Introduction
Web3 security in 2025 reflects an environment shaped by iteration, reuse, and growing system complexity. Protocols increasingly rely on shared components. Infrastructure becomes modular. Tooling abstracts critical logic. In this context, attackers no longer need novel exploits. A single overlooked entry point is sufficient to compromise large systems.
More than $2.3 billion in losses have already been recorded in 2025. These losses trace back to a small set of persistent weaknesses. They are known to experienced reviewers. The challenge lies in identifying them within the evolving architecture of today’s protocols.
Spearbit conducts deep reviews across diverse codebases and security surfaces. Our goal is to surface vulnerabilities before they are exploited. The following vectors represent patterns observed repeatedly across high-impact projects.
Eight Security Vectors We See Across Protocols
Overview of Key Vectors
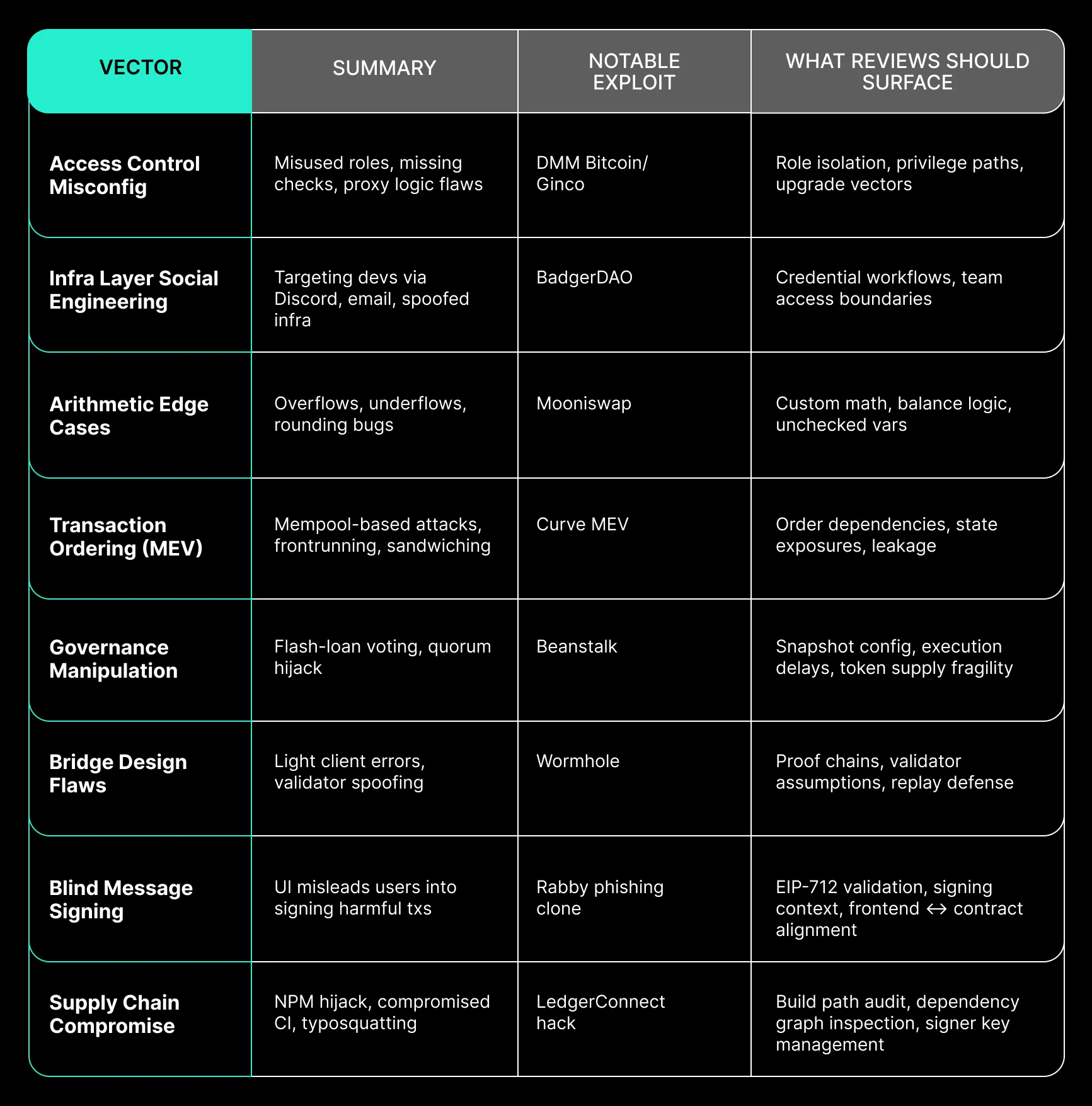
Access Control Misconfigurations
Large-scale breaches often stem from insufficiently scoped control over privileged functions. Whether through misplaced role logic, upgradeable contracts, or unclear ownership structures, adversaries exploit incorrect assumptions about access.
In security review, we trace the execution context of privileged operations. We verify separation of roles, evaluate the upgrade pattern, and map any mismatch between intended authority and actual control flow.
Social Engineering at the Infrastructure Layer
Adversaries increasingly target developers, infrastructure teams, and support staff. Social engineering operations impersonate trusted platforms or individuals to extract credentials or deploy malicious payloads. These attacks do not depend on contract-level vulnerabilities. They succeed by compromising the workflows around deployment and access.
Our review includes an analysis of communication channels, access patterns, and operational practices. We identify where trust is implicit and verify how access is provisioned and revoked across the development lifecycle.
Arithmetic Edge Cases
Arithmetic vulnerabilities, such as overflows, underflows, and rounding errors, still appear in critical applications. These errors often arise from gas optimizations, unchecked low-level operations, or nonstandard math implementations. The impact is magnified when calculations affect token balances, rewards, or collateral ratios.
Reviews involve both formal and adversarial analysis of arithmetic logic. We model edge cases and simulate how minor deviations can affect outcomes in high-volume or time-sensitive systems.
Transaction Ordering and MEV Exposure
Protocols that rely on transaction order for correctness face consistent threats from MEV exploitation. Public mempools expose timing-sensitive mechanisms to frontrunning, sandwiching, and state manipulation. These vulnerabilities affect auctions, liquidity incentives, and on-chain execution pathways.
We assess reliance on ordering guarantees, identify critical paths dependent on transaction sequence, and simulate interactions from the perspective of a MEV-aware adversary.
Governance Manipulation via Token Dynamics
Token-based governance introduces timing windows for manipulation through flash loans, liquidity concentration, or snapshot mismatches. Protocols with minimal quorum thresholds or poor separation between proposal and execution phases remain susceptible.
Our reviews evaluate the structure and implementation of governance logic. We focus on how governance power is distributed, how votes are executed, and how execution is gated to mitigate short-term control.
Bridge and Cross-Domain Design Flaws
Bridge infrastructure continues to present systemic risk. Common issues include light-client verification errors, incorrect validator set assumptions, and timing mismatches between chains. The implications often span multiple ecosystems and affect downstream integrations.
We audit the cryptographic assumptions of bridging systems, review how messages are validated across domains, and verify that replay and spoofing protections are applied consistently.
Blind Signing and Auth Layer Mismatch
Many user-facing applications continue to rely on ambiguous message signing. Adversaries exploit users' inability to interpret opaque payloads, prompting approval of harmful actions that bypass on-chain controls.
We evaluate how signing flows communicate intent, how frontend and contract logic remain synchronized, and how users are positioned to make informed approval decisions.
Supply Chain Compromise
Development environments remain vulnerable to dependency hijacking, compromised CI pipelines, and improper key management. These attack paths target the release process directly, bypassing even well-secured contracts.
Our reviews examine the integrity of build systems, package dependencies, deployment workflows, and the handling of sensitive credentials throughout the delivery chain.
3. Why These Patterns Persist
These vectors remain active because many security reviews focus narrowly on contract-level correctness. Broader architecture, system interaction, and operational behavior often receive less scrutiny. As protocols evolve and teams scale, security models must account for implicit trust, system composition, and the interfaces between components.
Adversaries evaluate systems holistically. Security review should do the same.
4. What We Prioritize in Review
Spearbit reviewers are selected based on domain expertise. Each review includes architectural analysis, threat modeling, and simulation of practical attack scenarios. Our process considers not only how contracts are written, but how they are used in context.
We include evaluations of:
- Architecture and upgradeability
- Role definitions and access patterns
- Governance mechanisms and execution paths
- Deployment and CI infrastructure
- Frontend and signature workflows
- Integration boundaries and external dependencies
5. Final Notes
The most common vulnerabilities are well understood. Exploits in 2025 repeatedly target known issues with access control, governance, transaction ordering, and operational exposure.
Security maturity is measured by how thoroughly teams identify and address these risks. Spearbit supports protocols that seek depth, not confirmation. If your project needs full-surface review, our approach is aligned. Contact us to strengthen your security posture.




