Move-based platforms like Sui and Aptos provide developers with structural primitives that demand architectural clarity. These frameworks require developers to embed authority, control, and governance within the very definition of a token. Issuance is not a cosmetic act; it is a binding declaration of logic, ownership, and enforcement.
Deny List Enforcement and Epoch Timing in Sui
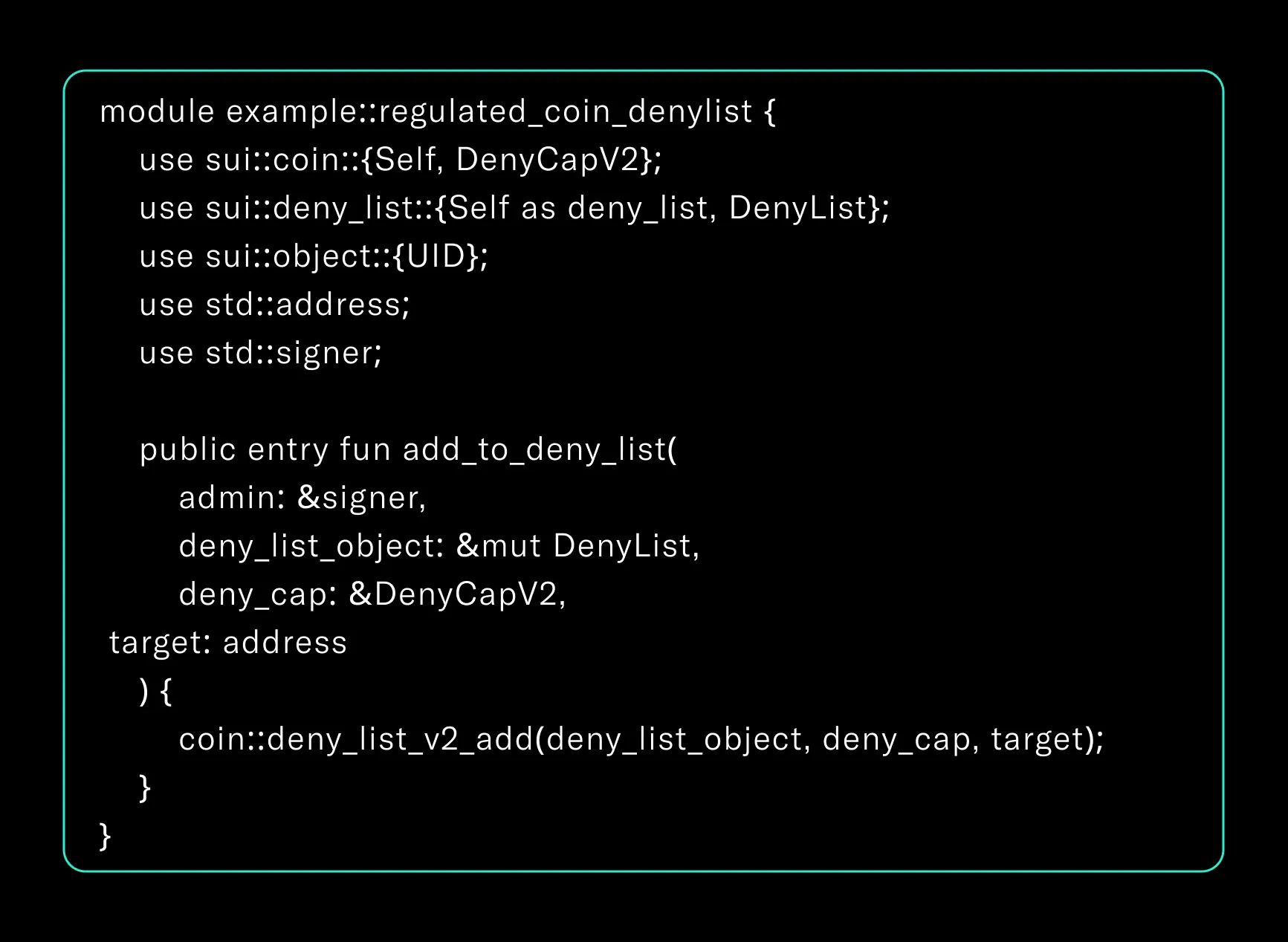
Sui introduces regulated coins via create_regulated_currency_v2, which produces both a TreasuryCap and a DenyCapV2. The latter is a capability object that allows the bearer to interact with a system-level singleton object, the DenyList located at address 0x403. This enables enforcement of blacklisting across the entire network.
The deny list governs access control over specific token types. Adding an address blocks its ability to use the coin as a transaction input. However, the propagation of this restriction is tied to Sui’s epoch model, which introduces a delay in full enforcement. Each epoch lasts approximately 24 hours.
Let’s walk through an example.
Scenario: Blocking an Address Mid-Epoch
Alice is a user holding USD_REG, a regulated stablecoin implemented via the sui::coin module. The admin of USD_REG decides to block Alice due to suspicious activity.
Immediate Outcome:
- Alice cannot send USD_REG anymore.
- She can still receive it from others until the end of the current epoch.
After the Next Epoch Starts:
- Alice can neither send nor receive USD_REG.
- Her balance remains, but any attempt to use or transfer it will fail at the protocol level.
This timing nuance must be understood when designing slashing systems, custodial controls, or real-time compliance engines. Without proper coordination, enforcement might lag behind event detection.
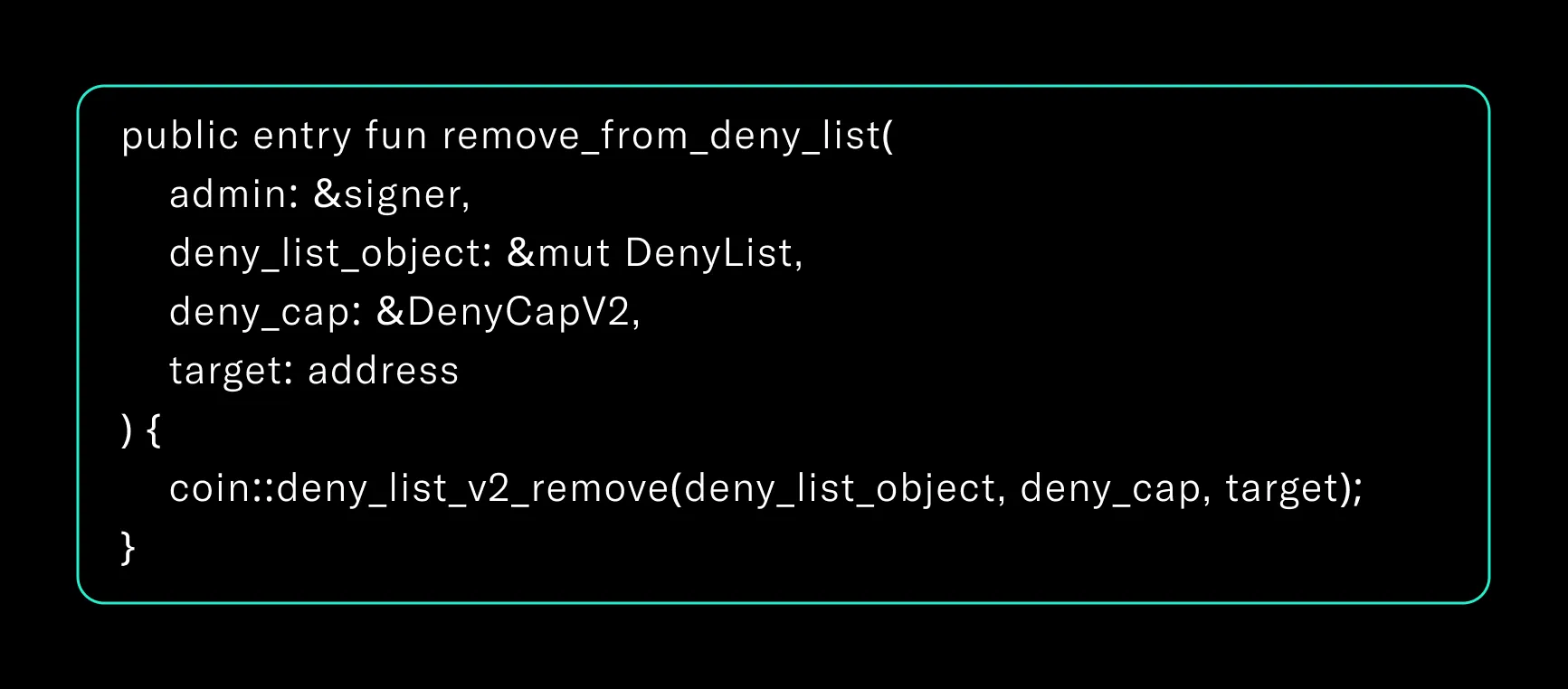
Unblocking an Address
Post-removal Behavior:
- Alice can receive coins immediately.
- She cannot send them until the next epoch begins.
TypeScript Integration
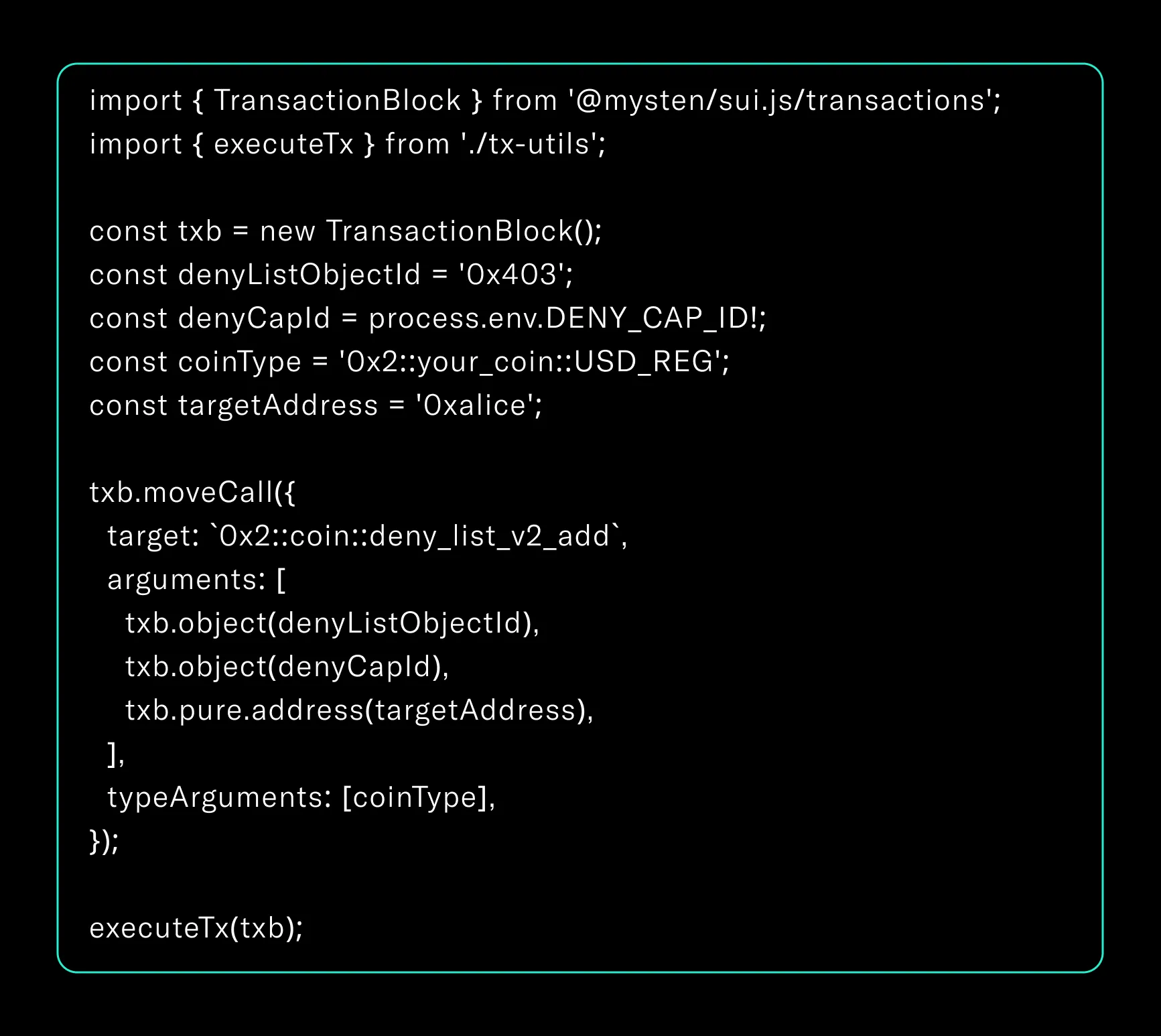
These two-phase transitions form the core enforcement model for regulated coins. They are neither instantaneous nor ambiguous. Developers must account for these propagation windows when building real-time apps or integrating Sui into external compliance workflows.
Capability Integrity and Escrow Transfer
Because enforcement is tied to DenyCapV2, access control over this capability object defines the trust boundary. If DenyCapV2 is lost, exposed, or held by a single signer without on-chain governance, blacklist functionality becomes a centralized kill switch.

Reviews must verify:
- Where DenyCapV2 is stored
- How access is controlled
- Whether rotation or delegation is possible
- What backup access paths exist
Any regulatory token contract without these controls is at systemic risk. A compromised admin key can irrevocably freeze or unfreeze participants without oversight or recourse.
Developer Takeaways
- Treat epoch-based enforcement as part of your system design.
- Plan event handling and UI feedback around propagation delays.
- Protect capability objects under multisig or governance modules.
- Explicitly model what happens between action initiation and enforcement.
Programmable Token Policies and ActionRequest in Sui
Sui’s token module allows the creation of programmable, closed-loop tokens with granular rules. These rules are enforced through TokenPolicy objects and their accompanying TokenPolicyCap capabilities. All protected actions like transfer, spend, or to_coin, emit an ActionRequest<T> object that must be validated.
This pattern enforces transaction discipline by requiring an ActionRequest<T> to be consumed immediately in the same transaction.

Example: Whitelisting Rule
Developers can attach rule logic to the policy to gate access:
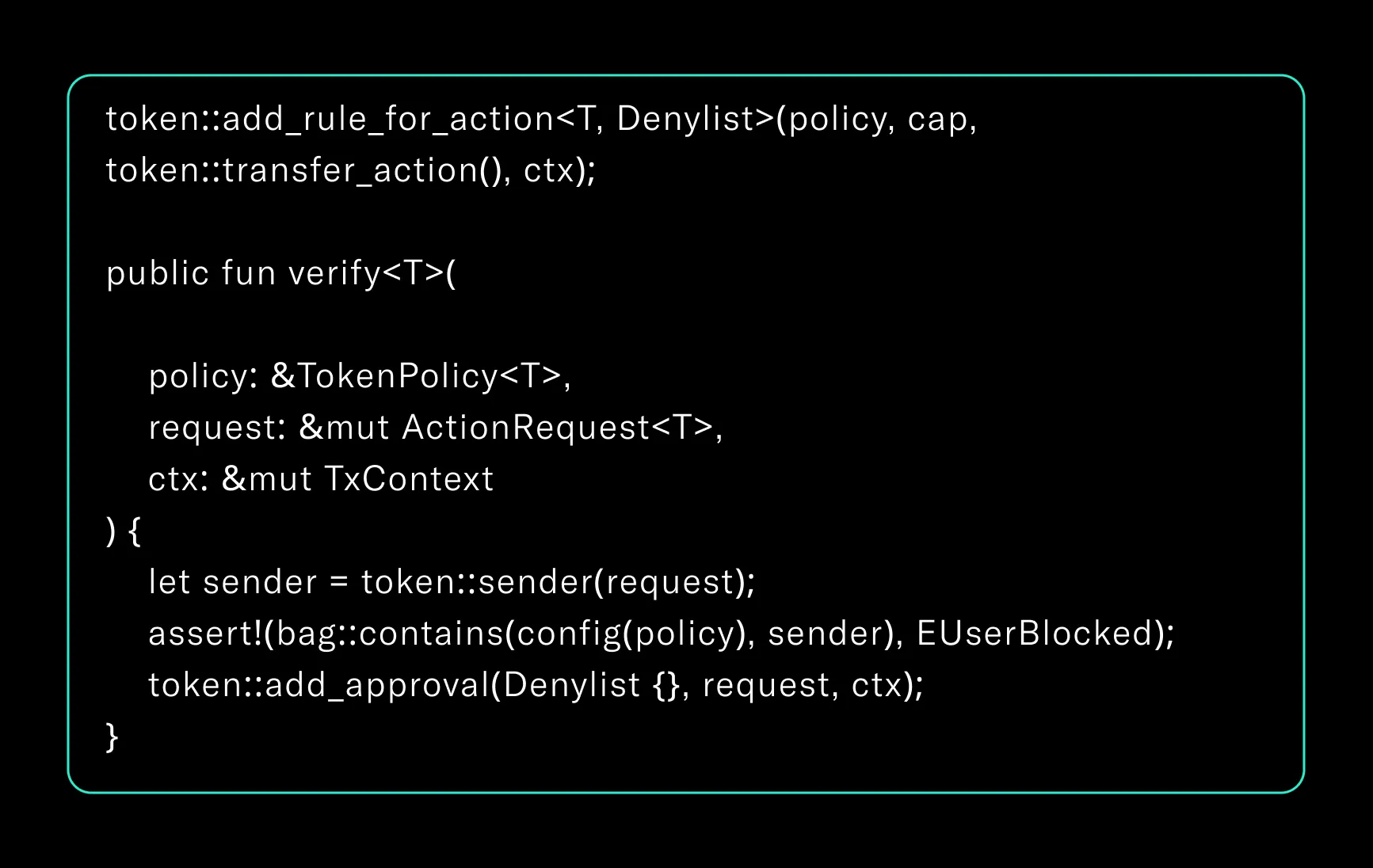
Rules like these allow developers to enforce transfer gating, max limits, role-based access, or other custom logic.
Dispatchable Logic and Hook Registration in Aptos
Aptos introduces a hook-based extension mechanism via the FA standard. The register_dispatch_functions API allows developers to override withdraw, deposit, and supply logic.
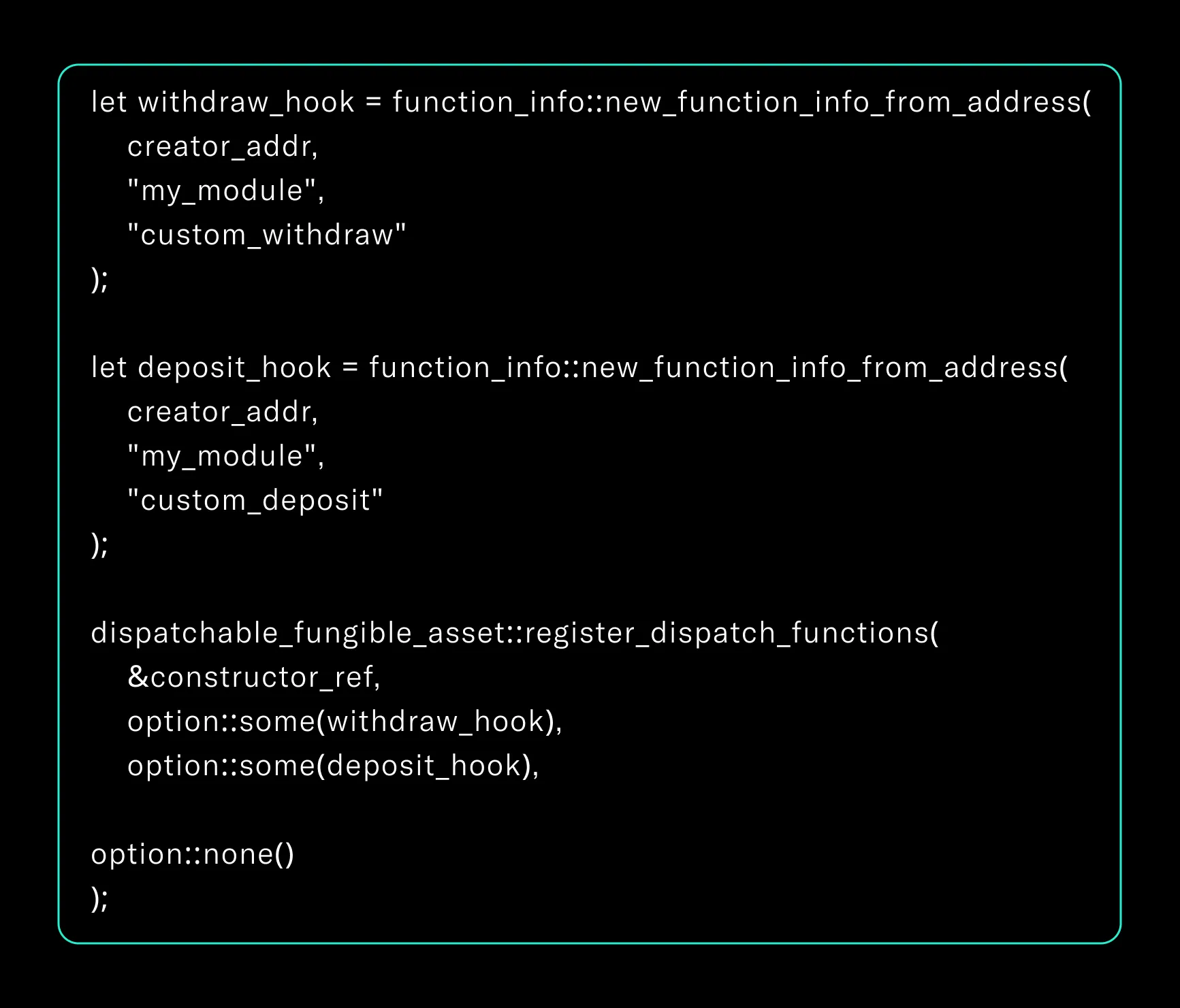
These functions replace default behavior and become mandatory pathways for all token movement. Developers can implement tax logic, multi-party confirmation flows, or regulatory checks.
Example: Deposit Hook With Fee
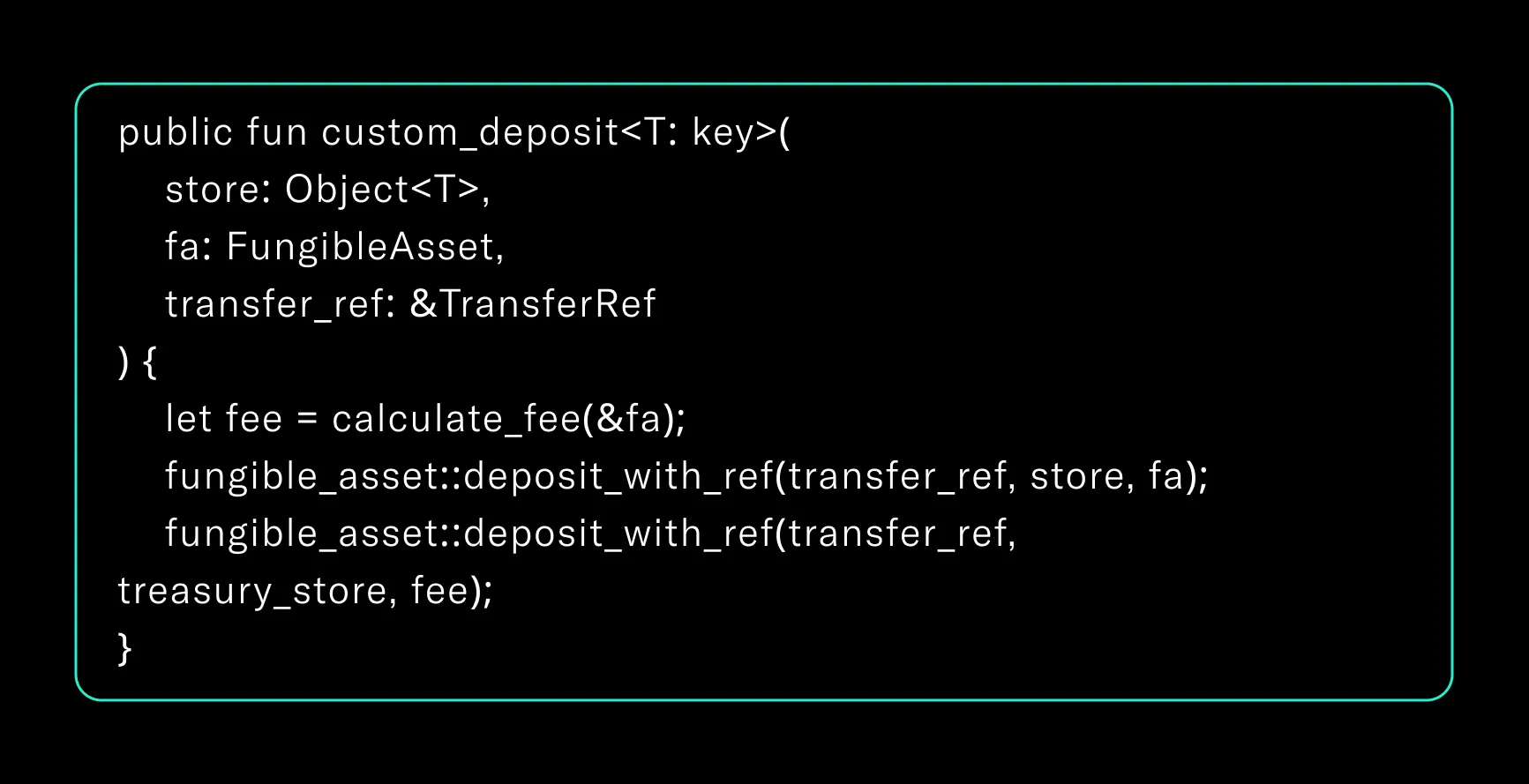
Developer challenges and Reviewing Paths
- Hooks must be registered during asset creation. They cannot be altered afterward.
- Fallback logic must be accounted for, what happens if a hook fails?
- Custom logic must avoid reentrancy and avoid invoking default behavior.
- Capability Refs (e.g., TransferRef) must be properly escrowed, or a single actor can arbitrarily freeze, unfreeze, or bypass restrictions.
These patterns form the backbone of compliant, extensible fungible token design on Aptos.
Move-based ecosystems introduce architectural primitives that demand deliberate design. Token contracts must define clear enforcement logic, control flows, and capability transitions. Each lifecycle event should reflect a consciously constructed trust boundary. At Spearbit, we conduct every high-signal review with the rigor of a protocol review. We identify authority paths, validate execution constraints, and surface edge cases others overlook.
If you're building on Move and require deep architectural analysis, get in touch with us. Our elite researchers are ready to help you launch with confidence.