As smart contract logic becomes increasingly robust, the cybersecurity attention in Web3 is shifting toward a less visible but equally critical layer—developer infrastructure and software supply chains. Compromised build systems, poisoned dependencies, vulnerable deployment flows, and improperly secured validator environments are no longer rare exceptions. They are now key attack vectors actively exploited in production.
This blog explores the modern threat landscape surrounding infrastructure and supply chains in blockchain environments. It presents relevant incidents, architectural trends, and actionable approaches to mitigation. The aim is to equip technical organizations and institutional stakeholders with a comprehensive understanding of how security extends beyond contracts and consensus and into the systems that enable them.
Supply Chain Threats Have Become Active Attack Surfaces
Across traditional and decentralized systems, attackers increasingly target what surrounds secure logic rather than the logic itself. The same patterns apply in blockchain: instead of compromising immutable contracts, adversaries now seek privileged positions upstream in the build or deployment lifecycle.
The most prominent categories of compromise include:
- Credential theft and impersonation of developers or maintainers
- Dependency poisoning through open-source package managers
- Exploitation of CI/CD pipelines and build agents
- Compromise of node software and validator libraries
- Manipulation of artifacts during publication or distribution
These compromises can alter deployed bytecode, leak sensitive secrets, redirect wallet flows, or distribute malware to every node in a network. In decentralized ecosystems that rely heavily on open tooling and public registries, the blast radius of these attacks is magnified.
Recent Incidents Reveal Systemic Exposure
Two high-profile attacks in 2025 illustrate the urgency of addressing these vulnerabilities:
The npm Worm Campaign
In September, over 500 packages on npm were compromised via maintainer account takeover. The campaign injected credential-stealing logic into otherwise trusted packages. The compromised libraries spread laterally through package dependencies and GitHub workflows, affecting both Web3 and Web2 tooling.
The Targeted npm Inject Event
A separate incident impacted multiple core JavaScript libraries widely used in blockchain frontends. The payload exfiltrated wallet metadata and transaction data. These libraries existed deep in the dependency trees of Web3 applications, making the compromise difficult to detect in early stages.
Each case involved credential compromise, code injection, and delayed detection. Each incident illustrates how trust assumptions in open ecosystems can be abused with minimal signals visible to downstream consumers.
The Risk Landscape Across the Delivery Lifecycle
Organizations must consider the full pipeline from code to execution. The following layers are commonly targeted:
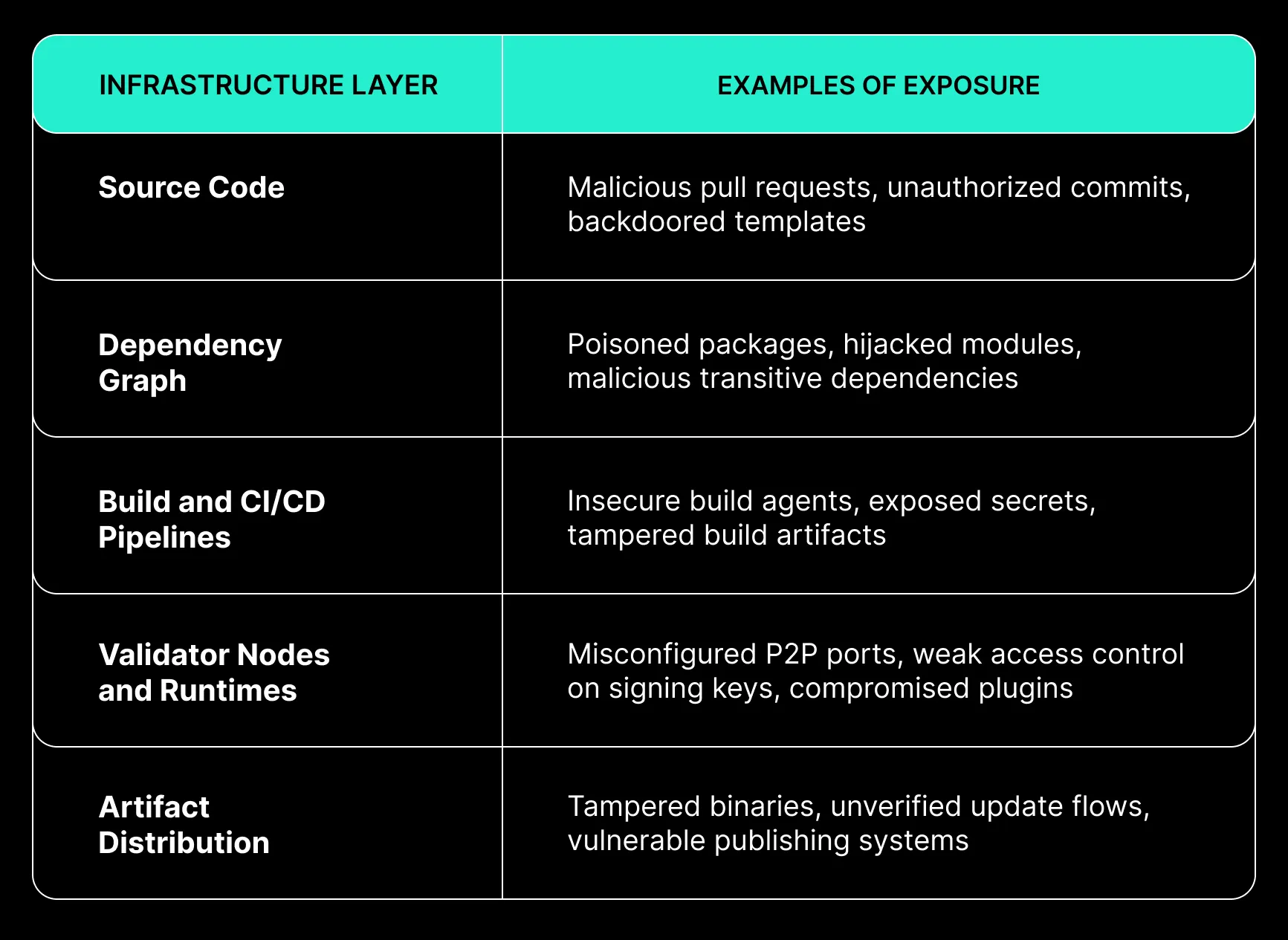
These are not speculative risks. Each has been exploited across ecosystems ranging from DeFi to L2 networks. Some attacks introduce state corruption. Others allow persistent access. All bypass traditional audit surfaces.
Mitigating Infrastructure and Supply Chain Vulnerabilities
Hardening requires defensive coverage at multiple levels, beginning with software engineering practices and extending into operational and organizational design. Effective strategies include:
Controlled Developer Access
Use hardware-backed keys and verified identities for maintainers. Implement strong authentication for code contributors and package publishers. Remove dormant accounts or unused credentials. Rotate secrets routinely and restrict access to production-facing resources.
Hardened CI/CD Pipelines
Use ephemeral build agents, static artifact verification, and signed binaries. Isolate sensitive scripts and deployment keys from build logic. Automate dependency scanning and hash validation for every imported module.
Runtime and Validator Isolation
Validator infrastructure should separate signing keys from exposed interfaces. Remote signing and hardware modules reduce the risk of memory-based exfiltration. Disable unnecessary RPCs and confirm all software updates using reproducible builds or secure channels.
Observability and Monitoring
Log every significant infrastructure operation. Use out-of-band monitoring to detect unexpected package updates, commit patterns, or publishing events. Maintain audit trails for build steps, secret access, and deployment commands.
Containment and Response Planning
Develop recovery workflows for key scenarios, including dependency poisoning, CI compromise, and release rollback. Pre-stage safe branches and artifact snapshots that can be used during remediation windows. Integrate with ecosystem peers for information sharing.
Institutional Responsibility and Trust Continuity
For institutions participating in blockchain systems, trust does not stop at code review. Custodians, exchanges, and enterprise stakeholders increasingly require verifiable transparency into infrastructure practices.
This includes:
- Verification of signing and release workflows
- Audited credential policies and access control
- Security reviews covering build infrastructure and validator setup
- Continuous monitoring and telemetry across software supply chain operations
Protocols seeking institutional integration must treat infrastructure as a first-class surface of assurance.
Spearbit’s Support for Infrastructure-Resilient Deployments
Spearbit provides structured engagements focused on infrastructure and supply chain review. These services include:
- Mapping dependency graphs and exposure to external modules
- Auditing build and publishing flows for safety and reproducibility
- Simulating supply chain compromise to test fallback preparedness
- Reviewing validator setup and runtime configuration
- Establishing continuous monitoring and artifact validation pipelines
This allows organizations to extend their security perimeter beyond application logic and into the operational backbone that enables protocol integrity.
Establishing Standards for Secure Delivery
In 2025, Web3’s technical progress depends on delivery systems that can be trusted under pressure. Secure infrastructure is no longer optional. It is now a prerequisite for deploying resilient systems and sustaining protocol-level confidence.
Organizations that invest in robust supply chain controls, monitoring, and recovery readiness will be better positioned to serve both users and institutions. Spearbit enables that readiness through structured validation and deep coordination across security domains.
To secure your deployment infrastructure and assess your supply chain exposure, contact us. Our network of researchers is ready to help you define standards, validate execution, and strengthen your deployment model.