Key Takeaways
- Symbiotic allows protocols to define validator coordination logic on their terms by combining modular vaults, permissionless operator opt-ins, and resolver-based slashing enforcement, without relying on a centralized validator set.
- Each integration can isolate validator behavior, incentives, and dispute mechanisms, making it possible to reuse infrastructure across services like rollups, AVSes, or DA layers without introducing shared risk.
- The system supports protocol-specific trust models, enabling teams to configure slashing enforcement and validator inclusion with precision, tailored to the needs of their respective networks.
Introduction
Symbiotic provides teams with a permissionless way to restake ERC-20 assets across networks without being locked into a fixed validator set. It's Universal Staking model lets you define how validators opt in, how slashing works, and how rewards are structured, fully scoped to the needs of your service. Modular architectures can define validator coordination with full control over inclusion, slashing, and rewards. The article outlines Symbiotic’s architecture, vaults, resolvers, and operator registration and explains how Spearbit’s expert reviews enhance security outcomes.
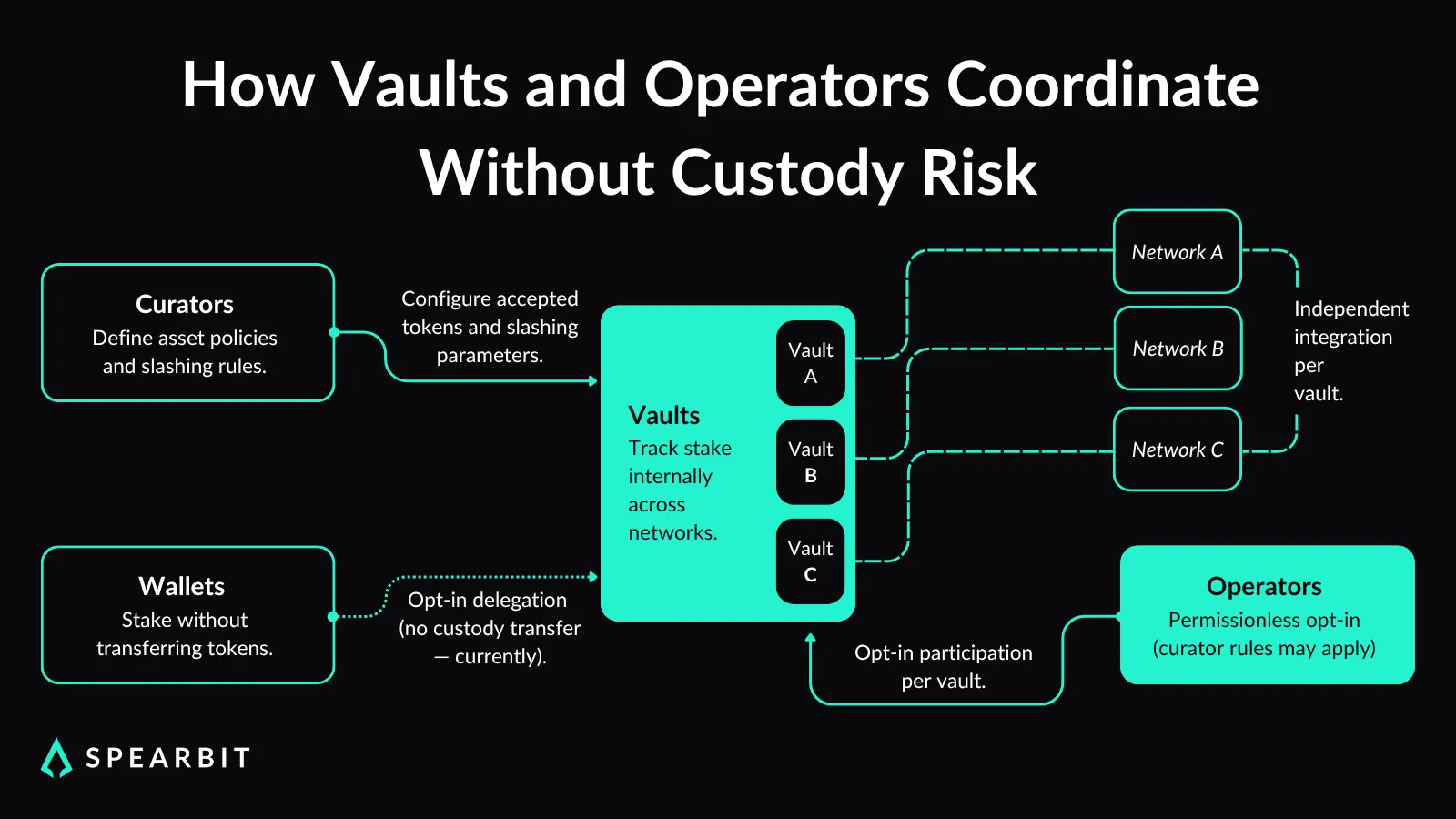
Vaults and Operators: Configurable Delegation Without Custodial Risk
Vault Mechanics and Multi-Network Utility
Vaults define how restaking works in Symbiotic at the asset and policy level. Curators define which ERC-20 tokens a vault accepts and configure reward distribution.
Slashing conditions are implemented through assigned slasher contracts, which can be set to FIFOSlasher, VetoSlasher, or None, and are responsible for executing enforcement logic, not the vault itself. Importantly, tokens don’t leave a user’s wallet. Symbiotic tracks stake internally using an accounting system, which avoids introducing custodial risk.
When someone opts into a vault, their stake goes through a configurable delay before becoming active. Once active, that stake follows the vault’s rules for slashing and rewards.
A single vault can be used across multiple networks or services. Each integration defines validator participation through a combination of curator-configured maxNetworkStakeLimit and operator-defined operatorNetworkLimit. These constraints determine stake bounds per operator-network pair, enabling shared validator infrastructure without requiring a global validator set.
Vaults expose data like stake status, operator allocations, and opt-in events. This helps networks and curators monitor what’s happening and build automation on top, whether that’s for alerts, rebalancing, or slashing workflows.
Operator Participation and On-Chain Coordination
Operators register themselves on-chain and opt into specific vaults or networks. There is no global validator list; each operator decides where to participate and under what terms. This provides networks with more flexibility to work with validators who meet their specific requirements.
Each operator has associated metadata, including their vault affiliations and other public details. Networks or curators can reference this when evaluating who to include or when writing conditions for validator eligibility.
There’s also a governance mechanism that can pause an operator in emergencies, but this doesn’t affect day-to-day participation. Operators retain full control over where they opt in and what they support, which makes the system more flexible for both new and existing validators.
Resolvers and Slashing: Programmable Enforcement and Arbitration Layers
Slashing Flow Across Vaults and Networks
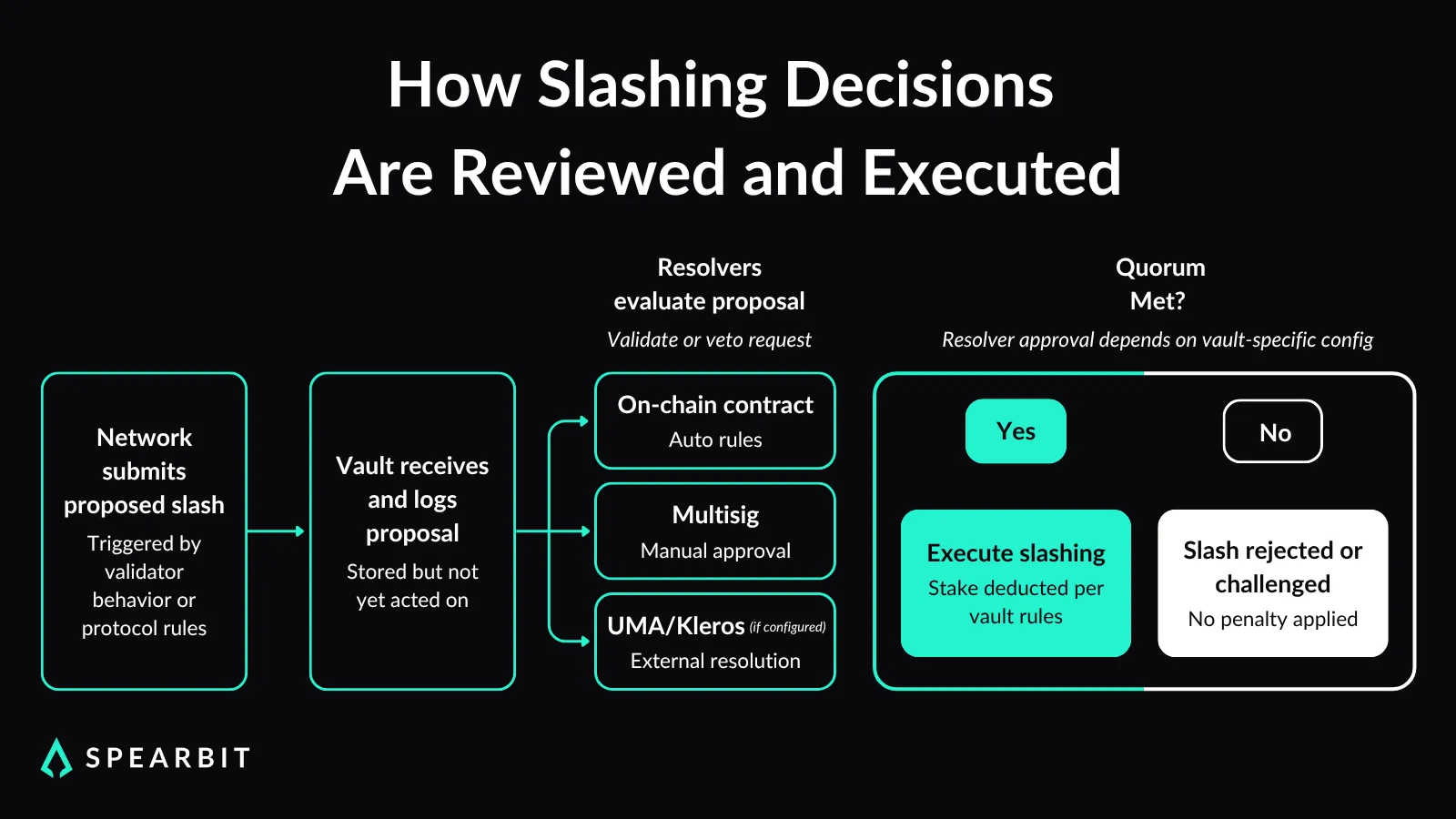
Slashing in Symbiotic starts at the network level. Each network defines its criteria for slashing and submits a proposal to the associated vault when those conditions are met. These proposals are not executed immediately. Instead, they are subject to review by resolvers tied to that vault.
Resolvers are responsible for reviewing or contesting slashing actions. They act as a validation layer between the slashing intent and actual enforcement. Each vault can be configured with one or more resolvers, and the outcome depends on the logic they follow.
Execution only proceeds once a resolver (or a quorum of resolvers) has confirmed the slashing proposal. This delay between submission and execution gives time for automated or manual validation and prevents unilateral slashing by networks without oversight.
Resolver Design Options
Resolvers can take multiple forms. They may be smart contracts, multisigs, or off-chain arbitration systems such as UMA or Kleros. The vault curator decides which resolver architecture is appropriate for their use case and configures the vault accordingly.
Vaults can support multiple resolvers simultaneously. Each resolver can be assigned a weight or role in the decision process. This modularity allows teams to build dispute resolution logic that aligns with their risk tolerance and operational complexity.
Slashing penalties are enforced per vault, meaning a validator penalized in one context does not automatically lose stake in others. This containment prevents unintended consequences across unrelated networks or services, allowing for clearer and more defined trust boundaries.
Vaults register slasher contracts via the VaultRegistry, assigning enforcement logic to modules such as FIFOSlasher, VetoSlasher, or disabling it entirely with None.
The Delegator contract handles the mapping between vaults, networks, and operators, linking stake to active services. This separation preserves vault-level autonomy while giving curators and operators fine-grained control over participation and enforcement rules.
Integration Patterns and Security Fit for High-Complexity Protocols
Service Design for Rollups, AVSes, DA Layers, and Beyond
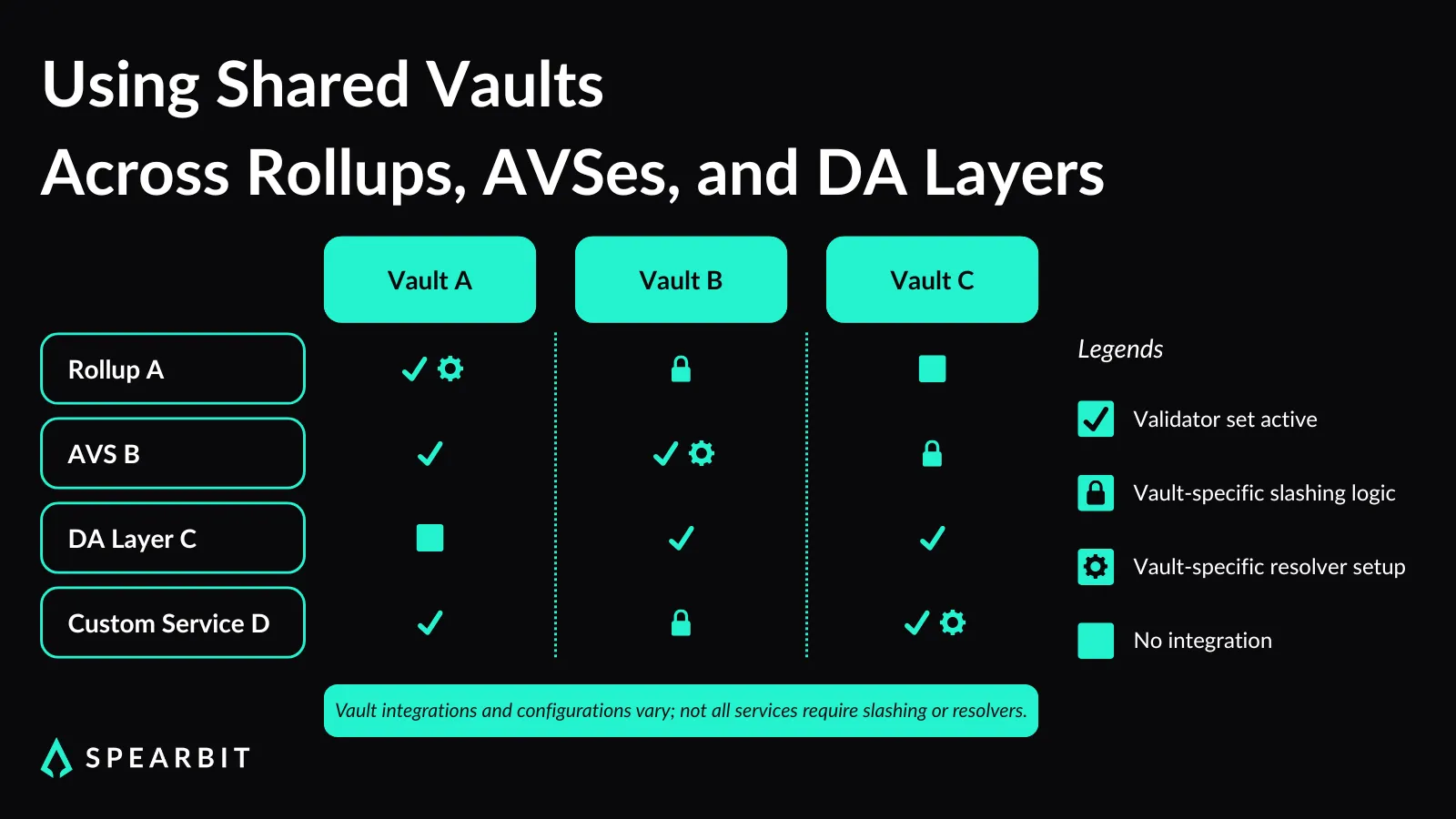
Symbiotic’s vault structure allows multiple services to share validator infrastructure without needing a unified slashing policy. Each service can configure its slashing conditions and resolver logic while using the same underlying vault. This reduces duplication and simplifies validator onboarding across services with different requirements.
Operators register per vault-service instance, not globally. This opt-in model gives validators control over where and how they participate. It also allows networks to select operators based on specific economic or technical preferences without affecting other services using the same vault.
Relay, as described in public Symbiotic documentation, is intended to support cross-chain verification by transmitting proof-of-stake-backed actions to other networks. While Relay is not yet live, its planned function would extend the utility of vaults and resolvers to services operating across execution environments.
Where Spearbit’s Researchers Add Value
Symbiotic gives protocols the freedom to define validator coordination. Teams can tailor slashing, rewards, and inclusion rules to fit their specific network needs. That flexibility creates a valuable opportunity to shape validator incentives and trust assumptions with clarity.
Spearbit works with teams at this stage to turn those decisions into secure, well-scoped implementations. Our researchers bring deep experience in modular staking and multi-network coordination. We help organizations ensure their vaults, resolvers, and validator flows are aligned with the intended security model, so they can launch with confidence.
Conclusion
Projects building on Symbiotic are often designing for complex, multi-network coordination - whether for rollups, AVSes, or DA layers. That flexibility comes with important design decisions around vaults, resolvers, and validator incentives. These choices shape how trust and enforcement operate across services.
Spearbit’s researchers work alongside organizations to review these configurations, validate security assumptions, and stress-test edge cases. For protocols implementing Symbiotic, our role is to help ensure your architecture aligns with your trust model, before launch, and as you scale.
Sources
FAQs
1. What is Symbiotic’s Universal Staking model?
Symbiotic’s Universal Staking is a permissionless framework for delegating ERC-20 tokens across networks. It allows protocols to define validator coordination, slashing logic, and reward distribution without relying on a centralized validator set.
2. How do vaults work in Symbiotic?
Vaults are configurable modules where curators define accepted collateral, slashing conditions, and reward mechanisms. Stake is tracked via internal accounting, and vaults can be reused across services, allowing protocols to isolate validator behavior per integration.
3. What role do resolvers play in Symbiotic?
Resolvers are on-chain or off-chain entities responsible for validating or vetoing slashing actions. A vault can use one or more resolvers, and slashing is only executed if quorum thresholds are met, enabling customizable dispute handling.
4. Can operators choose which networks to validate in Symbiotic?
Yes. Operators register on-chain and opt into specific vault-network pairs. This scoped participation model gives validators control over where they operate, allowing protocols to select operators based on specific technical or economic criteria.
5. How can Spearbit support teams using Symbiotic?
Spearbit’s elite researchers assist teams in reviewing vault configurations, validator incentive models, and slashing enforcement logic. Their expertise supports protocols integrating with Symbiotic to reduce validator risk and strengthen modular staking design.