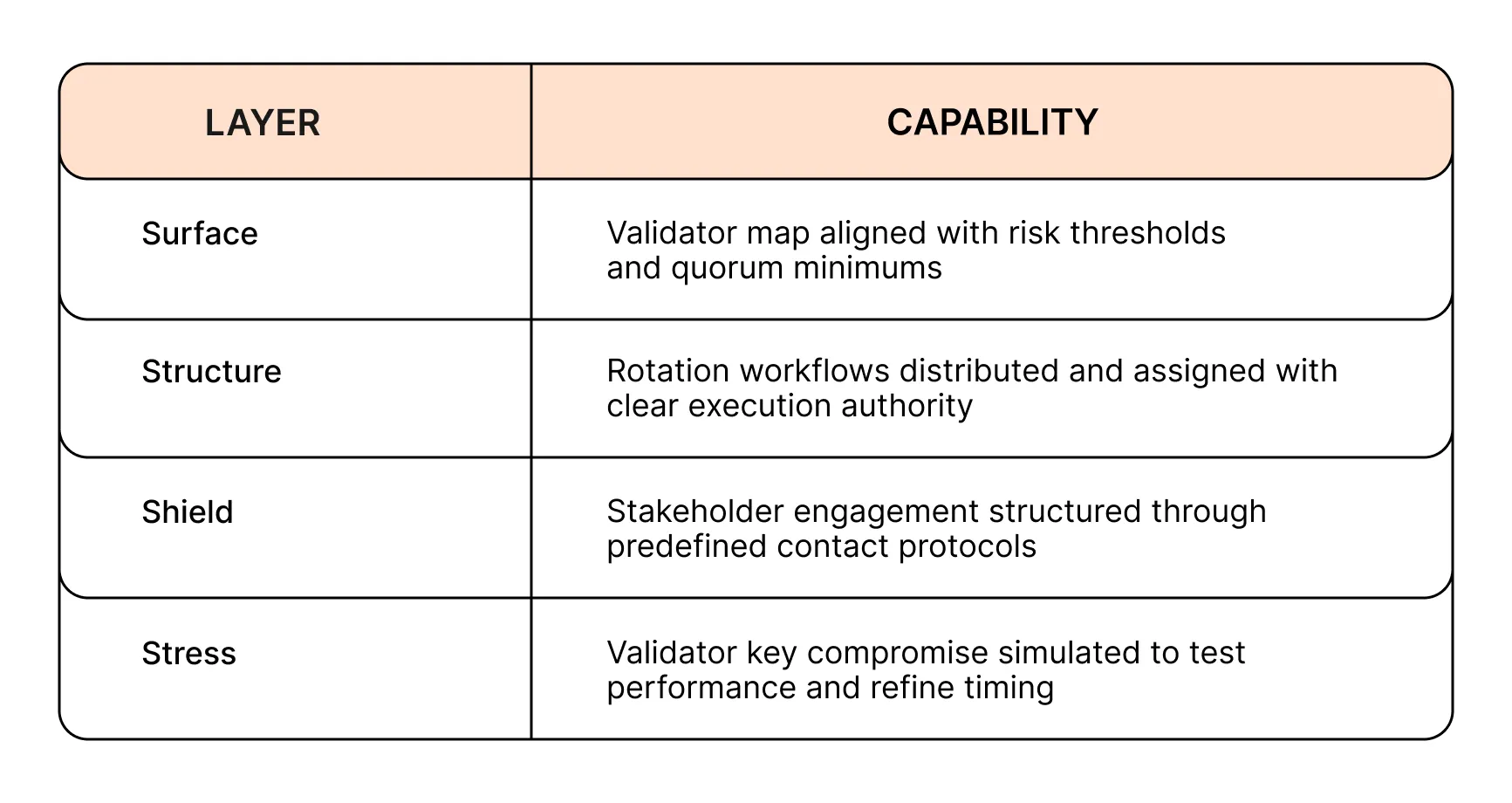
Attack Type 2: Validator and Key Compromise
Validator custody often evolves without structured oversight. Quorum configurations change over time, leaving organizations unsure who owns rotation procedures or what should happen if validator access is lost. Even with monitoring in place, a lack of coordination between internal and external stakeholders can block recovery.
Incident Response introduces validator mapping, recovery planning, and structured communication workflows. These elements are tested in simulation to ensure execution is possible under real conditions.
Prevention and Execution with Incident Response
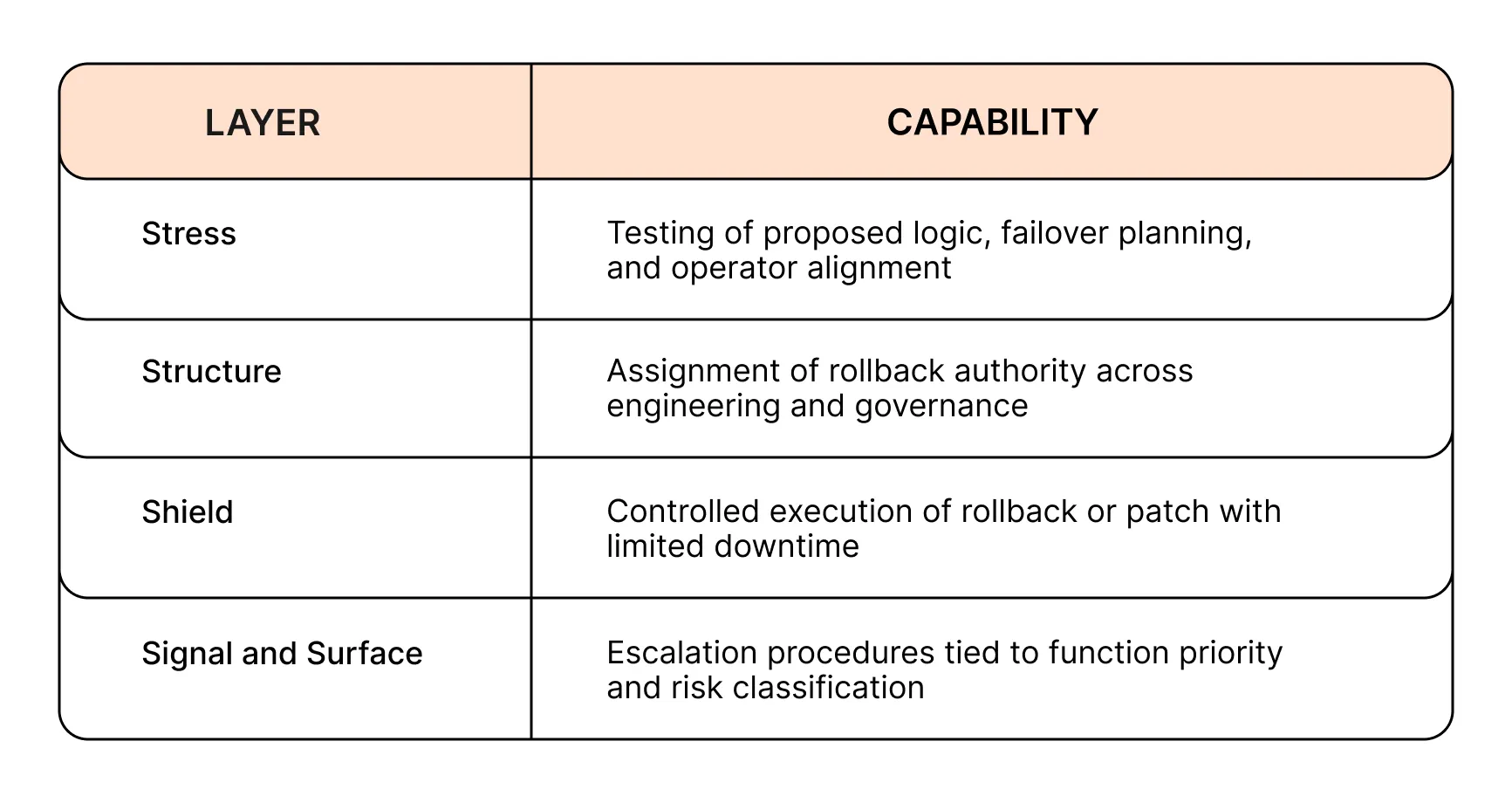
Attack Type 3: Configuration-Based Exploits
Configuration and logic failures often stem from assumptions that appear valid in review but break under operational pressure. When function priority is unclear and rollback paths are undefined, response teams often debate actions in real time, delaying intervention and increasing exposure.
Incident Response addresses these gaps by tying deployment controls to containment plans and validating those plans under simulated pressure.
Prevention and Execution with Incident Response
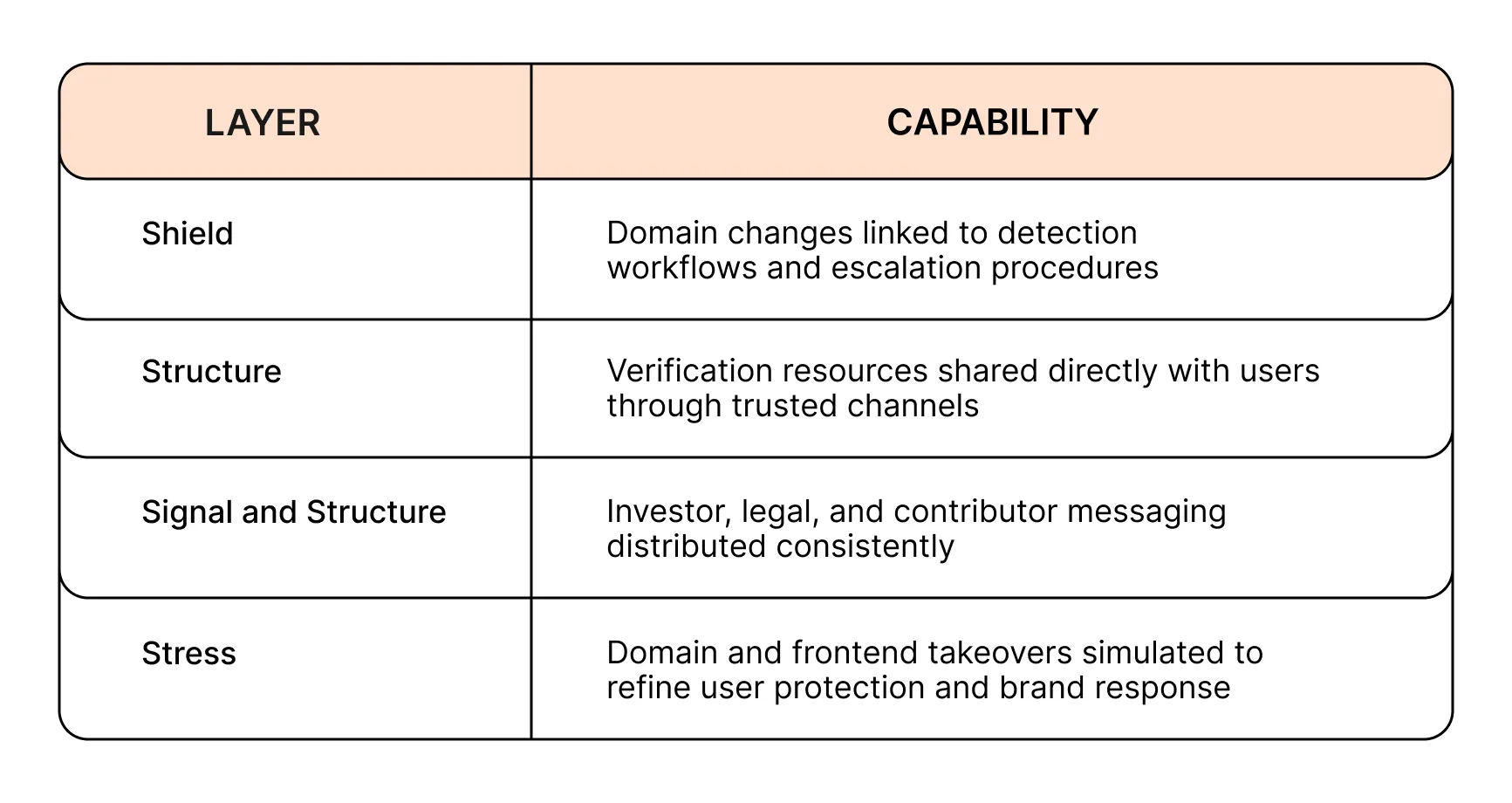
Attack Type 4: Frontend or DNS Hijack
Domain infrastructure remains one of the most overlooked surfaces in protocol security. Registrar misconfiguration, expired protections, or weak fallback planning can lead to user-facing compromise. When this happens, organizations often lack verified messaging flows, leaving users to interact with spoofed interfaces and lose funds.
Incident Response addresses these risks with DNS monitoring, fallback contract verification, and predefined communication workflows.
Prevention and Execution with Incident Response
What Connects These Failures
In every case described above, the initial detection occurred. The problem was not a lack of signal, but the inability to act.
Incident Response exists to solve for that failure pattern.
Why Leading Organizations Adopt Incident Response
Organizations using Incident Response are not theorizing about response. They are executing simulations, coordinating across engineering, legal, and governance, and preparing for known threats through structured rehearsal.
“Incident Response allows us to operate without hesitation. With Cantina’s preparation and rapid response capabilities, we can push boundaries with confidence.”
— Aionex
Begin With a Readiness Review
Cantina is onboarding a limited number of organizations into Incident Response. Each implementation begins with a readiness assessment, followed by role alignment, infrastructure mapping, and a live simulation.
Schedule a readiness review and understand how the organization will perform during its first critical minutes.




