Modular blockchain architectures distribute responsibilities across independent components: sequencers order transactions, provers submit validity proofs, data availability layers handle block publishing, and execution clients apply state transitions. This modularity enables scalability and specialization, but it also creates a fragmented security landscape that demands structured coordination.
As protocols adopt rollup frameworks, sovereign chains, and off-chain proof systems, understanding who secures what becomes essential. This blog provides a framework for evaluating security coordination in modular environments, with practical guidance for organizations, developers, and institutional integrators.
Modular Stack Overview
Modular protocols delegate responsibilities to specialized layers:
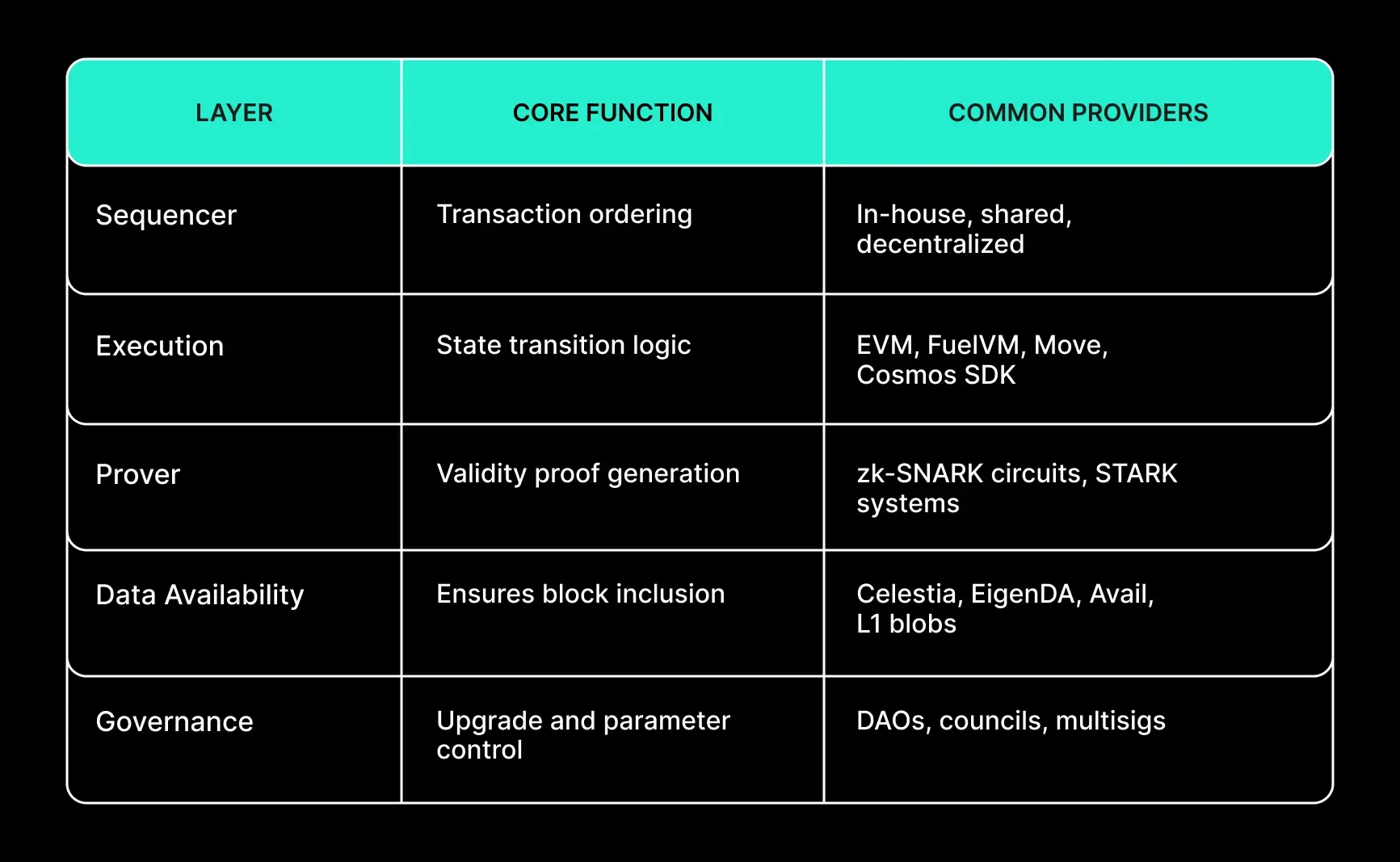
Security in a modular context means evaluating these layers not in isolation, but in terms of their interactions, dependencies, and failure propagation potential.
Sequencer Design and Consensus Guarantees
Sequencers play a critical role in defining transaction order and controlling access to block inclusion. While many modular protocols rely on centralized or permissioned sequencers today, future models aim for decentralization.
Risks and implications:
- Centralized sequencers can censor transactions or reorder them for MEV extraction.
- Downtime or misbehavior can stall the system if fallback mechanisms are not in place.
- Decentralized sequencer sets require consensus and fair ordering protocols, which introduce complexity and coordination challenges.
Recommendations:
- Evaluate liveness guarantees and fallback plans.
- Ensure transaction inclusion guarantees are transparent and enforced.
- Simulate adversarial sequencer behavior in test environments.
Prover Liveness and Circuit Integrity
Provers generate validity proofs that secure the rollup’s execution trace. They must produce correct and timely proofs for each batch of transactions. However, prover pipelines are still maturing, and centralization remains the norm.
Security implications:
- A malfunctioning or malicious prover can delay settlement or block finality.
- Circuit-level bugs can result in invalid state transitions being accepted by L1.
- Different systems use different assumptions: some require L1 verification, others depend on committee attestations.
Recommendations:
- Validate prover assumptions, especially in beta-stage circuits.
- Require observable metrics for proof submission timelines and failure recovery.
- Integrate circuit audits and formal verification into deployment cycles.
Data Availability Layers and Inclusion Guarantees
Data availability (DA) ensures that the full transaction data behind a block is actually published and retrievable. Without this, state transitions cannot be validated or challenged.
Key risks:
- Delayed or incomplete data publishing breaks light client assumptions.
- DA layer failures can stall the chain or block rollup verification.
- Modular systems with external DA must verify data was posted before accepting state changes.
Best practices:
- Use DA layers with erasure coding, light client support, and auditability.
- Confirm inclusion guarantees independently from the rollup itself.
- Implement alerting for DA delays or unverified blocks.
Governance and Upgrade Synchronization
In modular systems, upgrades must propagate across multiple components—execution logic, sequencer behavior, prover settings, and DA contracts. Unsynchronized upgrades risk incompatibility, downtime, or consensus failures.
Coordination challenges:
- Lack of structured governance delays vulnerability patching.
- Upgrades must be synchronized across smart contracts, circuits, and node clients.
- Emergency changes can be misused if access is concentrated or undocumented.
Recommendations:
- Use upgrade simulations to model edge cases and timing assumptions.
- Publish pre-deployment plans with testnets, audit artifacts, and rollback paths.
- Ensure all components emit clear upgrade events for monitoring.
Infrastructure-Level Assumptions
Beneath protocol logic sits infrastructure that must remain hardened: RPC endpoints, validator nodes, remote signers, relayers, and off-chain daemons. In modular systems, these components can become implicit trust dependencies.
Security measures:
- Segment infrastructure by role and expose only required interfaces.
- Apply telemetry and health checks to every off-chain component.
- Include infrastructure coverage in security assessments and incident simulations.
Implications for Institutions and Security Partners
Institutions integrating with modular blockchain ecosystems, whether as custodians, data providers, infrastructure participants, or liquidity managers, depend on predictable assumptions across the system stack. When security responsibilities are fragmented across sequencer operators, prover teams, DA providers, and governance councils, institutional confidence requires deliberate clarity around these roles.
Key considerations include:
- Who controls settlement guarantees?
Institutions need to understand who is responsible for finalizing application state. This includes the conditions under which a sequencer can reorg transactions, how prover validity is enforced, and what happens when proofs are delayed or withheld. - Are data availability commitments independently verifiable?
DA providers must offer publicly auditable inclusion guarantees. Institutions often require on-demand proofs or third-party assurance systems that can confirm data was made available before acceptance. - What mechanisms exist for dispute resolution?
Especially in fraud-proof or optimistic systems, institutions must understand the resolution process. This includes timelines for challenge windows, staking requirements, and rollback coordination in the event of a fault. - Is there clarity on governance and upgrade timing?
Upgrades to sequencer logic, DA parameters, or prover circuits must follow timelines that support institutional change management. Transparent processes, with advance disclosure and technical artifacts for review, are essential. - Can observability be integrated into operational dashboards?
Enterprises must be able to monitor liveness, proof submission, DA confirmations, and governance activity as part of their risk operations. APIs and structured feeds should support automated compliance tracking.
When modular systems fragment security and operational responsibility, the cost of unclear assumptions is borne by the organizations depending on them. Clear documentation, structured risk alignment, and verifiable commitments are prerequisites for adoption.
Establishing a Coordination-Centric Security Standard
Security in modular architectures must move beyond smart contract audits and focus on coordination. The surface area spans across off-chain actors, asynchronous pipelines, and multi-actor governance. Each protocol team, infrastructure partner, and institution must approach security through the lens of layered accountability.
Spearbit supports this shift by conducting structured engagements across sequencer behavior, prover design, DA dependencies, governance resilience, and infrastructure hardening. Our goal is to establish coordination-aware assurance programs that reflect the modular reality of modern blockchains.
To discuss a coordination-focused security review or build an institutional readiness plan for your modular deployment, contact Spearbit. We are ready to support all layers of your stack.