As the Web3 ecosystem matures, expectations around security have evolved beyond reactive patching or late-stage auditing. Organizations now face the responsibility of treating security as a continuous discipline that spans protocol design, infrastructure, and governance. At the center of this shift is the principle of zero vulnerability, a proactive approach to minimizing attack surfaces across every layer of a blockchain system.
This blog outlines the concept of zero vulnerability, how it applies to modern Web3 protocols, and what organizations must do to embed it within their development and operational lifecycles.
Understanding Zero Vulnerability in Web3
Zero vulnerability does not imply a guarantee of perfect security. Instead, it describes a security posture where all known risks are addressed systematically through verification, enforcement, and constraint. It reflects an approach driven by prevention, not reaction.
A zero vulnerability posture is defined by:
- Embedding security thinking from specification to production
- Employing formal methods to validate assumptions and invariants
- Treating every commit, parameter, and dependency as a potential entry point
This framework aligns with an institutional-grade mindset, where trust is earned through proof and observability, not just claims of coverage.
Foundational Pillars of a Zero Vulnerability Architecture
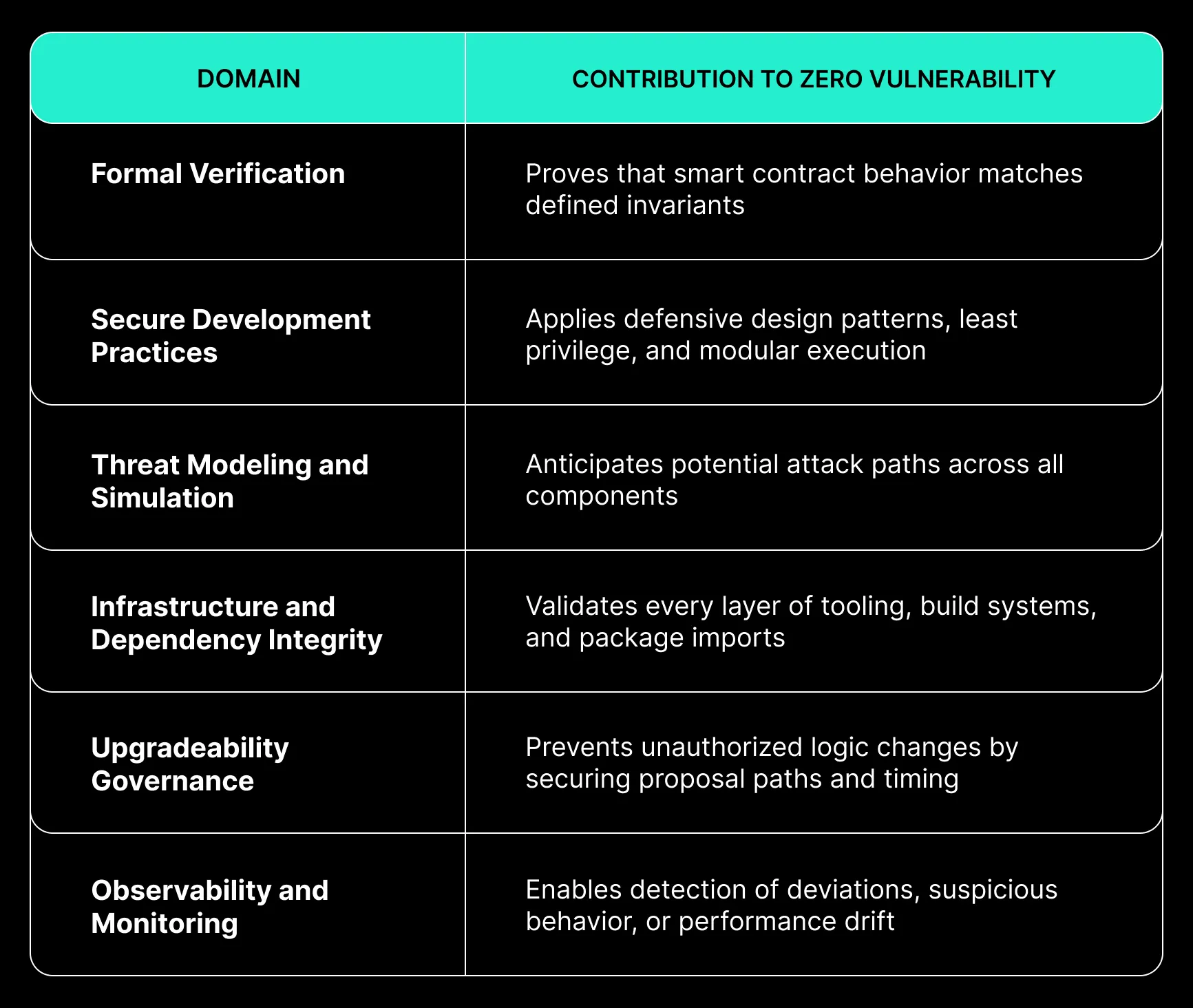
Designing With Zero Vulnerability in Mind
Adopting a zero vulnerability posture begins during protocol architecture. Security reviews at this stage emphasize:
- Defining what must always be true through system invariants
- Identifying where power concentrates and how to enforce constraints
- Modeling edge cases around economic behavior and privilege boundaries
- Designing fail-safe behavior in the presence of degraded components
Instead of auditing after implementation, security validation becomes part of the design conversation itself.
Sustaining a Zero Vulnerability Posture in Production
Zero vulnerability is an operational commitment. Once deployed, protocols must continuously enforce the same level of scrutiny through:
- Infrastructure hardening and isolation of privileged keys
- Secure build pipelines and reproducible deployment processes
- Real-time monitoring of governance, upgrade proposals, and network behavior
- Attack simulations that explore privileged actor compromise, multisig misuse, and liveness challenges
Without this coverage, even verified systems can become vulnerable due to environment-level breakdowns.
Establishing Zero Vulnerability as an Industry Standard
Zero vulnerability is not a branding claim. It is a measurable standard that reflects architectural intent, technical execution, and operational maturity.
Spearbit supports protocols and organizations pursuing this posture through:
- Protocol-level threat modeling and risk design audits
- Governance simulation and upgrade safety analysis
- Infrastructure audits focused on CI/CD, key custody, and validator behavior
- Incident response planning and resilience testing
Security is not an event. It is a discipline. The protocols that scale successfully in the next cycle will be those that treat security as integral.
Building Secure Systems With Spearbit
To move toward a zero vulnerability posture, protocols must commit to deeper validation and stronger design principles across all layers. This includes development, governance, infrastructure, and recovery planning.
Spearbit provides lifecycle-aligned security engagements designed for this standard. We work with organizations to define, validate, and maintain systems that meet institutional expectations for resilience, trust, and control.
Contact Spearbit to discuss a tailored engagement focused on formal security foundations, operational readiness, and protocol integrity.




