In modern blockchain development, the ability to upgrade protocol logic is essential. Protocols need to evolve to address emerging technical requirements, respond to governance outcomes, and incorporate new security improvements. However, each on-chain upgrade introduces powerful control surfaces that must be evaluated through structured audit processes.
This blog outlines critical areas of focus for securing upgradeable protocols, and introduces Spearbit’s approach to upgrade validation. The goal is to equip both organizations and institutional partners with a security framework that supports long-term trust, operational clarity, and resilience across governance-driven deployments.
Why Upgrade Mechanisms Require Specialized Validation
Upgradeability is a strength, but also a potential failure mode. Protocols that support upgradability must design those systems with the same care applied to their core logic. If governance paths, storage migrations, or access roles are misconfigured, the consequences can be systemic.
Unlike traditional audits that evaluate the logic of current deployments, upgrade-focused assessments ask a different set of questions: Who controls change? When can upgrades occur? How are changes coordinated across contracts, data, and stakeholder expectations?
The control layer of a protocol, the upgrade system, must itself be subject to rigorous scrutiny.
Security Evaluation Areas for Upgradeable Protocols
- Execution Authority and Role Design
- Clearly define who can trigger upgrades. Whether through DAO voting, multisigs, or specialized governance modules, the control plane must be observable, decentralized where appropriate, and include mechanisms to prevent unilateral changes.
- Governance and Voting Simulation
- Upgrades typically require a proposal and approval process. Auditors must assess whether voting thresholds, quorum rules, and timelocks are robust against low participation or attack scenarios. Simulation of edge cases, such as spam proposals or duplicate execution, should be part of the audit process.
- Proxy Compatibility and Storage Alignment
- In proxy-based upgrade patterns, the storage layout must remain compatible across versions. Misaligned variables, wrong inheritance order, or uninitialized slots can brick critical systems. Validation includes storage layout comparisons, migration script testing, and revert path confirmation.
- Emergency Paths and Failover Systems
- Some protocols maintain an emergency upgrade mechanism for critical patches. These paths must include clear thresholds and delays, not just privileged access. Review should confirm how fast upgrades can happen and who authorizes them under stress.
- Monitoring, Events, and Observability
- Protocols should emit clear, structured events when an upgrade is proposed, scheduled, and executed. Stakeholders, including custodians and exchanges, must be able to detect these events and respond accordingly. Logging and alerting are core elements of operational trust.
- Rollback Readiness and Regression Protections
- Effective upgrade systems include rollback mechanisms. But rollbacks themselves must be secured to avoid unintended behavior. Reviewers should evaluate whether upgrade reverts are available, testable, and observable.
Common Failure Modes in Upgradeable Protocols
Upgrade mechanisms have failed in the past due to:
- Storage corruption after improper variable changes
- Emergency upgrade misuse by centralized entities
- Governance bypass due to low participation or broken threshold logic
- Introduction of previously patched bugs due to incomplete regression testing
Every one of these examples was technically preventable with specialized upgrade audits. Without auditing the upgrade path, protocols expose themselves to irreversible control failures.
Lifecycle-Aligned Approach to Upgrade Security
Security must be integrated across the entire upgrade lifecycle:
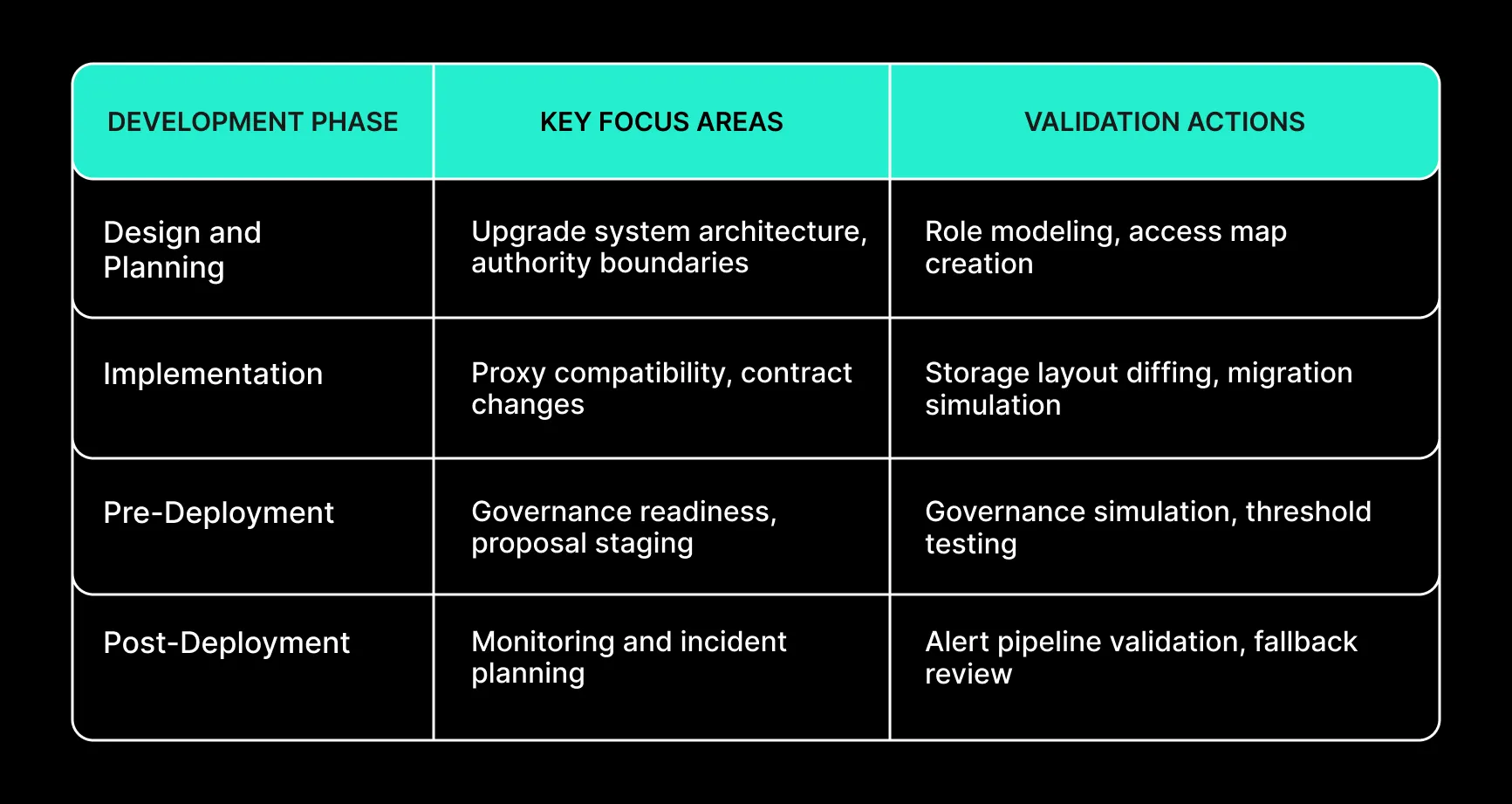
How Spearbit Supports Upgrade-Ready Protocols
Spearbit provides specialized engagements for upgradeability audits. Our structured process supports modular protocols, governance-aligned systems, and rollup or appchain deployments where resilience and clarity are critical.
Key services include:
- Upgrade Surface Mapping: We diagram all control flows, ownership paths, and cross-contract dependencies.
- Storage and Proxy Validation: Our auditors compare layout across versions and simulate migrations in test environments.
- Governance Simulation: We model low-participation scenarios, attack proposals, and quorum bypass attempts.
- Operational Readiness Audits: We validate monitoring systems, test alert propagation, and check observability.
- Fallback and Recovery Support: We assess rollback strategies and confirm their ability to restore network stability.
We partner with security teams, governance engineers, and institutional stakeholders to ensure change management does not become a hidden source of fragility.
Institutional Alignment and Integration Readiness
For institutions integrating with or providing infrastructure around on-chain protocols, upgradeability affects trust at the deepest level.
Spearbit helps institutions answer key operational questions:
- Can we track and verify upgrade proposals before they are executed?
- Are there built-in notice periods and review buffers?
- Can any single role or entity push through critical upgrades?
- Are failovers tested and documented?
With proactive validation and security-aligned governance modeling, protocols can present a mature posture to custodians, liquidity providers, and enterprise partners.
Summary
Protocols are not static, and neither is their attack surface. As protocols introduce upgrade paths, they must design, document, and validate those paths with the same intensity applied to contract logic.
Spearbit helps ensure upgradeable systems remain safe, observable, and consensus-aligned. Our lifecycle-aligned validation framework provides coverage across planning, simulation, and post-deployment scenarios.
To request a protocol audit or to assess your upgrade system before activation, contact us. Our researchers bring depth, clarity, and institutional alignment to change-critical infrastructure.




