NEAR offers a performance-optimized, WASM-based smart contract platform designed to scale through parallel execution and usability-first design. It supports high throughput, fast finality, and contract development in familiar languages such as Rust and TypeScript. These strengths have positioned NEAR as a compelling platform for consumer-facing applications and modular Web3 infrastructure.
Yet, this architecture introduces unique security challenges. From asynchronous call handling and gas metering to validator set dynamics and interchain bridges, deploying safely on NEAR requires deliberate choices at both the contract and infrastructure levels. This guide outlines essential considerations for builders seeking to maintain integrity and uptime across the NEAR stack.
Runtime Architecture and Execution Safety
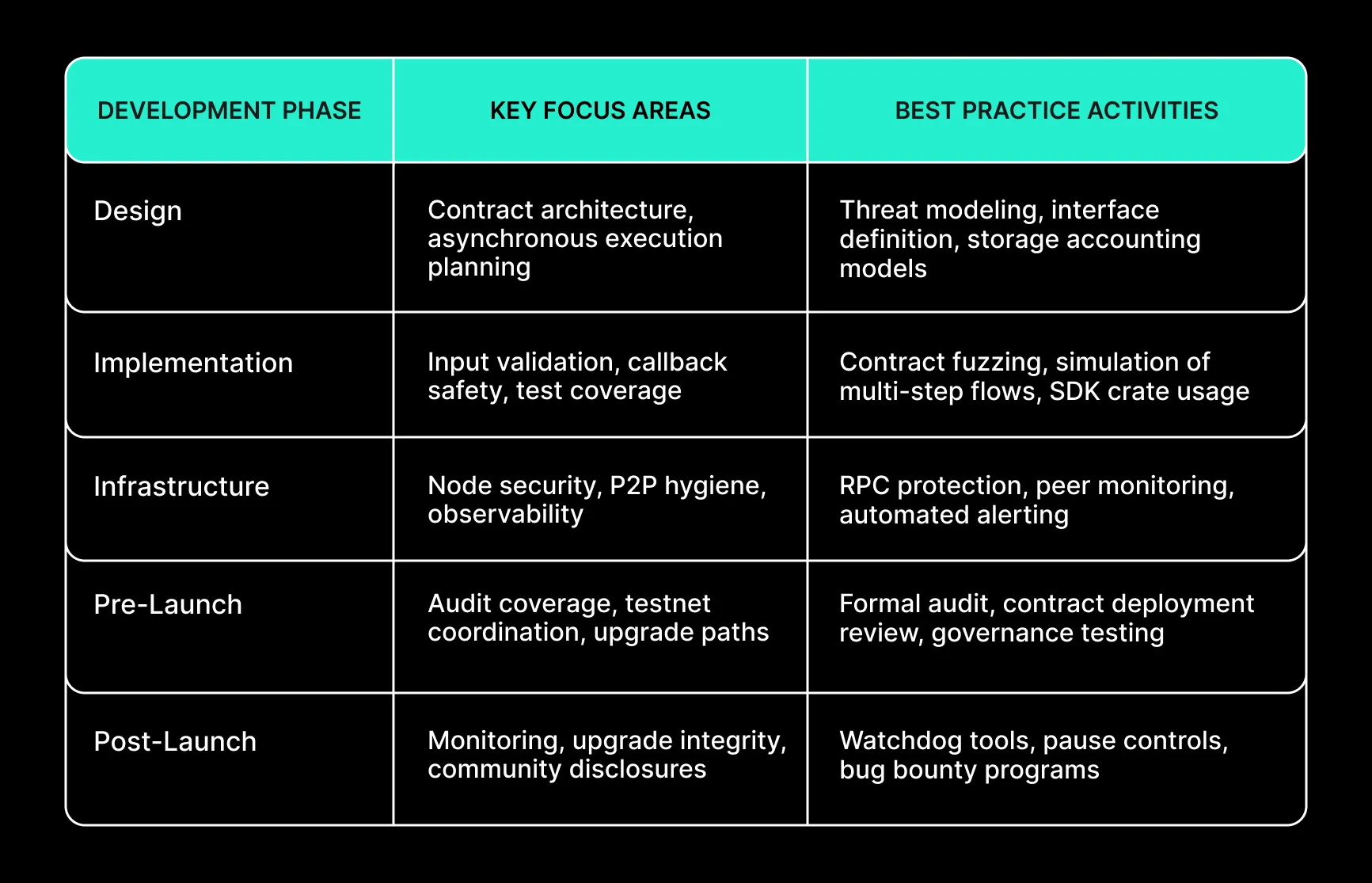
NEAR’s contract execution is powered by a WASM runtime, offering language flexibility and speed. Contracts are compiled to WebAssembly and executed in an isolated environment. While this abstraction improves efficiency, it also introduces distinct risks:
- Unchecked Integer Overflows: Rust contracts must explicitly enable overflow checks. Failing to do so can result in silent logic errors or bypassed constraints.
- Asynchronous Cross-Contract Calls: NEAR handles inter-contract communication asynchronously. Developers must structure callbacks carefully and validate state transitions to avoid race conditions and unexpected execution branches.
- Storage and Gas Accounting: NEAR meters storage usage and requires users to prepay for changes. If contracts fail to correctly calculate storage costs, they may inadvertently reject transactions or allow denial-of-service vectors.
Best practices include enabling overflow checks by default, using structured logging, validating inputs at the top of contract execution, and simulating common call flows. NEAR provides SDKs with helper crates to support reproducibility and contract safety. These should be integrated into every contract development flow.
Validator Dynamics and Consensus Assumptions
NEAR uses a Thresholded Proof-of-Stake (TPoS) consensus with validator rotation, finality sampling, and epoch-based selection. This design offers fast block confirmation and high liveness under normal conditions, but introduces assumptions developers must understand:
- Validator Set Size and Churn: NEAR rotates validators every epoch (approximately 12 hours). Rapid churn or misaligned stake incentives may lead to inconsistent participation or accidental forks.
- Light Client Safety: Applications relying on light clients or off-chain relayers must monitor finality thresholds and avoid accepting transactions from unfinalized blocks, especially in high-volatility environments.
- Validator Attacks and Downtime: While NEAR does not use traditional slashing, validators can be temporarily ejected for downtime. However, this does not address equivocation or censorship directly.
Builders deploying infrastructure or middleware should account for possible validator underperformance and integrate mechanisms to detect delayed finality, missing receipts, or orphaned transactions. NEAR’s RPC and indexer stack provide observability tools for this purpose.
Network Layer and Node Security
In late 2024, NEAR experienced a network-layer vulnerability where a malformed handshake could crash nodes through the P2P layer. The incident—dubbed the “Web3 Ping of Death”—highlighted the importance of message validation and node hardening.
Operators and infrastructure contributors should adopt strict network security controls, including:
- Disabling unauthenticated debug endpoints
- Restricting RPC access to known IPs or private networks
- Monitoring node uptime, peer counts, and memory usage
- Applying timely patches to avoid known handshake exploits
Custom indexers or off-chain agents should also avoid over-trusting network state or partial block data. Treat node-facing interfaces as untrusted and enforce input sanitization across the stack.
Smart Contract-Level Considerations
NEAR contracts differ from EVM environments in several ways. Some security patterns must be adapted accordingly:
- No Built-In Reentrancy Protection: Contracts must use state-first design and avoid nested calls that can be re-entered through callbacks.
- Callback Misuse: Improper validation of return values in callbacks can lead to faulty state transitions or spoofed data.
- Gas Exhaustion via Loops: Iterating over large collections (e.g. balances, NFTs) may lead to gas exhaustion and failed transactions. Use pagination and limits in all user-facing queries or writes.
- Randomness and Oracle Safety: NEAR contracts requiring randomness should not rely on block hashes or timestamps. Use oracle services or VRF mechanisms with proven liveness and correctness guarantees.
Following NEAR’s official security guidelines, integrating fuzzing tools, and conducting differential testing are critical for avoiding runtime-level vulnerabilities.
Cross-Chain Interactions and Bridge Exposure
Several projects on NEAR rely on cross-chain bridges to interface with Ethereum, Aurora, or other networks. Bridge integrity depends on:
- Timely finality assumptions on the source chain
- Honest relayer behavior and signature aggregation
- Payload validation and non-replay guarantees
Bridge vulnerabilities remain a leading cause of asset loss in Web3. Builders should audit bridge contracts and associated relayer logic, and ensure emergency controls and pausing mechanisms are in place. Any cross-chain mint or burn logic should be isolated and hardened with defensive validation.
Incident Transparency and Ecosystem Maturity
To date, NEAR has avoided major contract-level exploits or consensus-level failures. Public data shows a relatively strong ecosystem security posture, with active audits, public vulnerability disclosures, and responsiveness to community-reported bugs. However, audit coverage remains uneven across smaller projects.
To support ecosystem maturity, developers should:
- Publish audit reports and formal verification results
- Use public bug bounty programs or coordinated disclosure processes
- Share code libraries and testing suites across teams
The NEAR Foundation and ecosystem partners have emphasized reproducible builds, shared SDKs, and open-source standards. These contribute meaningfully to ecosystem trust but require continual maintenance and community alignment.
Security-Driven Recommendations for NEAR Builders
How Spearbit Supports NEAR Deployments
Spearbit offers specialized review engagements for NEAR-based applications, infrastructure teams, and bridge providers. Our researchers analyze contracts, validator assumptions, governance mechanics, and off-chain dependencies through:
- Runtime behavior analysis and contract state simulation
- Callback sequence inspection and asynchronous validation
- Infrastructure reviews focused on node security and RPC exposure
- Validator logic modeling under partial participation or attack conditions
- Upgrade coordination simulations and rollback planning
- Bridge integrity review across multi-chain deployments
We work closely with teams building on NEAR to align security assumptions with operational readiness and regulatory maturity.
Summary
NEAR offers a performant, developer-friendly environment optimized for scalable smart contracts and modular execution. But this power demands attention to runtime behavior, validator coordination, cross-chain design, and off-chain infrastructure.
Security on NEAR is not limited to smart contract correctness. It must encompass node reliability, consensus awareness, governance design, and data integrity.
To discuss a NEAR-specific security engagement or simulation effort, contact us. Our network of researchers is equipped to support your deployment across design, validation, and live system readiness.




