Key Takeaways
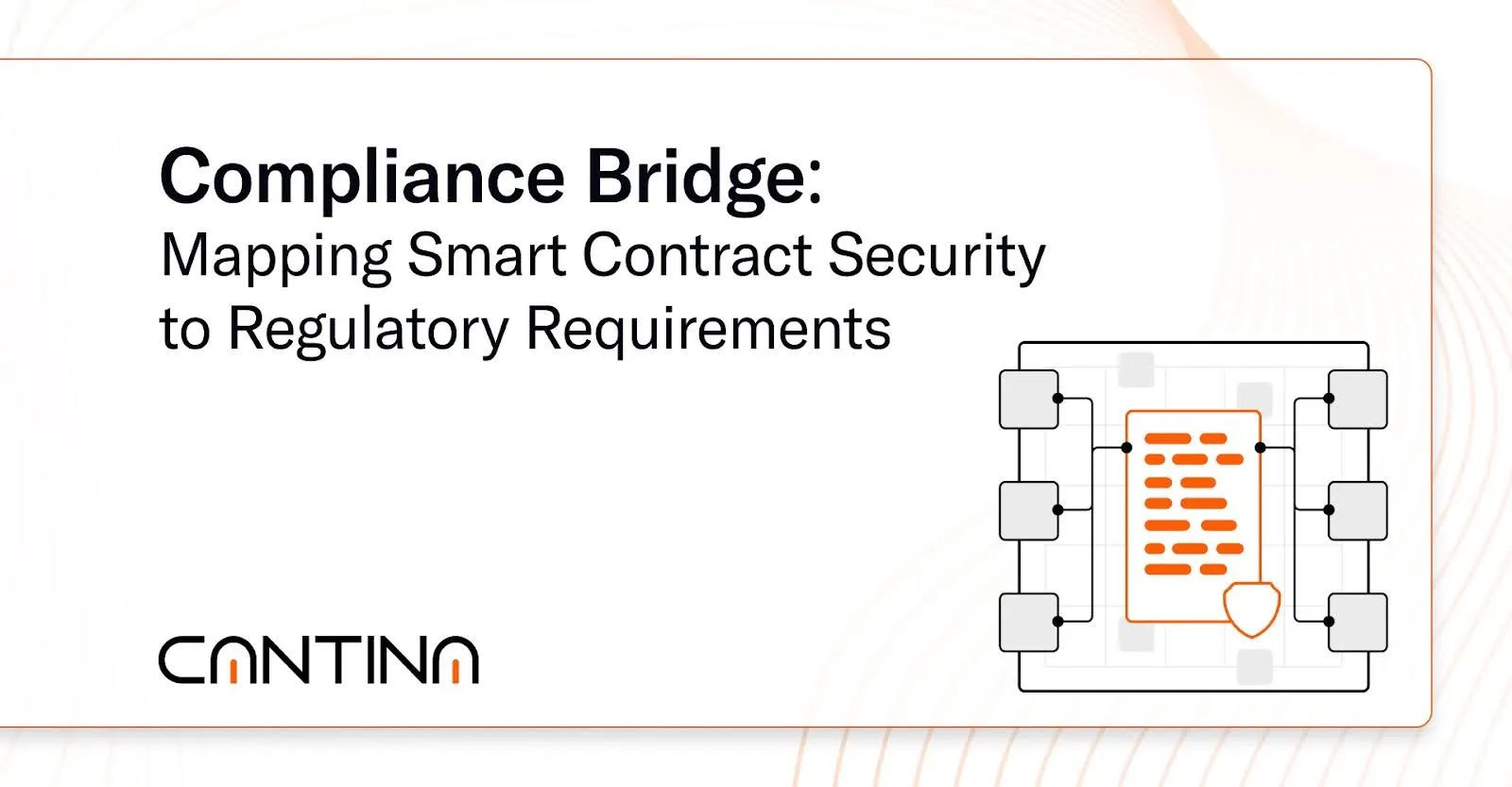
- Smart contract security has to go beyond bug detection; it needs to show how systems enforce control, access, and accountability. Institutional reviewers want to see who can act, how actions are gated, and whether behavior can be verified.
- Most compliance signals are already built into protocol design. Timelocks, multisigs, on-chain logs, and CI/CD gating can align with regulatory expectations when properly structured and documented.
- Teams that align engineering, legal, and ops around these controls move faster through diligence. Cantina helps turn security review outputs into artifacts that meet GRC standards without compromising decentralization.
Introduction
DeFi organizations are facing more rigorous scrutiny not just around bugs, but around control, change management, and traceability. security reviews alone aren’t enough to satisfy expectations under frameworks like MiCA, DORA, and evolving SEC guidance. Legal and risk teams want to understand how the system governs itself in practice. Most security review reports don’t address that. In this article, we explore how smart contracts can surface actionable compliance signals and how Cantina helps teams make those signals visible and reviewable, without compromising their operational design.
From Vulnerability-Focused to Control-Oriented Security
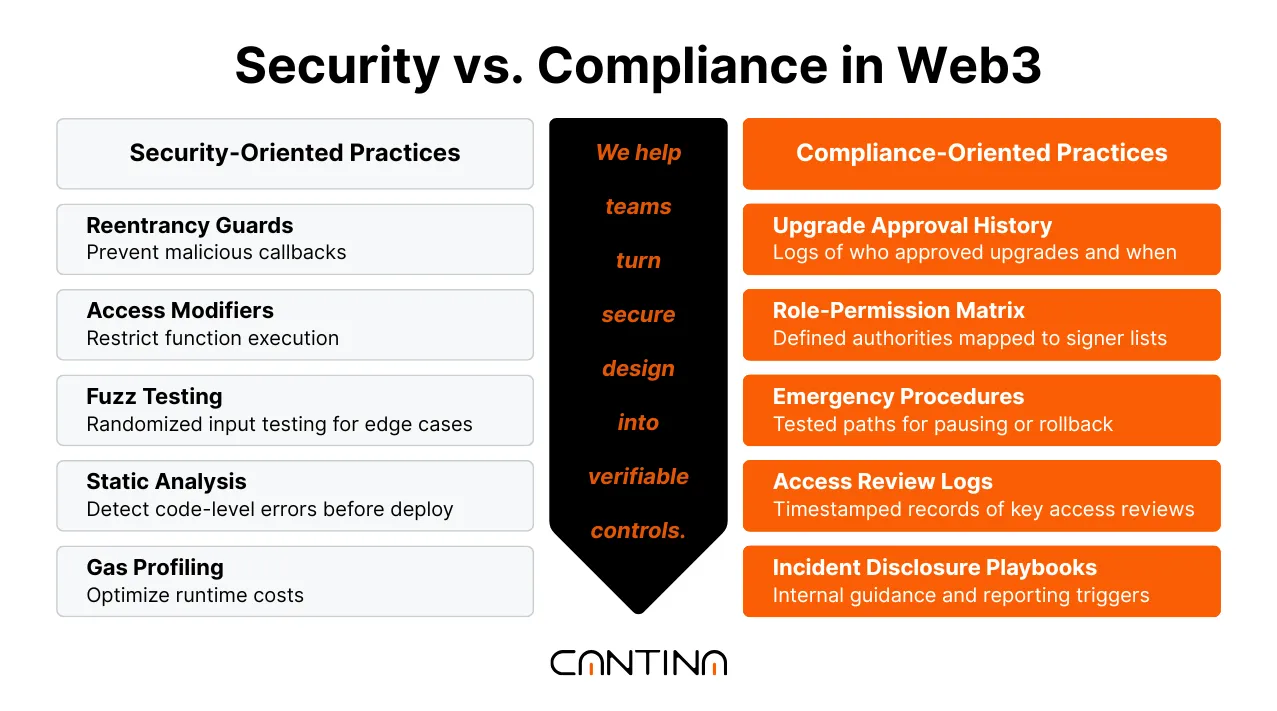
Security Fixes Risk. Compliance Demonstrates the System Is Effective.
Many smart contract security reviews focus narrowly on bugs, overlooking critical control signals that can lead to significant vulnerabilities. For institutional stakeholders, what matters is visibility into how authority is gated, how changes are approved, and how the system handles operational risk. These elements are often undocumented or buried in engineering workflows.
Regulators, institutional partners, and even larger DeFi users are increasingly asking these questions and not receiving satisfactory answers. Security work hasn’t kept pace with the types of scrutiny protocols now faced.
The primary difference between security and compliance lies in repeatability. Security helps prevent failure. Compliance demonstrates how a system responds to risk in ways that are testable and observable over time, across teams, and under stress. That means codifying roles, setting thresholds, tracking decisions, and demonstrating that the system behaves as the documentation states it should.
Most security reviews Still Miss What Reviewers Care About
The signals that most institutional reviewers rely on, such as deployment governance, upgrade procedures, access tracking, and kill-switch logic, are often missing from security reviews. Without this visibility, it’s difficult to assess whether a protocol is operationally sound or institution-ready. These are the same things that legal and risk teams look for when reviewing protocol infrastructure and the same things that most security review reports often overlook.
This gap in structured documentation forces legal and compliance teams to dig into raw code or audit logs, slowing down diligence cycles and increasing uncertainty during integration or review. That slows down integrations, increases legal friction, and creates gaps in institutional readiness even for technically sound systems.
Instead of just fixing issues, teams need security review outputs that demonstrate how risk is being managed on-chain, including signer permissions, change approvals, emergency paths, and role assignments. Not hypothetical controls, real ones, reflected in code and commit history.
Cantina helps teams build that visibility into their security review process. We work with protocols to map control logic to actual expectations, MiCA, DORA, SOC 2, and more, so reviewers see signals they recognize. No rewrites, no workarounds, just clearer structure around what’s already there.
Smart Contract Systems as Embedded Compliance Architecture
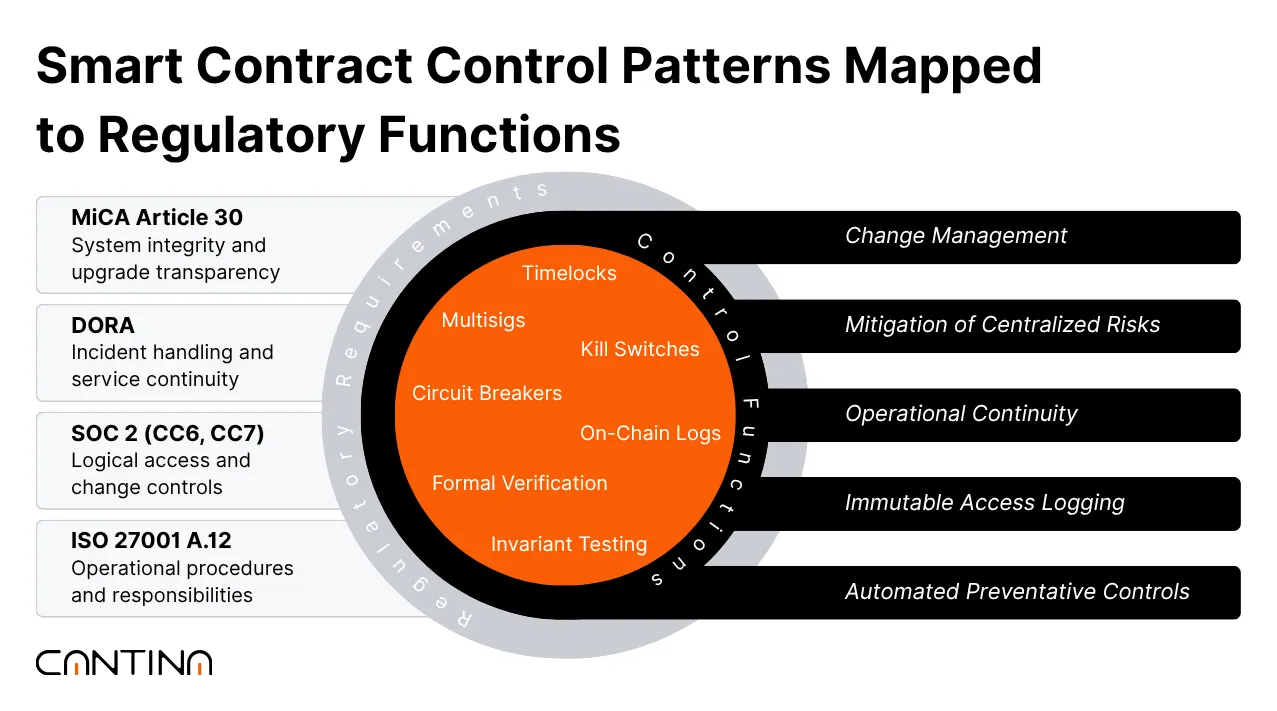
Compliance-by-Code Design Patterns
Smart contracts already handle a significant portion of the operational work that compliance reviewers are concerned with. Timelocks, multisigs, and kill switches directly support change control and reduce centralized risk, two of the most common flags in institutional diligence.
These mechanisms show how upgrades are gated, how authority is distributed, and how decisions get surfaced before they’re executed. When mapped clearly, they serve both the engineering team and the external reviewer.
Emergency pause functions and circuit breakers help protocols react without chaos. They give teams a defined path to stabilize systems when something goes wrong.
When those controls are tested, logged, and connected to roles or thresholds, they support expectations found in frameworks like DORA. On-chain logs and security review events, when structured well, act as immutable records of who did what and when. Formal verification or invariants can act as automated controls, catching violations before they become real-world issues. The patterns are already there; they just need to be made visible.
Cantina’s Framing for Compliance-Minded Reviews
Most protocols don’t need to re-architect their contracts; they just need to demonstrate. Protocols don’t need to be rebuilt; they need to be demonstrated. Cantina works with teams to surface how existing controls align with frameworks like MiCA, DORA, and SOC 2, in formats institutional reviewers can easily understand and verify. Cantina works with teams to build a “controls registry” that documents each contract’s alignment with external requirements.
It’s versioned alongside the codebase and lives beyond the security review. This way, everyone from legal to engineering is working from the same reference point, with clear links between contract behaviors and compliance frameworks like SOC 2, ISO 27001, or MiCA Article 30.
This creates institutional legibility, as legal and risk teams can evaluate the protocol’s governance structure directly, without having to sift through technical artifacts. It reduces ambiguity and accelerates trust. And third-party reviewers see controls that match their expectations, without having to decode a raw security review report. We help protocols bring compliance and security together, without adding overhead, just more structure around what’s already working.
Institutional Readiness: Building for GRC, Not Only Exploit Defense
What Institutional Reviewers Should Expect from Protocol Teams
Protocols engaging with regulated partners or entering formal integrations should be able to demonstrate operational control, not just technical correctness. That includes clearly defined signer roles, historical deployment records, and documented upgrade authority. These are baseline indicators of governance maturity, not optional details.
Incident procedures should also be traceable. Institutional reviewers should expect to see versioning history, emergency response playbooks, and records of how authority is distributed across roles or multisigs. Without that visibility, it's difficult to assess how a protocol manages real-world risk or handles fault scenarios under pressure.
How Deployment Practices Translate into GRC Readiness
Protocols may have secure infrastructure, such as CI/CD gating, access controls, and signer records, but without clear framing, these controls aren’t usable in GRC evaluations. Institutional teams often encounter well-architected systems that still fail due diligence due to a lack of traceability. Without framing, engineering hygiene doesn’t translate into a GRC signal.
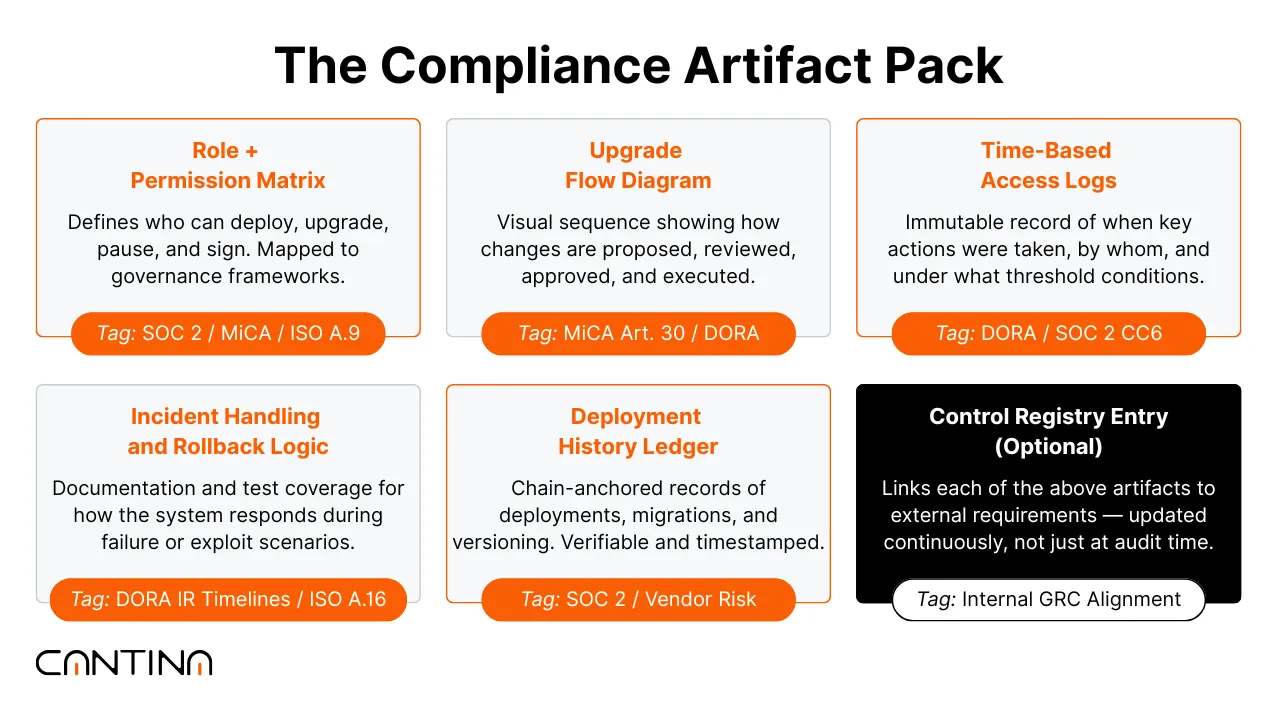
Cantina structures these underlying signals into Compliance Artifact Packs, which include permission matrices, upgrade timelines, and incident-handling documentation that map directly to regulatory expectations.
During security reviews, we work with protocol teams to produce a Compliance Artifact Pack tailored to governance, risk, and compliance stakeholders. This includes a permission matrix, access timelines, upgrade flow documentation, and incident-handling logic based on actual system behavior.
These artifacts create a direct path for legal and risk teams to evaluate protocol readiness. They support vendor risk reviews, map cleanly to frameworks such as SOC 2 and DORA, and reduce ambiguity around operational controls. When these signals are structured and verifiable, institutional teams can engage more efficiently, without slowing down protocol velocity.
Operationalizing the Compliance Bridge Across Functions
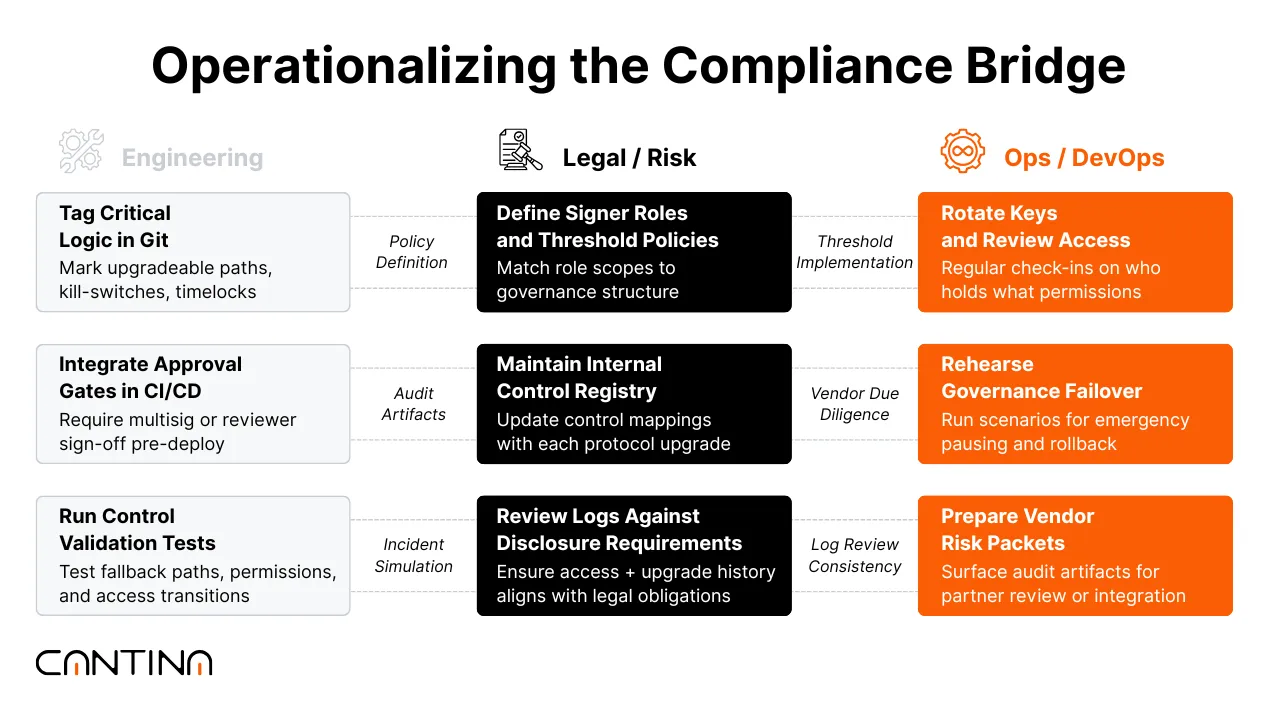
Why Cross-Functional Alignment Matters
Smart contract systems operate across technical, legal, and operational domains. For institutions conducting diligence or preparing for integration, those domains need to be coordinated. Engineering teams implement the control logic.
Legal teams are tasked with interpreting how those controls map to external obligations. Operations teams are responsible for keeping everything current, traceable, and aligned with day-to-day system behavior.
When technical, legal, and ops teams lack alignment, reviewers are left with blind spots. Without clear documentation and consistent control mapping, it’s impossible to verify how authority is distributed or how decisions are enforced in practice.
The law can’t defend what isn’t visible. Ops can’t maintain controls that aren’t documented. And engineering teams end up fielding compliance questions late, after the code is live.
This misalignment slows down integration timelines and introduces risk. For institutional teams, alignment across these roles is a foundational requirement for trust and scale.
How Cantina Supports Structured, Reviewable Coordination
Cantina collaborates with protocol teams to design their control systems in a manner that supports institutional requirements from the outset. Security review outputs aren’t just technical artifacts; they’re formatted to feed internal compliance programs, external certifications like SOC 2 or ISO 27001, and partner/vendor risk assessments. The work happens during the security review cycle, not as an afterthought.
In practice, that includes tagging sensitive logic in code, aligning security reviews with incident response plans, and supporting governance dry runs with verifiable logs.
We also help teams embed control validation directly into their CI/CD pipelines, including versioned runbooks, approval thresholds, and dashboards that display the live control state.
These outputs provide legal and operations teams with a consistent view of protocol maturity, reduce interpretation gaps, and accelerate institutional decision-making.
Conclusion
With regulatory expectations rising, protocols that cannot demonstrate operational controls across access, upgrades, and incident response will face increasing friction, regardless of how technically sound their systems are. The architecture for compliance is often already in place. Smart contracts encode governance, permissions, and decision paths. The challenge is structuring those elements into something that legal, risk, and operations teams can evaluate. Cantina helps institutional stakeholders see what matters: verifiable control structures, consistent security review outputs, and alignment with frameworks like MiCA, DORA, and SOC 2. We partner with protocol teams to surface the right signals, without compromising their decentralization.
If you're conducting diligence or preparing for integration, we're available for structured reviews. Let’s explore how your systems map to the requirements that matter.
FAQs
What does institutional compliance mean for smart contract security?
Institutional compliance in smart contracts involves demonstrating how access, upgrades, and incident responses are governed and logged, rather than just verifying the security of the code. Institutions expect control structures that are reviewable and aligned with frameworks like MiCA, DORA, and SOC 2.
How can smart contracts meet regulatory expectations without centralizing control?
Smart contracts can meet compliance needs by utilizing existing patterns, such as timelocks, multisignatures, and on-chain logs. These features, when structured and appropriately documented, show distributed authority and operational accountability without requiring centralized intervention.
What are compliance signals in a smart contract system?
Compliance signals are design patterns and security review artifacts that demonstrate how a protocol handles governance, access, and operational events. Examples include access logs, role definitions, upgrade procedures, and formal verification tied to real controls.
Why aren’t traditional smart contract security reviews enough for institutional readiness?
Traditional security reviews often focus on technical bugs but overlook controls like signer roles, incident workflows, and permission tracking. Institutions require clear evidence that risk is managed in a repeatable and reviewable manner, which is often lacking in technical-only security reviews.
How does Cantina support compliance for protocols integrating with institutions?
Cantina works with teams to structure their smart contract security into security review outputs that legal, risk, and ops teams can use. We package technical reviews into Compliance Artifact Packs, making it easier to pass diligence and align with governance standards, without changing how protocols operate.