As the Cosmos ecosystem continues to expand, developers and infrastructure teams face an increasingly complex security environment. From deterministic execution in ABCI methods to the modular challenges of IBC-powered interoperability, Cosmos-based appchains must navigate nuanced risk surfaces. This guide outlines high-impact vulnerabilities and purposeful mitigations, drawing from documented incidents, technical research, and best practices across the ecosystem.
The Determinism Imperative: Preventing Consensus Disruption
Determinism lies at the heart of consensus safety in BFT systems such as CometBFT. Any divergence in state can lead to validator disagreement, halted blocks, or chain forks.
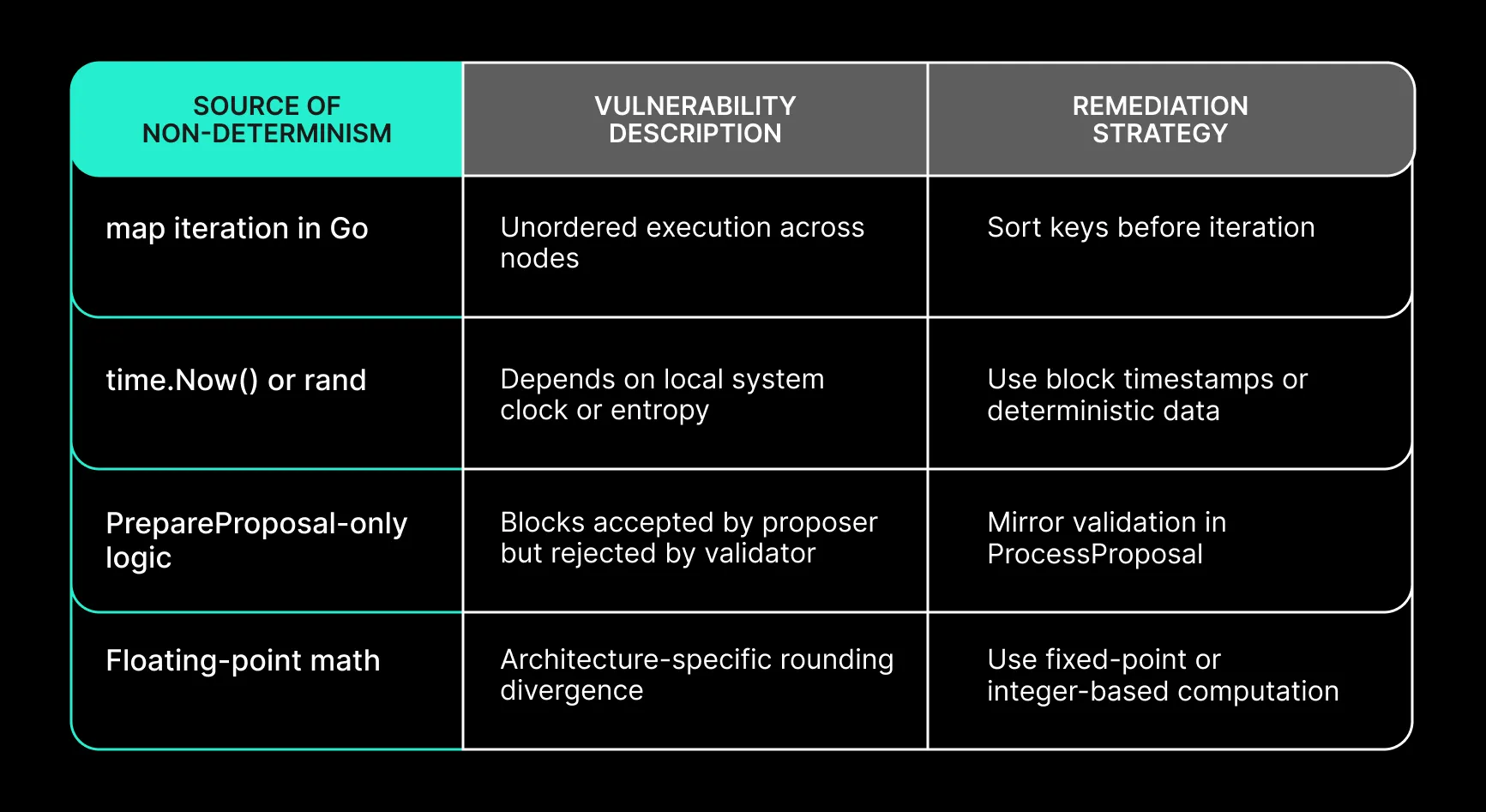
- Non-deterministic logic, including unordered map iterations or reliance on runtime variables such as time.Now(), can produce inconsistent outcomes across nodes. This behavior has triggered production-level halts.
- Mismatched execution between PrepareProposal and ProcessProposal can introduce validation inconsistencies between proposers and validators.
- Floating-point operations in state-altering logic are unsafe due to architecture-dependent rounding behavior.
Determinism Risk Table
Panic, Error Handling, and Execution Hazards
Uncaught panics in ABCI methods can halt the entire chain.
- BeginBlock, EndBlock, Commit, and DeliverTx must handle edge-case input and maintain state consistency under failure conditions.
- Batch processing of actions such as SendCoins across multiple recipients must include per-item validation to prevent mass failure.
- Runtime panics from incorrect keeper usage, unexpected types, or failed assertions must be guarded and logged.
Mitigation: Wrap all consensus-bound logic in panic-safe constructs. Enforce structured logging and observable error signaling before state transitions.
Resource Metering and Performance Risks
Gas management remains one of the most underdeveloped disciplines in Cosmos deployments.
- Hooks such as EndBlocker and BeginBlocker often execute without bounded gas, enabling O(n) or worse behavior. Several validators have exploited validator loops to delay or crash the chain.
- CheckTx executes prior to block inclusion and without enforced gas metering. Excessively complex ante handler logic can serve as a DoS vector.
Recommendation: Bound loop length, use indexed data access, and simulate gas behavior under realistic validator and user load scenarios.
IBC Integrity and Interchain Trust
IBC enables Cosmos’ modular interoperability, but each packet path must be explicitly trusted and scoped.
- Default IBC modules accept packets from any chain. Application logic must verify sender chain identity and channel origin for privileged actions.
- Packet replay and airdrop spoofing have occurred due to modules failing to authenticate source chains or validate claim logic.
- IBC applications such as interchain staking, airdrop claim routing, and governance voting require full-path validation at both message and channel levels.
Misuse of Cosmos Modules and Interactions
The modular nature of the Cosmos SDK enables composability but increases coupling between modules.
- Incorrect registration of staking validators has allowed key duplication or takeover.
- Broadcasting during Commit introduces deadlocks due to CometBFT’s mempool locks.
- Mass SendCoins in BeginBlocker without per-denom handling has caused invariant violations and runtime crashes.
Best practice: Use deny-lists for module accounts, restrict cross-module write permissions, and validate upstream keeper paths during integration.
Cosmos-Specific Development Considerations
- sdk.Context deprecation: The SDK now uses appmodule.Environment to eliminate reliance on global mutable state. All modules must migrate to this interface.
- Consensus parameter updates: When modifying consensus parameters during FinalizeBlock, omit no subfield. Defaults will otherwise override previous values.
- Vote extensions: Applications using ExtendVote or VerifyVoteExtension must treat those extensions as non-authoritative until revalidated in PrepareProposal.
How Spearbit Supports Cosmos Appchain Security
Spearbit provides structured, high-signal security review tailored to Cosmos systems. Our researchers apply full-context validation across consensus layers, application modules, and interchain protocols.
- Determinism assurance through ABCI path simulation, including proposers and non-proposers
- Panic-path tracing across execution hooks and transaction logic
- Resource constraint analysis for validator-induced DoS or module-induced stalls
- IBC origin authentication, channel mapping, and replay prevention
- Upgrade and validator key rotation analysis under CometBFT coordination
- Validator liveness modeling and incident response simulation
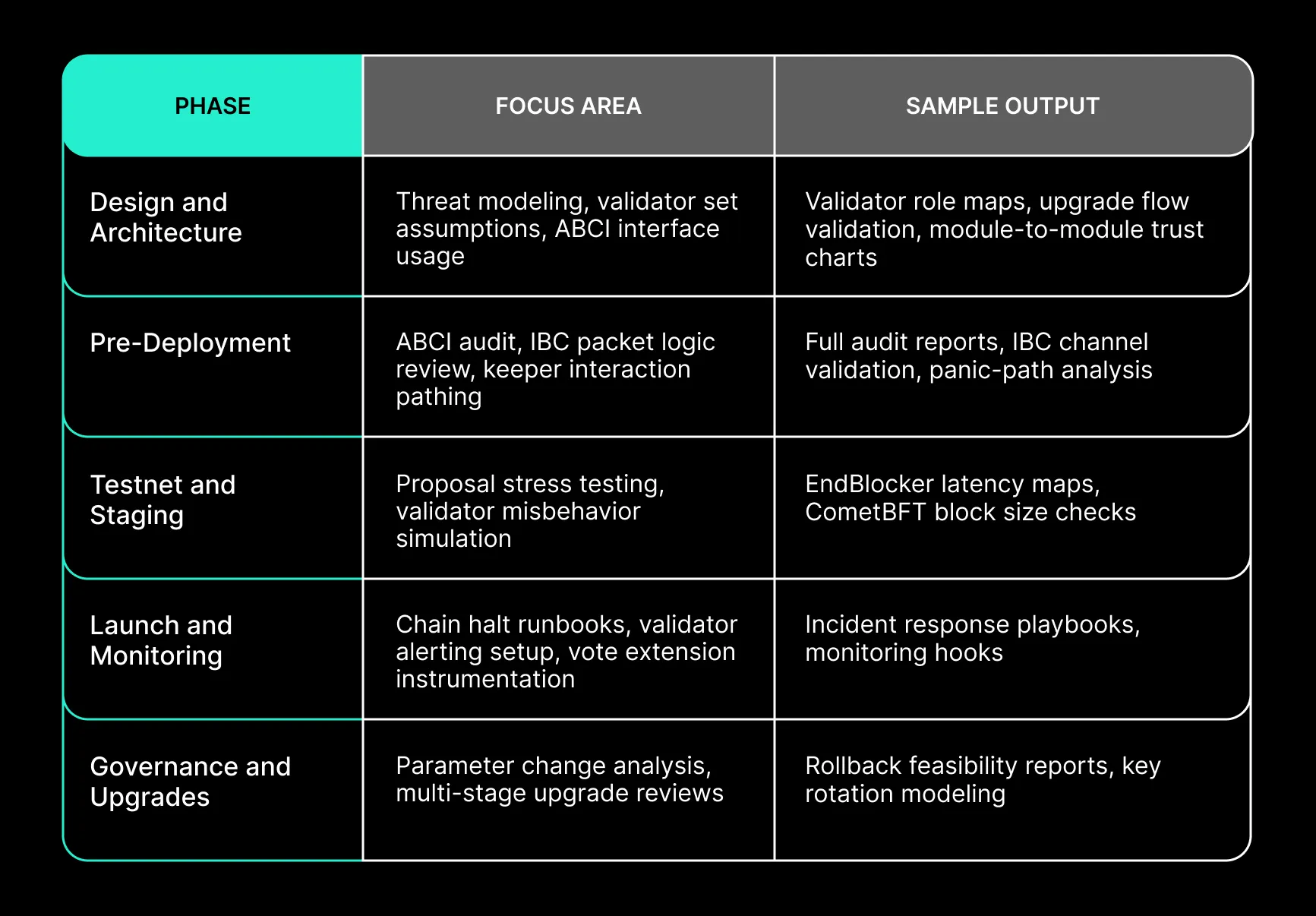
End-to-End Security Coverage for Cosmos-Based Protocols
Security in Cosmos is a lifecycle challenge. Spearbit’s methodology applies continuous validation across the entire development and operational arc of appchain projects.
Summary
Security in Cosmos requires attention across execution boundaries, chain configuration, and cross-domain interaction. Determinism, validator integrity, IBC trust paths, and modular correctness are not secondary considerations, they define operational viability.
Spearbit’s network of researchers works with protocol teams to close gaps before they become exploits. From deterministic validation to IBC proof flow simulation, our reviews focus on actionable alignment with Cosmos consensus guarantees.
To schedule a Cosmos appchain security review, simulation scope, or upgrade path audit, contact Spearbit. Let’s secure your network from genesis block to production confidence.




