Quantum computing presents a future threat with irreversible consequences for blockchain protocols that rely on traditional cryptography. This blog outlines why the quantum threat must be considered a present risk, explains the architectural vulnerabilities in Web3 systems, and proposes concrete strategies for developers, cryptographers, and protocol designers to secure their systems for the post-quantum era.
Introduction
Quantum computing is advancing at a pace that challenges the long-term reliability of existing cryptographic systems. The cryptographic foundations of blockchain, particularly asymmetric schemes such as ECDSA, are mathematically secure against classical computing models, but they are known to be vulnerable to quantum algorithms. The key issue is that blockchain systems are publicly verifiable and immutable. Once a key has been exposed, there is no mechanism to revoke or hide it. These properties introduce enduring risk when adversaries have access to stronger computation in the future.
This paper explores the implications of this risk, the architectural decisions that amplify it, and how protocols can adapt now to avoid delayed compromise.
The Mechanics of the Threat
Blockchain systems commonly rely on elliptic curve cryptography for signature verification. Public-private key pairs generated using these schemes are secure under classical assumptions, but vulnerable to Shor’s algorithm when executed on sufficiently powerful quantum computers. The exposure of a public key enables private key recovery once quantum resources become available.
Harvest Now, Decrypt Later
State-level actors and long-term adversaries are already collecting on-chain data. This includes public keys, signatures, and protocol-level interactions. The data collected now may become exploitable in the future when quantum computing reaches the required thresholds. The timeline is unknown, but the exposure is permanent.
Vulnerabilities in Web3 Systems
Blockchain systems cannot retroactively remove or conceal historical data. Public keys that have been revealed during transaction signing are permanently accessible. Address reuse remains common. Wallet implementations, particularly earlier ones, often lacked strong key hygiene. Externally Owned Accounts (EOAs) in Ethereum directly expose key material upon signature. Even where public keys are derived indirectly, exposure is inevitable upon transaction submission.
The second layer of risk arises from architectural rigidity. Many systems cannot change their cryptographic primitives. Multisignature contracts, bridge controls, governance contracts, and oracles often rely on hardcoded public keys or verification logic. There is frequently no upgrade path that would allow for quantum-resistant replacements.
Protocol Design Constraints
Protocol design in Web3 favors determinism and minimalism. Many contracts verify signatures using fixed logic. Validator sets are embedded in contract storage. Governance is enforced through predetermined public keys or signatures. If these verification assumptions are bound to ECDSA or similar schemes, the entire trust model is predicated on the continued unbreakability of those primitives. This constraint results in cryptographic rigidity.
Overview of Quantum-Resistant Cryptographic Schemes
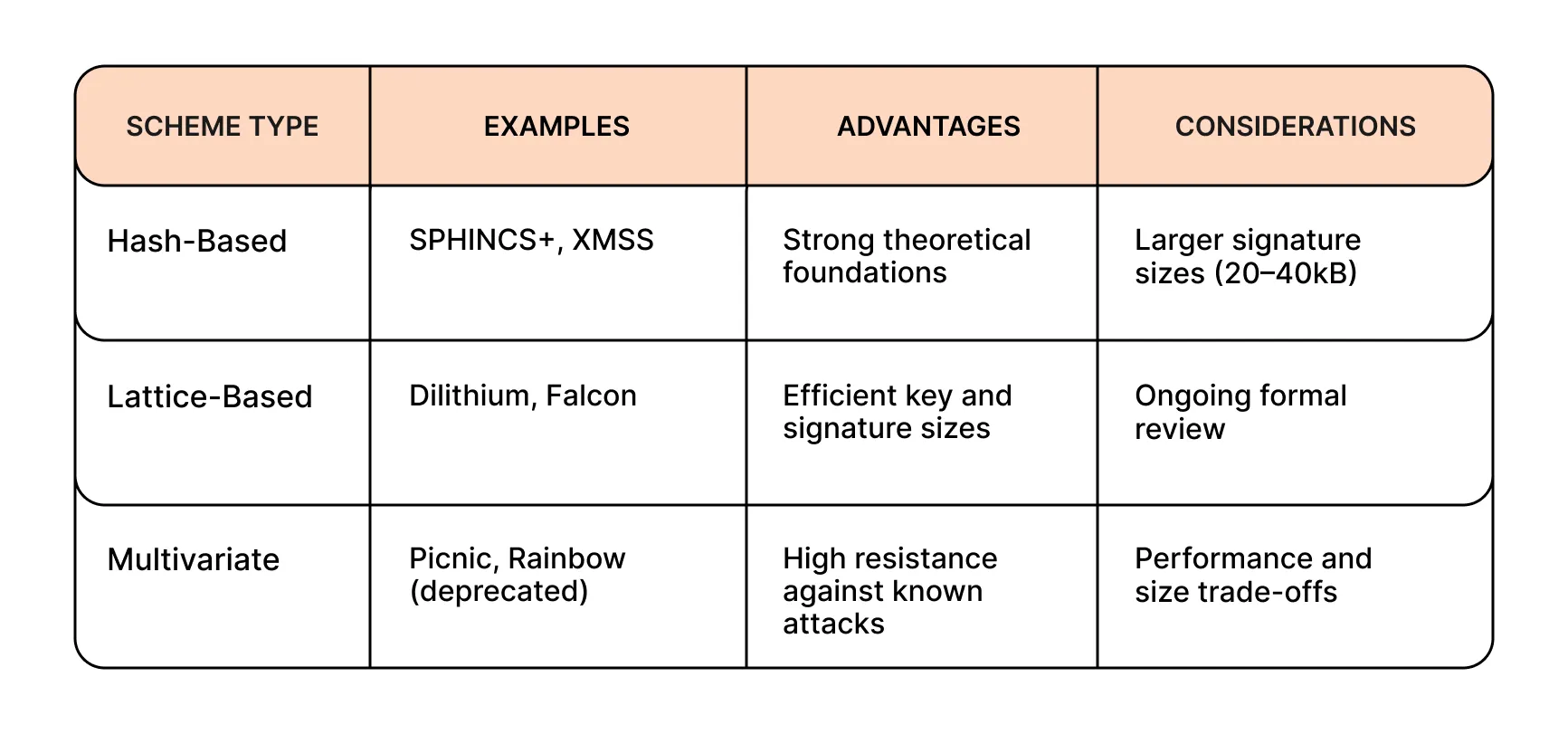
While some schemes are NIST finalists, adoption remains limited due to integration complexity and lack of native support in most blockchain virtual machines.
Key Size is Not a Mitigation
The fundamental vulnerability of traditional schemes lies in their mathematical structure. Increasing key size does not prevent attacks using quantum algorithms. RSA, ECDSA, and other discrete logarithm-based schemes are vulnerable regardless of key length. Post-quantum readiness requires different assumptions and mechanisms.
Time-Delayed Compromise Through Irreversible Exposure
A protocol that accepted a multisignature from a trusted address in 2021 may face compromise if that key becomes reconstructable in 2028. Exposure is permanent. Signature data is public. Once private key recovery becomes possible, historical approvals can be replayed or misused. DAOs, bridges, or upgradeable contracts are at risk if key authority is not revocable or auditable.
Enabling Cryptographic Flexibility
Protocols should be designed with cryptographic agility. This means:
- Support for signature verification abstraction at the contract layer
- Ability to rotate keys and signer authorities without full redeployment
- Use of multisignature and threshold schemes with adjustable quorums
- Storage of configuration state separate from execution logic
Hybrid approaches can be used where legacy and post-quantum signatures coexist temporarily, allowing for gradual migration.
Immediate Actions for Protocol Teams
- Conduct Exposure Audits
- Identify all addresses that have revealed public keys.
- Review signer histories across governance and upgrade systems.
- Simulate Quantum-Level Adversaries
- Map the impact of private key reconstruction based on current exposure.
- Evaluate protocol behavior under key compromise scenarios.
- Assess Upgrade Capabilities
- Determine whether contract code allows for cryptographic scheme migration.
- Review whether authority can be reassigned to post-quantum compatible mechanisms.
- Eliminate Static Trust Anchors
- Replace long-lived static signers with rotating structures.
- Implement expiration and audit procedures for signer roles.
- Engage with PQC Development
- Track NIST standardization and research libraries such as OpenQuantumSafe.
- Begin performance benchmarking of candidate schemes within testnets.
Cantina’s Perspective on Quantum Risk
Quantum computing is a developing area of concern for public key infrastructure. The risk model it introduces is unconventional. Exposure happens now, but compromise may not occur for years. This creates a security timeline that most protocols were never designed to account for.
We are observing how protocols handle cryptographic rigidity, the reuse of long-lived keys, and the limitations in rotating or upgrading key systems. In many cases, public key exposure is already embedded, and mitigation would require fundamental changes to how signature verification is implemented.
There is no standard approach yet, and most systems do not treat quantum risk as an active part of their threat model. However, the long-term implications are relevant for any protocol expected to maintain security guarantees across decades. We see value in continuing to study how these patterns evolve, and what kinds of architecture could support flexibility under future cryptographic requirements.
Conclusion
Quantum computing introduces a credible, time-delayed threat to public key infrastructure. In blockchain systems, where data cannot be revoked and signatures cannot be erased, exposure becomes permanent. Cryptographic assumptions that underpin most protocols today are no longer sufficient for long-term security. Teams must begin the transition to more flexible, resilient architectures.
The cryptographic future will reward those who plan for transformation. Quantum risk is not a distant theoretical event. It is a compounding liability built into systems that were never designed for cryptographic change.
“We believe future-ready security requires protocol design that accounts for quantum risk today. We’ll continue tracking this space, and supporting the organizations who take it seriously.




