The financial landscape is undergoing a profound transformation driven by the rise of tokenization, the process of converting rights to real-world assets (RWAs) into digital tokens on blockchain networks. This innovation promises to unlock trillions of dollars in liquidity, improve transparency, and democratize access to investment opportunities. However, as tokenized assets proliferate, they bring new regulatory and security challenges that must be expertly addressed to safeguard investors and foster mainstream adoption.
In this article, we explore the evolving regulatory framework in the European Union (EU), discuss emerging token standards designed for compliance, examine the growing risks of digital asset theft, and explain how advanced security services, especially those provided by Cantina, are essential to securing the future of Web3 projects, particularly for institutions entrusted with safeguarding substantial digital wealth.
The Promise and Challenge of Tokenization
Tokenization offers significant advantages:
- Fractional Ownership: Dividing high-value assets into smaller, tradable digital units.
- Increased Liquidity: 24/7 global marketplaces enable continuous trading.
- Efficiency: Reduced reliance on intermediaries lowers costs and settlement times.
- Transparency: Blockchain’s immutable ledger ensures auditability and traceability.
Industry forecasts predict the global tokenized asset market will exceed $16 trillion by 2030, underscoring the enormous opportunity, and the imperative for robust, compliant frameworks.
Navigating the EU Regulatory Landscape
Dual Regulatory Regimes: MiCAR and MiFID II
In the EU, tokenized assets navigate a complex dual regulatory regime:
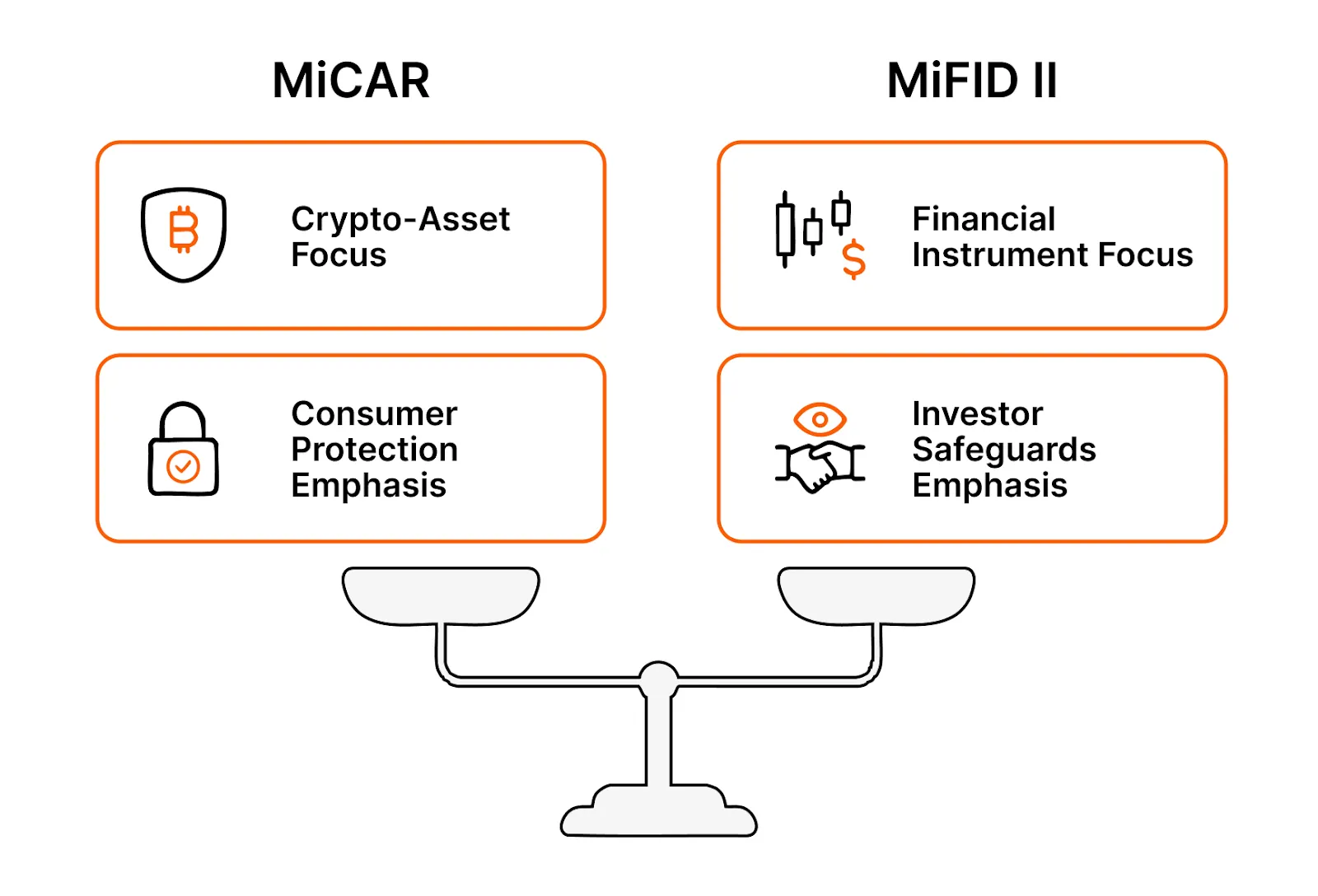
MiCAR (Markets in Crypto-Assets Regulation): A harmonized framework for crypto-assets not classified as financial instruments, improving consumer protection and market integrity.
MiFID II (Markets in Financial Instruments Directive II): Governs financial instruments with stringent transparency and investor safeguards.
The overlap requires token issuers, platforms, and investors to precisely determine which regulations apply, creating complexity that demands expert legal and technical guidance.
Impact on Token Standards
Token standards are evolving beyond basic fungible tokens to embed compliance features directly:
- KYC/AML Integration: Ensuring tokens are held and transferred only by verified participants.
- Transfer Restrictions: Enforcing jurisdictional and regulatory limits on secondary trading.
- Governance and Disclosure: Encoding rights and obligations within the token itself.
Standards like ERC-1400, ERC-3643 (T-REX), and CMTAT illustrate this trend toward compliance-centric token design.
The Growing Threat Landscape: Securing Digital Assets
The Inherent Risk of Digital Ownership
Digital assets operate as “bearer instruments,” meaning control of the private key equates to ownership. This model provides unparalleled financial sovereignty but also introduces significant risk — loss or theft of keys results in irreversible asset loss.
High-Profile Heists and Sophistication of Threats
From the infamous Mt. Gox hack to the recent $1.5 billion ByBit breach, the industry faces escalating cyber threats. Attackers employ advanced techniques including:
- Smart contract exploits
- Advanced persistent threats
- Social engineering and phishing
The digital asset ecosystem must prepare for a potential “trillion-dollar heist” unless security defenses improve dramatically.
Institutional Custody and Best Practices
Institutions managing large asset pools rely on regulated custodians offering:
- Segregated, bankruptcy-remote custody wallets
- Multi-signature controls
- Insurance coverage
Complementing custody, rigorous security reviews and penetration testing are vital to identify vulnerabilities before they are exploited.
Web3 Projects and Financial Institution Security Reviews
To gain institutional trust and comply with financial regulations, Web3 projects must undergo thorough security reviews that include:
- Manual and automated smart contract reviews
- Infrastructure penetration testing
- Compliance and regulatory alignment checks
- Continuous vulnerability monitoring
Such comprehensive reviews ensure resilience against sophisticated threats and demonstrate a commitment to industry best practices.
Cantina: The Security Partner for a Safe and Successful Web3 Ecosystem
In this environment, Cantina stands out as a critical ally for projects and institutions alike. Cantina’s global network of elite security researchers delivers world-class reviews and penetration tests tailored specifically for Web3 protocols.
Why Cantina?
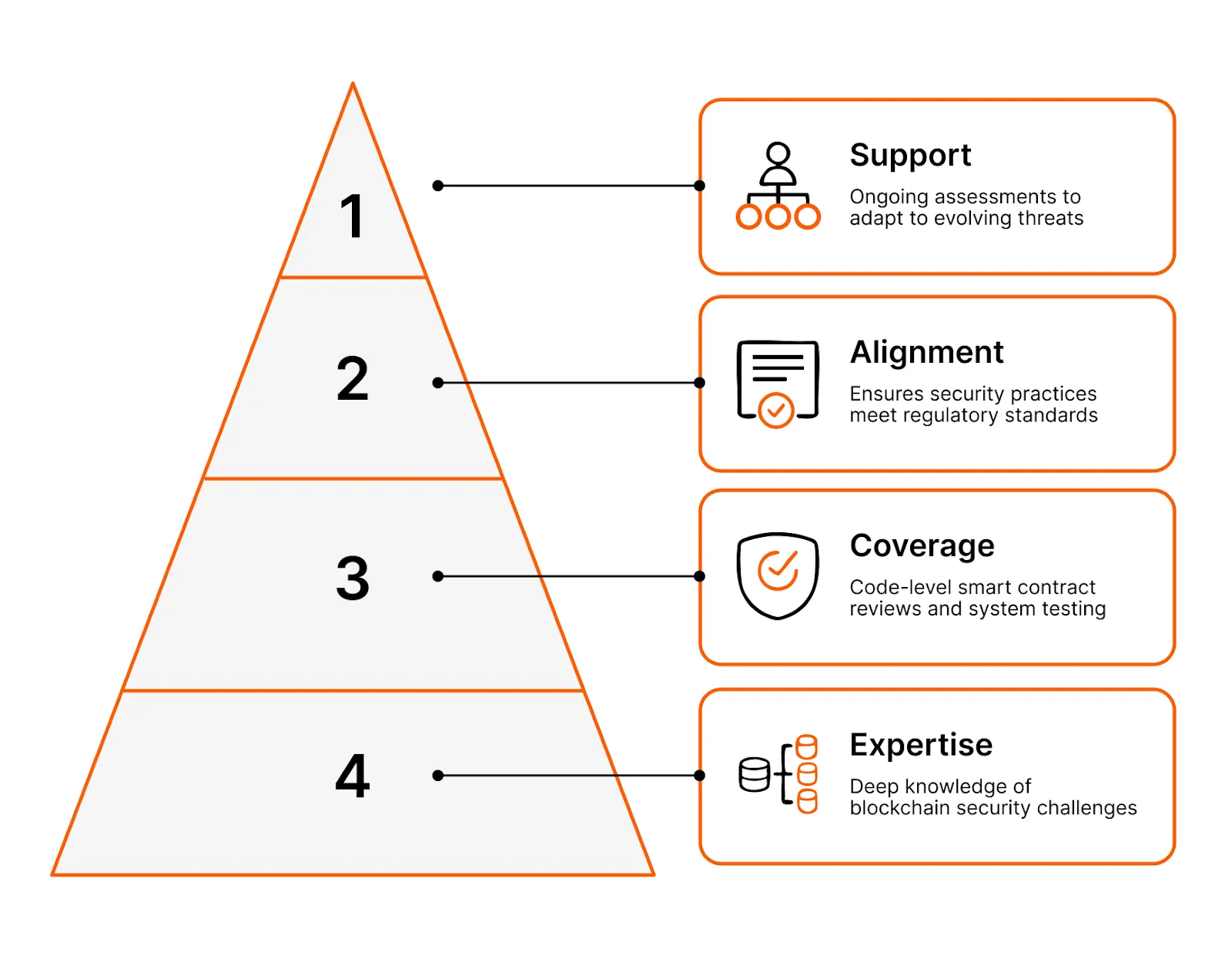
For institutions managing billions in digital assets, partnering with Cantina is not just prudent, it’s essential. Cantina’s rigorous security processes help prevent costly breaches, protect investor confidence, and support regulatory compliance, ultimately fostering sustainable growth.
A Roadmap for the Future: Integrating Tokenization, Compliance, and Security
To realize the full potential of tokenized assets, projects must:
- Develop compliance-ready token protocols that embed regulatory requirements.
- Engage expert security researchers like Cantina to harden smart contracts and infrastructure.
- Leverage regulated custodians for secure asset storage.
- Stay agile by aligning with evolving regulatory frameworks.
- Foster industry collaboration to share best practices and threat intelligence.
This integrated approach will protect trillions of dollars in digital assets and build the trust necessary for widespread adoption.
Conclusion
Tokenization is revolutionizing finance, but without strict adherence to regulatory compliance and rigorous security practices, the risks are immense. Cantina’s cutting-edge security solutions empower Web3 organizations and institutions to meet these challenges head-on, safeguarding assets, ensuring regulatory alignment, and enabling healthy, successful ventures.
If you are leading a Web3 project or institution seeking to secure your digital assets with trusted, expert support, don’t leave your security to chance. Request a quote today, and receive a tailored proposal in 24 hours.




