Introduction
zkVMs are live; organizations compile application logic into circuits, generate proofs from inputs, and verify them without re-executing code. Bitcoin is being integrated via relays that bring block headers and UTXOs into zero-knowledge (zk) environments, enabling direct state references. These systems are already executing in production. This article examines the interaction between zkVMs and Bitcoin, the risks associated with constraint-based execution, and how Spearbit evaluates circuits, compilers, and cross-chain integration.
The Technical Shift
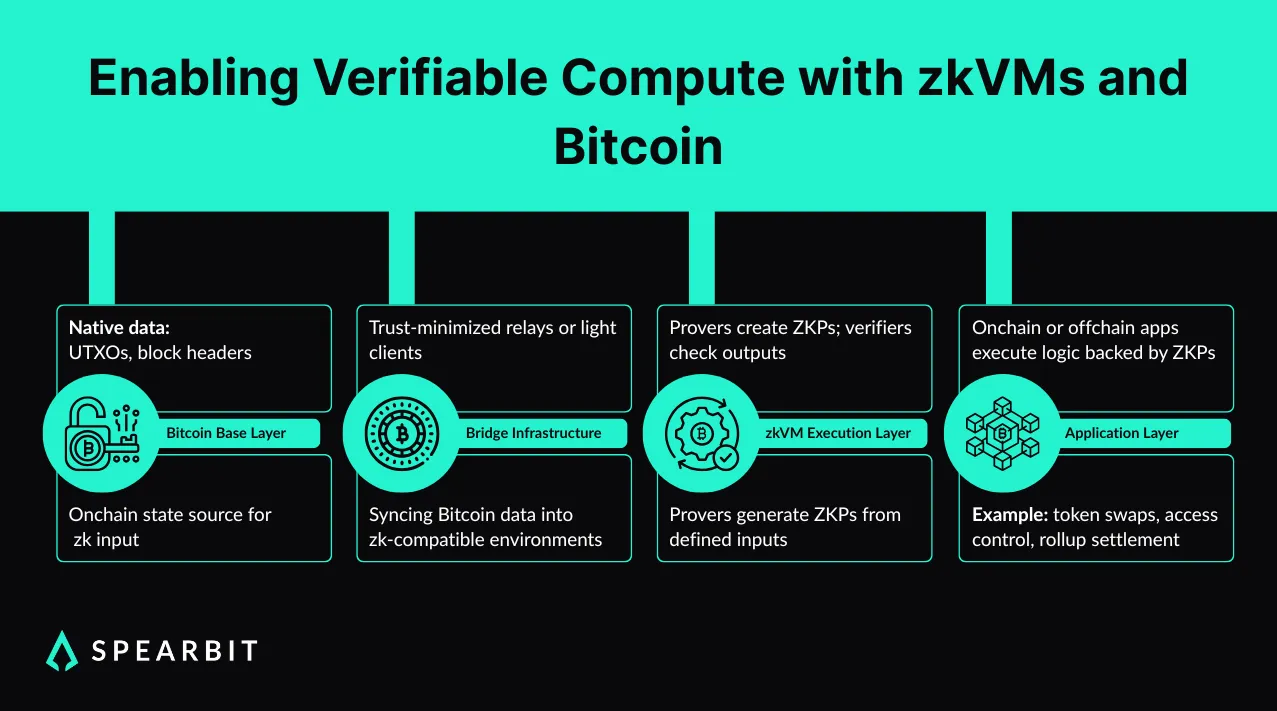
zkVMs generate succinct, cryptographic attestations that specific logic was followed during execution. Instead of interpreting bytecode at runtime, these systems reduce application logic, such as asset transfers, swap calculations, or bridge validation steps, into constraint systems.
When inputs are applied to those constraints, a proof is generated that attests to the validity of the outcome. This proof can then be verified independently, without rerunning the original logic.
Bitcoin is now being used as a data source within this framework. Block headers and UTXO sets are ingested into zk-compatible environments through light clients and relay protocols. In some implementations, this data is transmitted as compact commitments or via Merkle inclusion proofs rather than full headers, enabling efficient validation within zk circuits.
These components provide cryptographic commitments to Bitcoin's state, allowing zkVMs to reference and reason about Bitcoin data directly. Applications can then include Bitcoin-originating facts in proofs without wrapping assets or depending on custodial bridges.
These integrations are operational in early production deployments or limited rollouts, demonstrating that proof systems are already generating validity proofs tied to Bitcoin-linked inputs under live or quasi-live conditions. Some systems verify proofs on-chain, such as rollups like zkSync that use native verification contracts.
Others rely on off-chain validation, seen in trust-minimized relays, before transmitting results to the destination chain. Both models rely on correct proof construction but differ in who holds final verification authority.
Execution is no longer evaluated solely within a chain’s native virtual machine but can be validated externally using a cryptographic transcript of what occurred.
Security Risks in a ZK Execution World
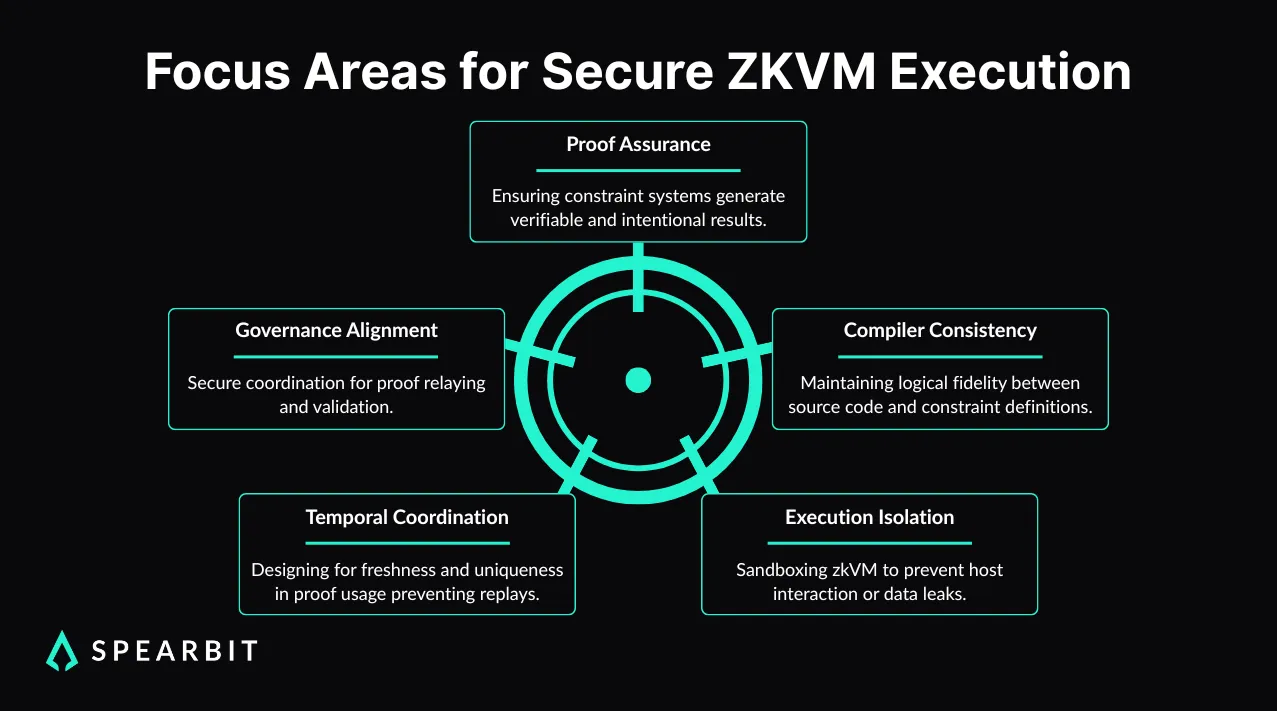
Proof integrity
A proof system is only sound if the constraint logic fully encodes the intended behavior. When a circuit is misdesigned, it may allow invalid transitions that still satisfy the constraints. These are not runtime bugs. The system verifies the proof successfully because the error lives in the structure of the logic itself, not in its execution.
This type of fault is particularly hazardous because it circumvents standard error detection mechanisms. There are no runtime signals to indicate a malformed result.
If a circuit fails to encode a required relationship or omits a boundary condition, the verifier will still return success. The system treats the proof as valid, even if it contradicts the developer’s assumptions.
Compiler trust
ZK compilers map high-level logic into constraint representations. This transformation introduces multiple layers of abstraction, including intermediate representations, optimization passes, and constraint flattening. A single error in any of these steps can distort the meaning of the original logic in ways that are difficult to detect post-compilation.
Because developers interact with the source language, they often assume the compiled constraint system preserves all logical relationships. That assumption can break down.
A misaligned constraint, a skipped assertion, or a reordered instruction can shift the behavior of the final proof. Without constraint-level inspection, these discrepancies go unnoticed until a live proof produces an outcome that deviates from the specification.
Isolation failure
zkVMs typically execute within bounded environments that restrict access to state and external interaction. These boundaries are implemented through call filters, resource quotas, and memory allocation constraints.
If any of these controls are incomplete or misapplied, the proving environment may allow access to state or functions outside its intended scope. In systems where the zkVM interfaces with bridge contracts or shared state verifiers, isolation guarantees matter.
A failure in sandbox enforcement may allow a malicious proof to trigger external logic or extract unintended state. This could compromise other contracts, leak information, or escalate access beyond what the proof was meant to authorize.
Liveness and replay risks
Systems rely on time-sensitive proofs to validate state transitions or authorize value transfers. These proofs often reference a specific block height, timestamp, or transaction root.
If there is a delay in generating or submitting the proof, the state may shift underneath it, making the original input set no longer valid or relevant.
Replay risk arises when proof consumption is not tightly tied to its context. Suppose an old proof is accepted in a later session due to missing replay protections such as nonces, unique proof identifiers, or time-bound commitments.
In that case, an adversary can reintroduce a valid but outdated action. Without explicit replay protection, the verifier may accept actions that were never intended to be repeated.
Relay governance
In ZK-based bridges or messaging layers, the correctness of a proof does not guarantee its timely submission. Relayers are often responsible for broadcasting proofs, coordinating sequences, and finalizing actions based on those proofs.
These relayers operate off-chain and may coordinate through multisigs, threshold signatures, or protocol-specific relay sets. The structure and transparency of these models influence reliability and censorship resistance. When relayer coordination lacks deterministic rules or sufficient fault tolerance, it opens the door to delay or censorship.
These risks can be exacerbated by weak economic incentives or latency gaps that degrade liveness and trust assumptions, especially in low-throughput or cross-domain deployments.”
This affects not only throughput but trust assumptions across chains. Even with valid proofs, the reliance on external agents for delivery and sequencing introduces non-cryptographic risks into the execution path.
Spearbit’s Security Perspective
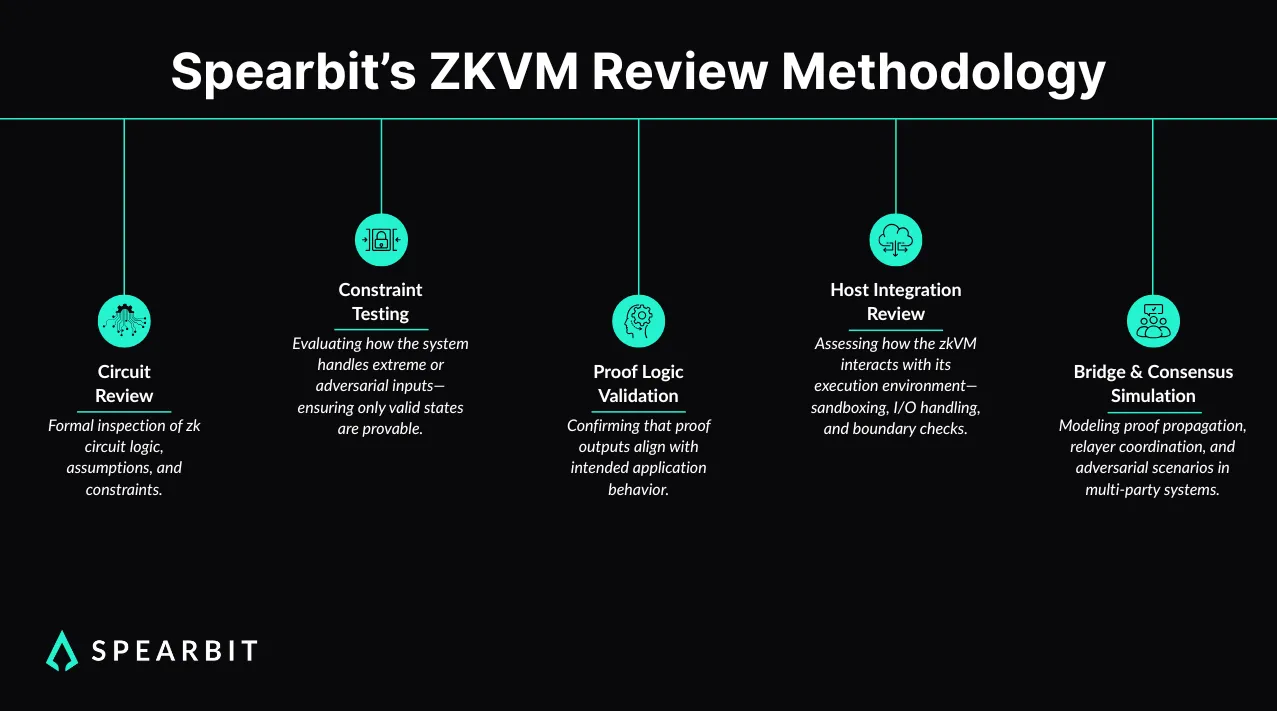
Spearbit works directly with teams building zkVM-based systems to evaluate how logic is encoded, how proofs are constructed, and how these systems interact with bridges and verifiers.
We focus on the boundaries where guarantees can break down due to design assumptions, translation layers, or incomplete isolation.
- Constraint-level circuit review: Reviews focus on how logic is encoded at the constraint level, covering edge cases, enforcing assertions, and aligning circuit behavior with expected outcomes.
- Proof behavior under adversarial conditions: Testing examines how proofs respond to malformed or manipulated inputs, including whether acceptance paths expose inconsistencies or gaps in enforcement.
- System integration with the zkVM: Evaluation includes input handling, boundary enforcement, and the potential for zkVM output to trigger unintended external behavior.
- Relay coordination and cross-system data flow: Analysis targets proof submission timing, relayer coordination, and the risk of replay or sequencing attacks in multi-party systems.
We treat security as a matter of how systems behave under pressure. That means reviewing logic not just for correctness, but for resilience under adversarial conditions. Our methodology is grounded in formal methods, real-world test cases, and simulation against realistic attack models.
Conclusion
zkVMs reshape the boundaries of verification, introducing new layers of proof logic, isolating execution from state replication, and creating new trust surfaces between chains and systems. As Bitcoin becomes part of this proving stack, the underlying assumptions must be understood and stress-tested. Spearbit collaborates with teams developing these systems to review circuits, test integration boundaries, and model how execution behaves when assumptions are challenged.
If you're building with zkVMs or integrating Bitcoin into verifiable compute, get in touch. We help teams secure what gets proven before it goes live.




