When smart contracts execute in unexpected ways, vulnerabilities can emerge. Reentrancy attacks remain one of the most dangerous examples, persisting as a critical threat since Ethereum's early days.
Modern reentrancy vulnerabilities take many forms, requiring both sophisticated detection methods and thorough security analysis to prevent exploitation. But how can we effectively identify and protect against these attack vectors? Let’s examine how.
Understanding the Core
Reentrancy occurs when a contract makes an external call and receives control again before the initial execution completes. If that happens while state is unsettled, logic that depends on accurate values can be manipulated.
This vulnerability appears during interactions with untrusted contracts. If internal balances or flags have not been updated before the external call, an attacker can exploit those values through callbacks or recursive paths.
Recognizing the Patterns
Common types of reentrancy include the following:
- Single function reentrancy
- Cross function reentrancy
- Cross contract reentrancy
Additional forms relevant to current systems:
- View based reentrancy
- Governance manipulation through recursive reads
- Price distortion using oracle fallback logic
Each of these involves assumptions that break due to execution timing. They become critical when intermediate values are used to inform actions or authorize outcomes.
Modern Attack Vectors in Practice
Modern contract systems expose reentrancy risk in areas such as the following
- Delayed state commits after early validation
- View logic consumed by downstream contracts
- Shared dependencies that allow callbacks
- Automation systems that chain contract interactions
These environments introduce paths where state is read and used before it is finalized.
Real World Example: Read Only Reentrancy in 2025
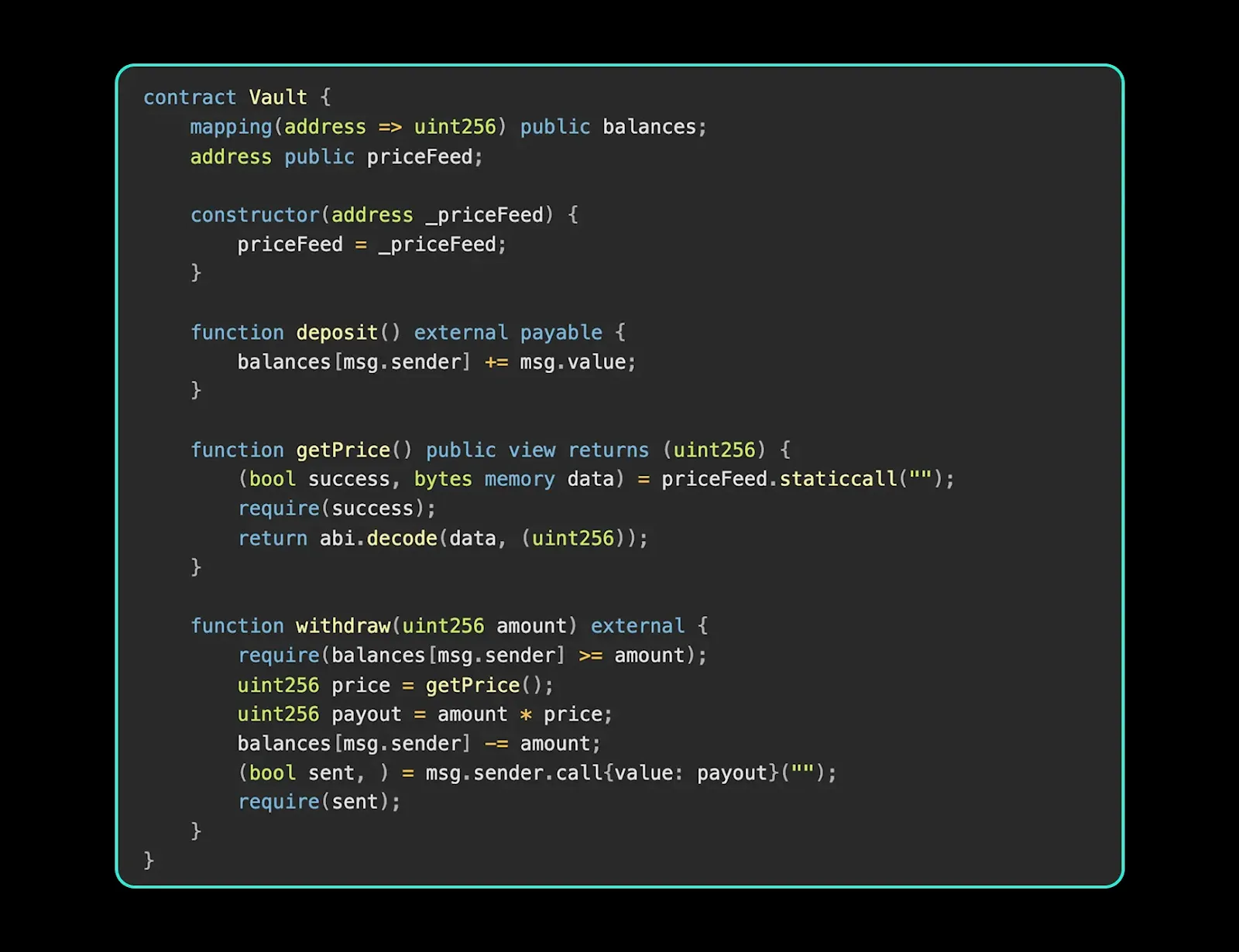
To illustrate how this type of vulnerability could manifest, consider a vault that performs a price check using a view function during withdrawals. An attacker could deploy a contract that initiates a standard withdrawal. During execution, when the vault queries the price via a view call, the attacker's contract could use a fallback function to manipulate the expected return value. This would cause the vault to complete the withdrawal based on incorrect pricing, potentially leading to significant asset miscalculation.
Vulnerable Vault
Exploit Contract
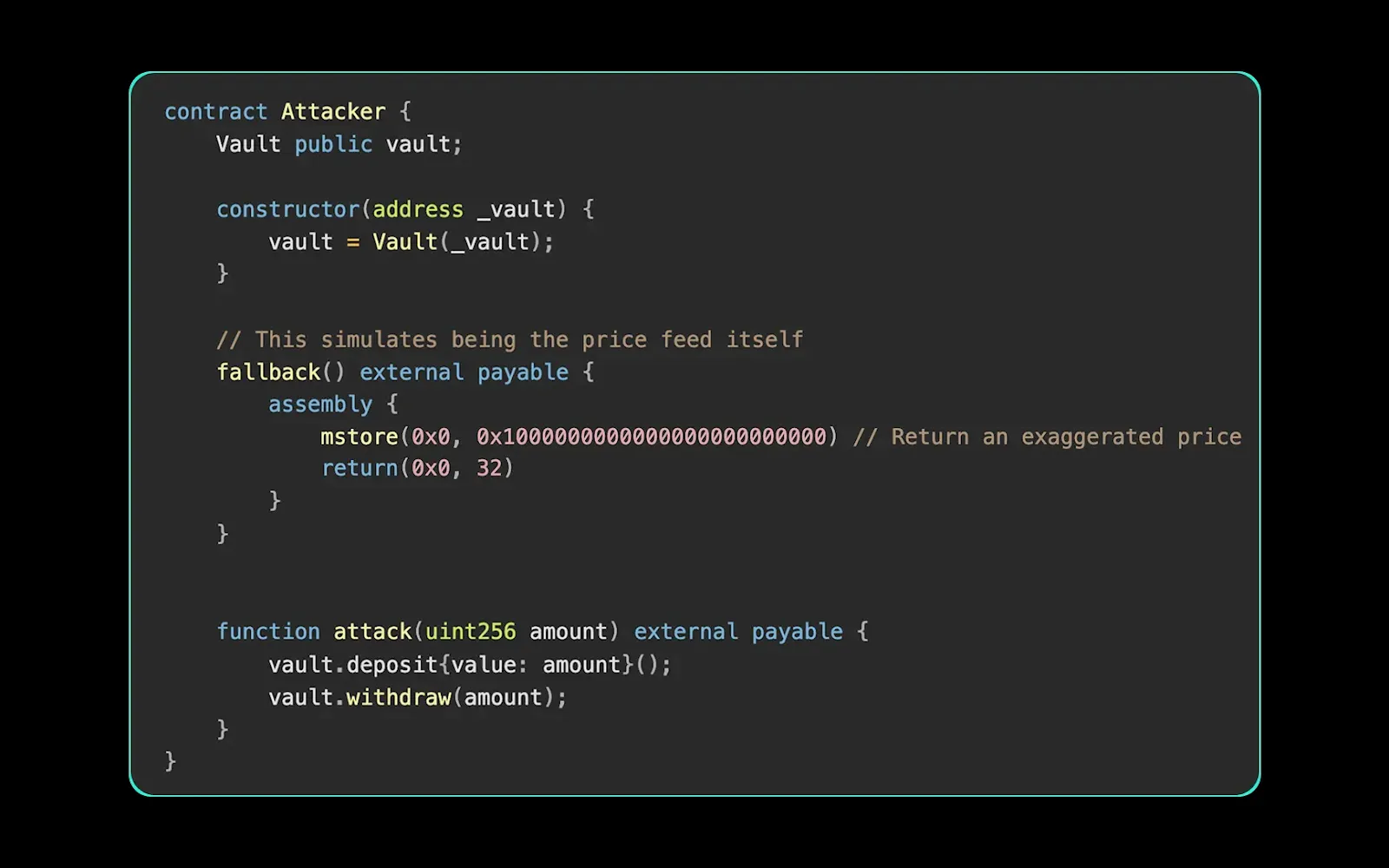
In this example, the attacker’s fallback returns a manipulated value when the vault performs a view call to determine pricing. The vault relies on this value to compute the payout. Because the manipulation happens within a staticcall, traditional protections like CEI or reentrancy guards do not apply, making this a subtle and effective vector.
Limitations of Automated Detection
Most tools detect signature reentrancy patterns. They alert when a function calls out before completing state updates. These detections are useful but incomplete.
Key limitations include the following
- Overreporting of low impact patterns
- No modeling of fallback triggered flows
- No visibility into view logic linked to core execution
Detection tools should not be treated as full analysis. Review teams must validate findings and simulate potential behavior.
High-Signal Reentrancy Review Strategy
Effective audits trace every execution path that touches external calls or depends on upstream data. This includes view functions that influence core logic.
Audit teams must test logic with simulated attacker contracts that call back into the system during execution. This helps confirm what state can be accessed and whether decisions rely on incomplete information.
Critical Areas for Reentrancy Assessment

Developer Side Defenses That Work
Reliable defenses require both design and enforcement. Recommended practices include the following
- Apply checks effects interactions consistently
- Use reentrancy guards on state dependent logic
- Prevent critical view calls during execution
- Harden shared components with controlled interfaces
- Confirm validation checks at point of execution
Spearbit's Approach to Reentrancy Detection
Spearbit's high-signal reviews use structured attacker modeling across execution states. We trace all inter-contract calls and simulate fallback-triggered reentry. View functions are treated as part of the security surface when they influence access or state transitions.
Each review includes • Execution mapping across all contracts in scope • Targeted simulation of fallback behavior during view logic • State tracking before and after external calls • Isolation testing of shared modules, proxies, and wrappers
Spearbit focuses on verifying assumptions through simulation, not pattern matching. This ensures conditions that could trigger reentrancy are identified, modeled, and mitigated.
What This Means for Reviews
Security reviews must simulate realistic attacker behavior. This includes timing manipulation, view logic access, and interdependent call flows. Pattern detection alone will not catch these scenarios.
Spearbit reviews simulate these behaviors directly. We model execution across fallback paths, trace logic into shared modules, and test view logic as if it were mutable. This approach reveals conditions that checklist based reviews miss.
Start a Spearbit security assessment today.




